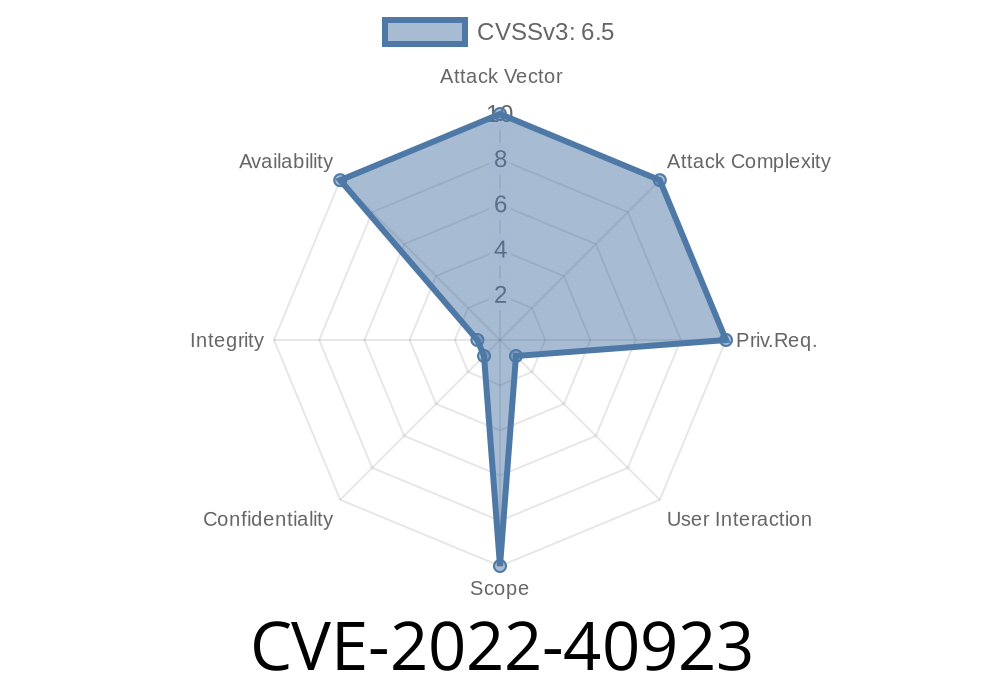
An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code. A vulnerability in the LIEF::MachO::SegmentCommand function of LIEF v0.12.1 allows attackers to cause a denial of service (DOS) through a segmentation fault via a crafted MachO file. An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code. An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code. An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code. An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic”
Summary
An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code.
Vulnerability overview
An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code. The vulnerability occurs when handling segmented MachO files. An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code.
An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code
MD5 hash function
The MD5 hash function creates a 128-bit hexadecimal number representing the message digest of data. The MD5 hash function is widely implemented, but collisions have been discovered which make it impractical to use for security purposes. An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code.
Bounds Check Bypass in LIEF::MachO::SegmentCommand
An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code. A vulnerability in the LIEF::MachO::SegmentCommand function of LIEF v0.12.1 allows attackers to cause a denial of service (DOS) through a segmentation fault via a crafted MachO file. An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code. A vulnerability in the LIEF::MachO::SegmentCommand function of LIEF v0.12.1 allows attackers to cause a denial of service (DOS) through a segmentation fault via a crafted MachO file. An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code
Vulnerability description - CVE-2022-40924
A vulnerability in the LIEF::MachO::SegmentCommand function of LIEF v0.12.1 allows attackers to cause a denial of service (DOS) through a segmentation fault via a crafted MachO file. An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code.
An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code. An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code. An attacker can create a file in the “native” format (aka “.n”) and then convert this file to the “dynamic” format (aka “.dylib”) to bypass protections and execute arbitrary code.
Timeline
Published on: 09/30/2022 19:15:00 UTC
Last modified on: 10/05/2022 15:46:00 UTC