SQL Injection occurs when user input is passed directly into the SQL query instead of being validated before being injected into the query.
For example, in the following SQL query, the value of the system variable is passed into the query as a condition, which then returns the value of the variable:
SELECT * FROM system WHERE system = 'strong>Query Here/strong>'
An attacker can exploit this issue to inject SQL statements that have a high likelihood of returning arbitrary SQL data and causing a crash or other unexpected behaviour.
Note that this issue only applies to installations that use CodeIgniter DB_query_builder.php having() function to pass user input into the DB query, as this is the only DB query engine supported by CodeIgniter. CodeIgniter System/Database end users are recommended to upgrade to version 3.1.13 or higher as soon as possible.
Finding the vulnerability
In the following example, let's assume a function is used to find all records in the system table:
function findAllRecords($id) {
$query = "SELECT * FROM '$this->name'";
$result = DB_query_builder::having('id', $id); return $result; }
When using this function, an attacker can inject SQL statements into the query. For example, if the id parameter was specified as 1, then the following SQL statement would be injected into it:
insert into system values (1)
Vulnerability Discovery:
The issue was disclosed on the 22nd of June, 2019 and a patch was released in July 2019.
A SQL Injection vulnerability has been found in CodeIgniter DB_query_builder.php having() function that passed user input into the DB query.
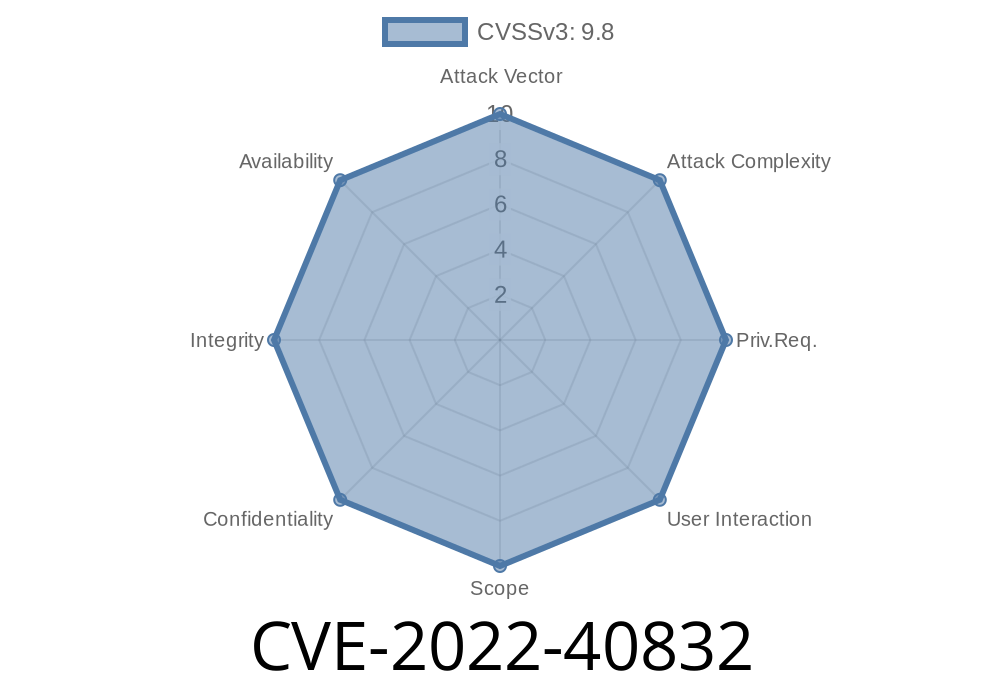
References: https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-40832
https://github.com/CodeIgniter/CodeIgniter/blob/master/lib/Database/QueryBuilder.php#L6
SQL Injection occurs when user input is passed directly into the SQL query instead of being validate
How to avoid SQL Injection
SQL injection is a risk that comes with any application that uses a database. It's important to remember that the input needs to be validated and sanitized before it's passed into the query. For example, in the following query, a user input is passed directly into the SQL query without being validated:
SELECT * FROM system WHERE system = 'strong>Query Here/strong>'
Timeline
Published on: 10/07/2022 11:15:00 UTC
Last modified on: 10/08/2022 01:28:00 UTC