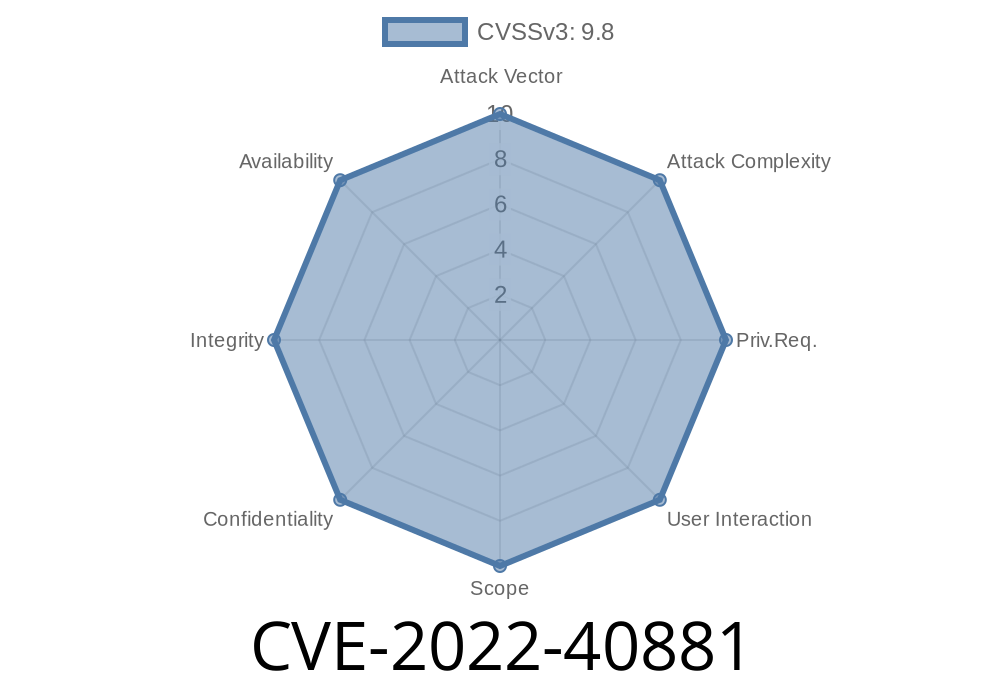
A user could inject commands into the server and execute arbitrary code as the root user. An attacker could exploit this to obtain access to critical systems or devices, or even hijack the session of a logged-in user. This is a critical issue, as it is possible to create a malicious profile on any SolarWinds system and inject commands, leading to a wide range of potential threats. SolarWinds recommends the following actions: Users are encouraged to update to version 6.10.7181 or higher.
Users are encouraged to change the default server password for network_test.php.
Users are encouraged to disable the “Run Profile Tests” functionality, as this functionality is vulnerable to command injection.
Users are encouraged to change the default password for the “admin” user.
Users are encouraged to disable the “Run Profile Tests” functionality, as this functionality is vulnerable to command injection.
Solution outlining how each company will provide assistance to their users
SolarWinds: The company will provide a manual of best practices to prevent the attack (https://support.solarwinds.com/hc/en-us/articles/36000764108). They will also release an update that fixes the vulnerability and removes the functionality that is vulnerable to command injection (https://www.solarwinds.com/blog/update-for-critical-vulnerability-in-network_test.php).
Other Important Information
The CVE-2022-40881 vulnerability has been fixed with SolarWinds version 6.10.7181 and higher.
SolarWinds Products Affected by This Vulnerability
This Vulnerability affects the following products:
SolarWinds Network Performance Monitor
SolarWinds Server & Application Monitor
Timeline
Published on: 11/17/2022 04:15:00 UTC
Last modified on: 11/18/2022 18:54:00 UTC