In September 2022, Microsoft patched several security flaws in the Windows Point-to-Point Tunneling Protocol (PPTP). One critical bug, known as CVE-2022-41039, enables remote code execution—meaning an attacker could potentially run commands remotely just by exploiting the way PPTP handles network traffic.
If you work with Windows environments or are responsible for network security, it’s important to understand this vulnerability, how it works, and what you can do to protect your systems. In this article, we'll break down CVE-2022-41039 in plain language, explain how the exploit works, touch on detection and available patches, and compare it to related vulnerabilities. This read is for learning and awareness only.
What Is Windows PPTP?
The Point-to-Point Tunneling Protocol (PPTP) is a VPN protocol that lets computers communicate securely over the internet by creating encrypted "tunnels" for data. It's considered outdated and less secure than newer protocols, but it’s still present in many Windows systems for backward compatibility.
What Is CVE-2022-41039?
According to the Microsoft Security Update Guide (MSUG):
> *“A remote code execution vulnerability exists in Windows Point-to-Point Tunneling Protocol. An attacker who successfully exploited this vulnerability could run arbitrary code on the affected system.”*
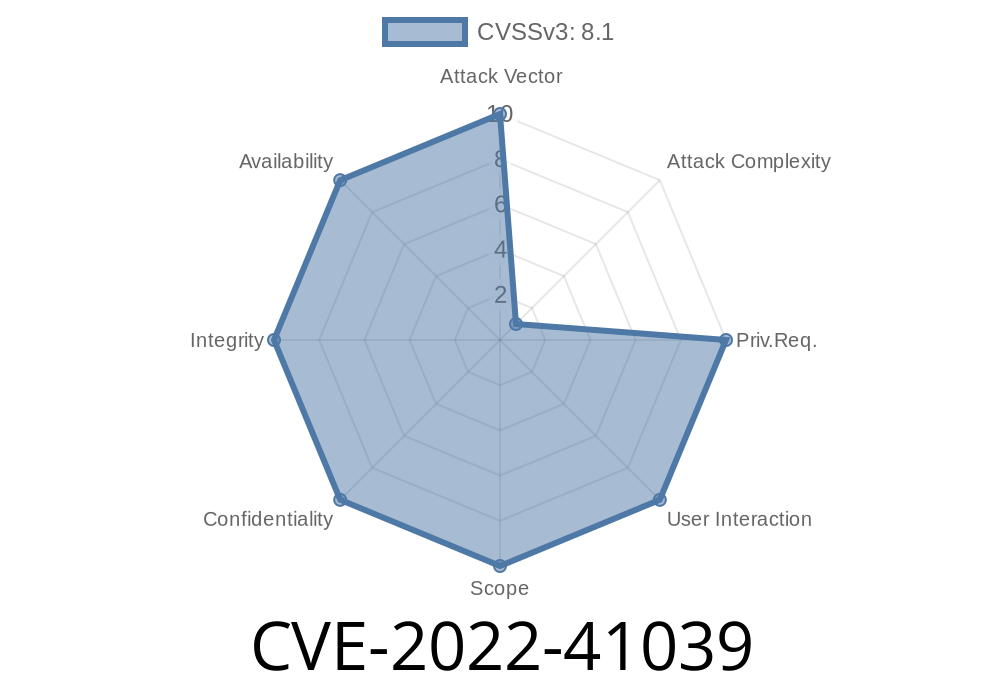
Severity: Critical
CVSS Score: 8.1 (High)
Exploitable Remotely: Yes
Authentication Required: No
How Does the Vulnerability Work?
This bug is found in the way Windows PPTP processes specially crafted data packets during a VPN handshake. If an attacker sends a maliciously crafted PPTP packet to a vulnerable Windows server or client, they could trigger a memory corruption, giving them the opportunity to execute arbitrary code with the system's privileges.
*The attacker does not need any authentication to launch the attack—they just need the ability to send packets to the PPTP service.*
Technical Breakdown
- The vulnerability occurs before authentication, during the parsing of specific PPTP control messages.
By sending malformed Control Message packets, attackers can exploit a buffer overflow.
- Successful exploitation can lead to code running on the system as the local user, or worse, as SYSTEM.
Example Exploit Flow
> *Below is a conceptual Python snippet showing how an attacker might connect to a PPTP server and send a malformed message. This is for educational purposes only—never run test code against systems you do not own!*
import socket
target_ip = "VICTIM_IP"
pptp_port = 1723
# Malformed PPTP control message (example, not a weaponized payload)
malformed_packet = b'\x1a\x2b\x00\x00' + b'A' * 512 # Overly long payload
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_ip, pptp_port))
sock.send(malformed_packet)
data = sock.recv(1024)
print(data)
sock.close()
*Actual weaponized code would require reverse engineering the exact memory handling flaw in the Windows PPTP implementation.*
No. CVE-2022-41039 is unique. Other similar PPTP vulnerabilities published in late 2022 include
- CVE-2022-41044 (MSUG link): Different RCE in PPTP, triggered by a separate parsing error.
- CVE-2022-41088 (MSUG link): Yet another RCE with a distinct exploit path.
Each CVE targets a different flaw in how Windows PPTP processes packets, but all allow for dangerous code execution if unpatched.
Who Is at Risk?
- Windows servers/clients with PPTP enabled and accessible from untrusted networks
What You Should Do
- Patch: Immediately apply Microsoft’s security update for CVE-2022-41039 (released September 2022).
- Disable PPTP: If possible, turn off PPTP on your servers and clients. Switch to modern VPN protocols like L2TP/IPSec, SSTP, or OpenVPN.
- Block PPTP Ports: At the network perimeter, block TCP port 1723 (the PPTP port) if you do not need it.
- Monitor Logs: Look for abnormal incoming connections on port 1723 and repeated failed handshakes.
Here's how you might disable PPTP server in Windows
# Open Routing and Remote Access snap-in
# Or, disable the RRAS service entirely if not needed
Stop-Service RemoteAccess
Set-Service RemoteAccess -StartupType Disabled
References & Further Reading
- Microsoft Security Update Guide: CVE-2022-41039
- Microsoft Patch Tuesday September 2022
- Common PPTP VPN Vulnerabilities
- Wikipedia: Point-to-Point Tunneling Protocol
Final Thoughts
CVE-2022-41039 is a harsh reminder that legacy protocols like PPTP still pose real risks if left enabled. This bug makes it trivial for attackers to execute code remotely—no password needed. Patch fast, disable legacy services, and always use current security best practices.
*Stay secure, and always check your perimeter for outdated services!*
Timeline
Published on: 11/09/2022 22:15:00 UTC
Last modified on: 11/10/2022 00:33:00 UTC