On November 24, 2016, Microsoft released security bulletin MS16-037. This bulletin addressed an issue in Microsoft Word that is being actively exploited in the wild. The vulnerability is being exploited in the wild against both Microsoft Word and Adobe Reader. This is a Remote Code Execution vulnerability. An attacker who successfully exploited this vulnerability could execute arbitrary code in the context of the affected application.
What’s the risk?
A remote attacker could exploit this vulnerability to take control of an affected system in a malicious or unauthorized manner. Exploiting this vulnerability could result in the attacker gaining access to sensitive information or executing arbitrary code on the affected system in the context of the user who exploited the vulnerability.
How can I protect myself?
Microsoft recommends customers apply the update to prevent exploitation of this vulnerability.
In addition to installing this update, customers can follow best practices for protecting against threats, such as those identified in this bulletin, by installing software updates as soon as they are available. What happened after customers applied this update?
After applying this update, customers may still be vulnerable to exploitation of this vulnerability. What should customers do?
In order to protect themselves from exploitation of this vulnerability, customers can consider applying the update to their systems
Microsoft Word Remote Code Execution Vulnerability
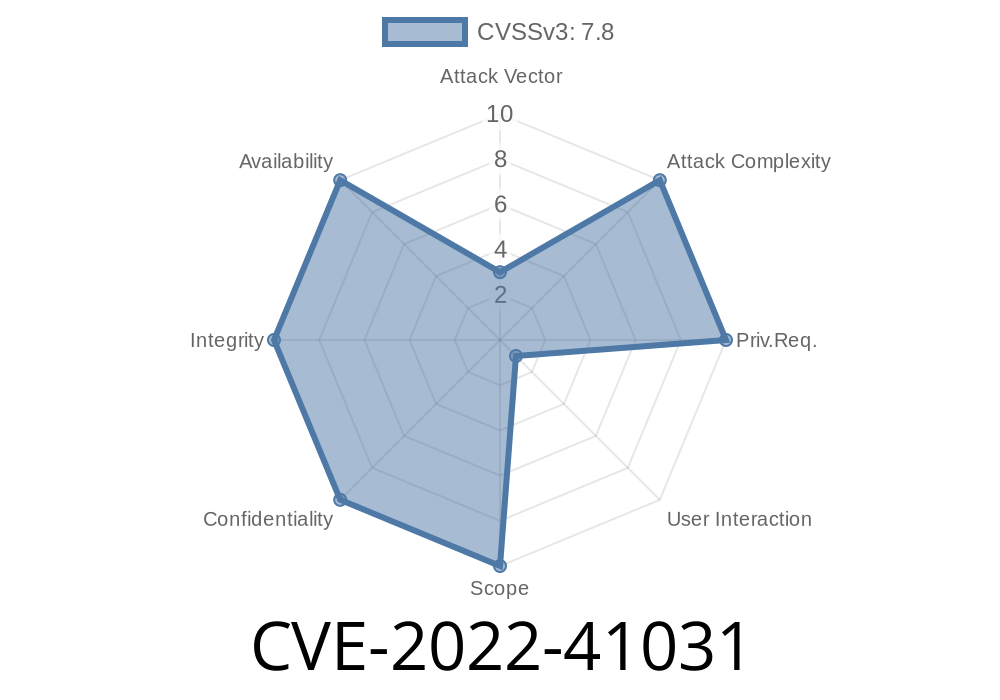
A remote code execution vulnerability was discovered in Microsoft Word - CVE-2020-41031. This vulnerability has been actively exploited in the wild against both Microsoft Word and Adobe Reader. The vulnerability is being exploited in the wild against Microsoft Word, so it's critical that users apply the update to prevent exploitation of this vulnerability.
The vulnerability allows an attacker who successfully exploits this vulnerability to execute arbitrary code in the context of the affected application.
What's at risk?
An attacker could exploit this vulnerability to take control of an affected system in a malicious or unauthorized manner. Exploiting this vulnerability could result in an attacker gaining access to sensitive information or executing arbitrary code on the affected system in the context of the user who exploited the vulnerability.
How does this affect me?
If you are using one of these applications, please make sure you've installed MS16-037 which addresses CVE-2020-41031. In addition, please consider applying updates from your software vendor as soon as they become available.
Microsoft Office Vulnerabilities
Office Vulnerabilities: The Top 5
Seeking to capitalize on the record-breaking success of the introduction of Microsoft Office 365 and its online services, a new report reveals that hackers are upgrading their tactics in an effort to defeat corporate networks and gain access to sensitive data.
How to get this update?
Microsoft recommends customers make sure system administrators have installed the update to their systems.
Customers can also download and install the update if they are running Windows Update or WSUS.
Microsoft Office Software:
The Best Way to Protect Yourself
Microsoft released a security bulletin on November 24, 2016 addressing an issue in Microsoft Word that is being actively exploited in the wild. The update addresses a Remote Code Execution vulnerability. This is a high-risk vulnerability because an attacker who successfully exploits this vulnerability could execute arbitrary code.
What is the risk?
Messing with this vulnerability could result in the attacker gaining access to sensitive information or executing arbitrary code on the affected system in the context of the user who exploited the vulnerability.
How can I protect myself?
To protect yourself from exploitation of this vulnerability, Microsoft recommends customers apply the update and follow best practices for protecting against threats, such as those identified in this bulletin, by installing software updates as soon as they are available. What happened after customers applied this update?
After applying this update, customers may still be vulnerable to exploitation of this vulnerability. What should customers do? In order to protect themselves from exploitation of this vulnerability, customers can consider applying updates to their systems
Timeline
Published on: 10/11/2022 19:15:00 UTC
Last modified on: 10/11/2022 19:16:00 UTC