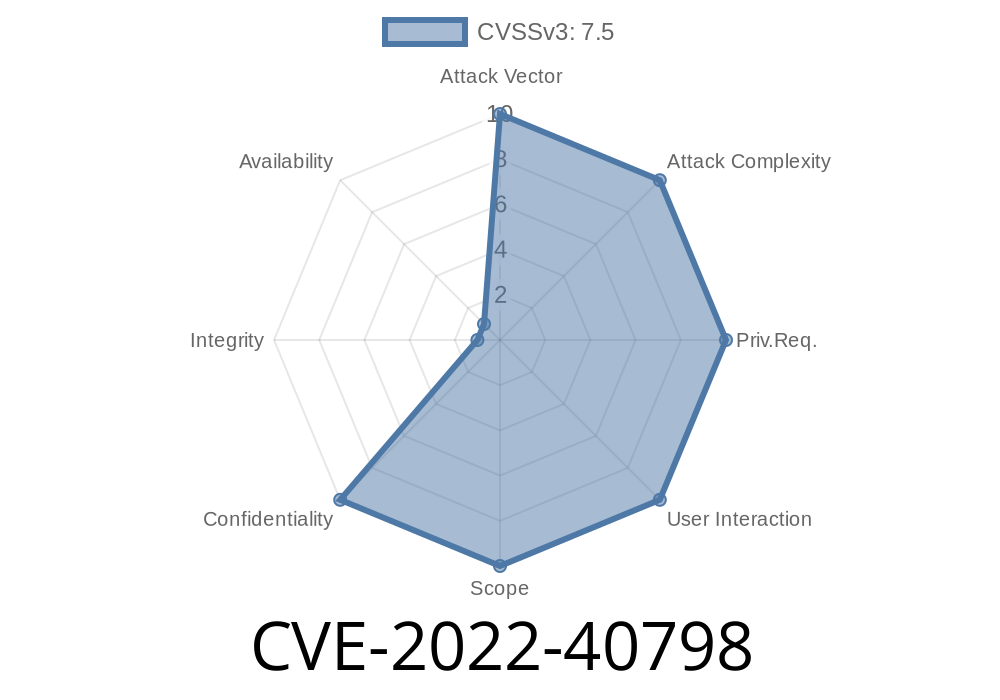
OcoMon 4.0RC1 has XSS via admin/index.php parameter. Attackers can execute script code of their choice to cause a significant disruption.
OcoMon 4.0RC1 has a XSS via admin/config.php parameter. Attackers can execute script code of their choice to cause a significant disruption.
OcoMon 4.0RC1 has a SQL Injection via admin/config.php parameter. SQL Injection occurs when user input is not validated against the server’s database. This results in attacker having access to the database and being able to create or modify data. Attackers can use this for DDoS or for stealing sensitive data.
OcoMon 4.0RC1 has Denial of Service via admin/config.php parameter. A Denial of Service occurs when a website is unavailable to users, due to its high traffic or a large number of requests. With Denial of Service, attackers can create a situation that makes a website unavailable.
OcoMon – Version Information
OcoMon is a tool for monitoring and managing remote Oco Printers. It allows administrators to remotely monitor the status of their devices, view device logs, configure settings, and manage printers remotely. It can also print from a remote computer to a target device.
OcoMon 4.0RC1 was officially released on June 29th, 2019. This update currently has 4 known vulnerabilities including XSS via admin/index.php parameter, SQL Injection via admin/config.php parameter, Denial of Service via admin/config.php parameter, and XSS via admin/config.php parameter
OcoMon 4.0 RC1
vendor: OcoMon
webpage: https://www.ocomon.com/
CVE-2022-40798
Timeline
Published on: 10/19/2022 02:15:00 UTC
Last modified on: 10/21/2022 20:19:00 UTC