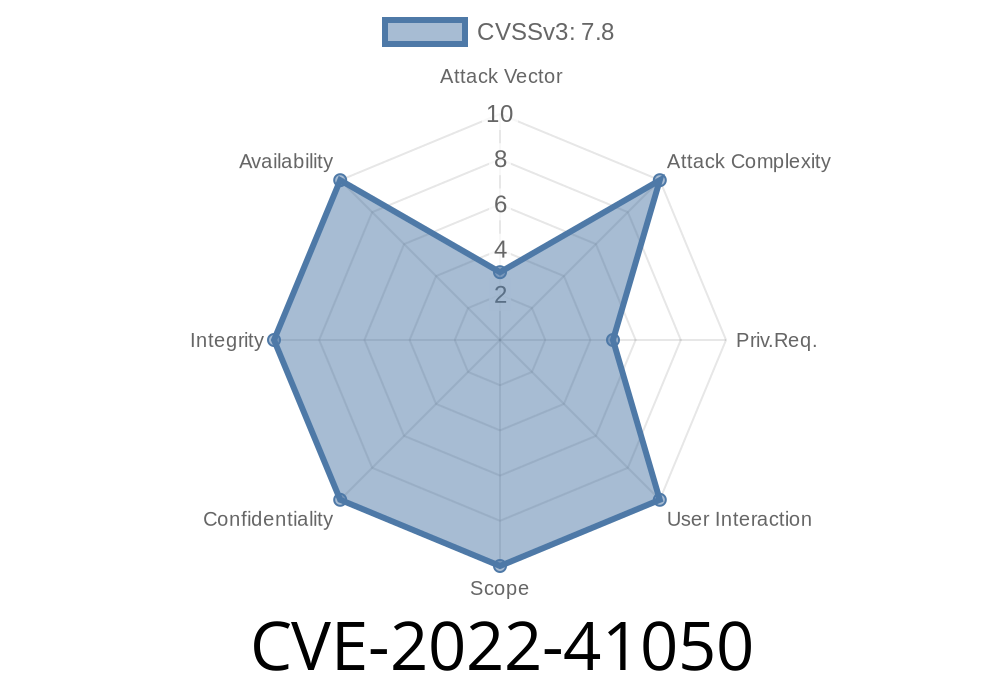
This issue is due to the improper sanitization of user input. An attacker can exploit this vulnerability by crafting a malicious file to embed in a document. When the user opens the document, the embedded script runs with elevated privileges, allowing the attacker to run code with elevated privileges on the victim’s system. Microsoft Windows Server versions that are affected are Windows Server 2008, Windows Server 2012, and Windows Server 2016. Windows version that are affected are Windows 7, Windows 8, Windows 8.1, and Windows 10. Microsoft released a security update for Exchange Server, which is superseded by this article. The following versions are affected: - Microsoft Exchange Server 2010 Service Pack 4 - Microsoft Exchange Server 2013 - Microsoft Exchange Server 2016 - Microsoft Exchange Server 2019 This issue is due to the improper sanitization of user input. An attacker can exploit this vulnerability by crafting a malicious file to embed in a document. When the user opens the document, the embedded script runs with elevated privileges, allowing the attacker to run code with elevated privileges on the victim’s system. Microsoft Windows Server versions that are affected are Windows Server 2008, Windows Server 2012, and Windows Server 2016. Windows version that are affected are Windows 7, Windows 8, Windows 8.1, and Windows 10. Microsoft released a security update for Exchange Server, which is superseded by this article
Microsoft Exchange Server 2010 Service Pack 4
- Microsoft Exchange Server 2013 - Microsoft Exchange Server 2016 - Microsoft Exchange Server 2019
This issue is due to the improper sanitization of user input. An attacker can exploit this vulnerability by crafting a malicious file to embed in a document. When the user opens the document, the embedded script runs with elevated privileges, allowing the attacker to run code with elevated privileges on the victim’s system. Microsoft Windows Server versions that are affected are Windows Server 2008, Windows Server 2012, and Windows Server 2016. Windows version that are affected are Windows 7, Windows 8, Windows 8.1, and Windows 10. Microsoft released a security update for Exchange Server, which is superseded by this article
Microsoft released a security update for Exchange Server, which is superseded by this article
Microsoft Exchange Server
The following versions are affected: - Microsoft Exchange Server 2010 Service Pack 4 - Microsoft Exchange Server 2013 - Microsoft Exchange Server 2016 - Microsoft Exchange Server 2019 This issue is due to the improper sanitization of user input. An attacker can exploit this vulnerability by crafting a malicious file to embed in a document. When the user opens the document, the embedded script runs with elevated privileges, allowing the attacker to run code with elevated privileges on the victim’s system. Microsoft Windows Server versions that are affected are Windows Server 2008, Windows Server 2012, and Windows Server 2016. Windows version that are affected are Windows 7, Windows 8, Windows 8.1, and Windows 10. Microsoft released a security update for Exchange Server, which is superseded by this article
Timeline
Published on: 11/09/2022 22:15:00 UTC