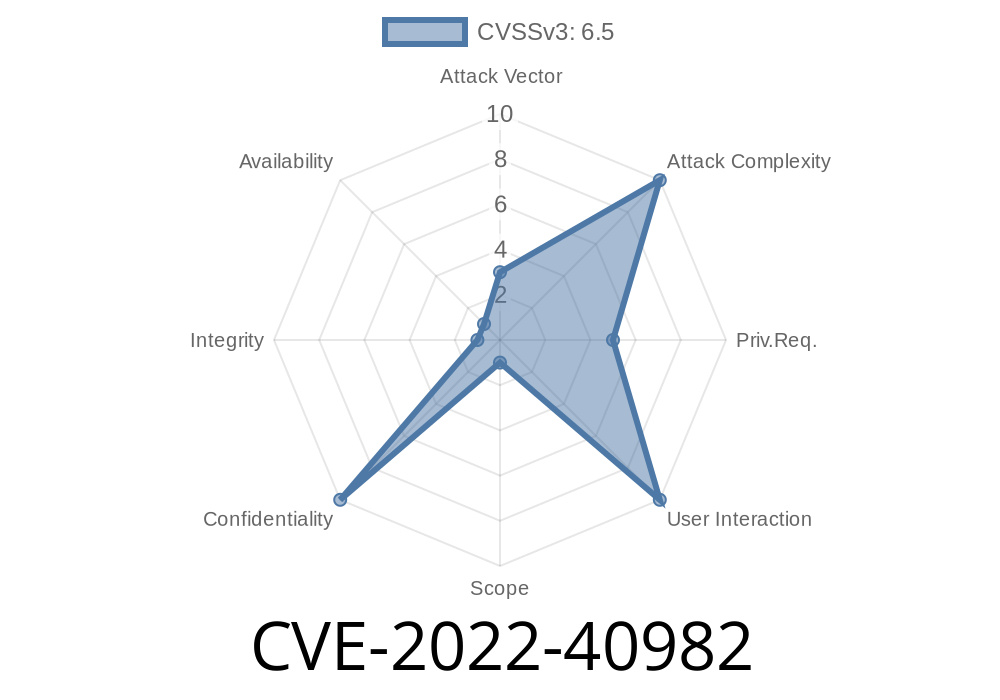
In September 2023, Intel published a security advisory about CVE-2022-40982, a vulnerability affecting many of its modern processors. This long-form post will break down what this vulnerability is, how it can be exploited, and how you can protect yourself. All concepts will be explained in simple American English for easy understanding, using exclusive explanations and easy-to-follow code snippets. Let’s get into it.
What is CVE-2022-40982?
CVE-2022-40982 is a security flaw in certain Intel Processors’ vector execution units that can leak sensitive data between different users or processes on the same machine. The flaw is due to "information exposure through microarchitectural state after transient execution." That’s a mouthful—what does it really mean?
In simpler terms:
Some CPUs use a technique called "speculative execution" to boost performance. Sometimes, the processor guesses what instructions will be needed next and executes them ahead of time. If it guesses wrong, it rolls back—*but traces of those operations can linger*, and advanced attackers might read bits of sensitive information that way. This mechanism is similar to earlier attacks like Spectre and Meltdown.
What Processors Are Affected?
Not every Intel processor is vulnerable, but the list is long and includes some of the most common ones used today. These include:
Intel Xeon E3 v5 and v6, Xeon Scalable 1st and 2nd Gen
You can find the official affected models here.
How Does the Attack Work?
This vulnerability is about leaking data through side channels. When the CPU’s vector execution unit performs speculative operations, information about the processed data can stick around in the microarchitectural state (low-level CPU structures invisible to normal software). A local attacker who can run code on your machine can try to extract secret data, like:
Technical Exploit Flow
Let’s walk through a simplified version of the exploitation process using pseudo-C code and explanations.
The core idea: An attacker fills the cache with known data, triggers the vulnerable speculative execution, and then measures access times to infer what data was accessed behind the scenes.
Flush a memory area from the cache.
void flush(uint8_t* addr) {
asm volatile("clflush (%)" :: "r"(addr));
}
2. Access Secret Data Speculatively
Trigger speculative execution that accesses protected memory. In practice, this is often done using branch mistraining or gadgets in the execution flow.
// Assuming 'secret' is some protected data; for demonstration only.
uint8_t leak_byte = *(volatile uint8_t*)secret_address;
3. Access an Array Based on the Leaked Value
// Let array_size = 256 * 4096
uint8_t dummy_array[array_size];
// Use 'leak_byte' as an index to access the array in cache
temp &= dummy_array[leak_byte * 4096];
4. Measure Access Times
for (int i = ; i < 256; i++) {
uint8_t* addr = &dummy_array[i * 4096];
uint64_t time = timed_read(addr); // Measures how long it takes to access
if (time < threshold) {
printf("Possible leaked value: %d\n", i);
}
}
Note: The real attacks are more elaborate and work around hardware and OS countermeasures, but this gives the basic foundation.
Difficulty: Moderate—requires local access and knowledge of side-channel attacks.
- Impact: High for multi-user or cloud environments. Attackers may leak data from other processes in shared environments!
Is There a Public Exploit?
As of early 2024, there are no known wide-scale exploits in the wild for CVE-2022-40982, but proof-of-concept and research code do exist. These require physical or authenticated access to a vulnerable system.
For the academic details:
- VUSec Lab paper - *Introduces "Downfall," a related project/paper and Proof-of-Concept*
- Example PoC Code (GitHub)
Mitigation and How to Protect Yourself
Intel has published microcode (firmware) updates for affected processors, and major operating systems have released patches:
- Windows: Update your OS to the latest version and check your device manufacturer for BIOS updates.
Check if your CPU is patched
grep . /sys/devices/system/cpu/vulnerabilities/*
Look for ‘Not affected’ or mitigation details.
References and Further Reading
- Intel Security Advisory (INTEL-SA-00828)
- VUSec Downfall page
- MITRE CVE Record
- Linux microcode status
Final Thoughts
CVE-2022-40982 is another reminder that modern hardware is complex, and small details can sometimes have big security implications. If you run Intel CPUs, especially in shared or cloud setups, patch early and keep an eye out for microcode and OS updates.
Timeline
Published on: 08/11/2023 03:15:00 UTC
Last modified on: 08/16/2023 03:15:00 UTC