It has been discovered that Windows GDI+ component, that is responsible for rendering bitmap images, is prone to information disclosure vulnerabilities. A remote attacker can exploit these issues to get access to sensitive information on the affected system, including system settings, full disk encryption keys and other data. GDI+ is a part of Windows that is responsible for rendering bitmap images. It is used by Windows applications to display graphics on the screen. It is recommended to apply the appropriate updates to mitigate the risk related to this issue. End users can also monitor the system for signs of information disclosure and act accordingly. Google Chrome OS Vulnerability Sparks Critical Vulnerability in Windows. A critical vulnerability has been discovered in Windows operating system that is being actively exploited in the wild. It has been revealed that a critical remote code execution vulnerability has been discovered in Windows operating system. According to experts, this vulnerability is being actively exploited in the wild. It has been reported that hackers are injecting malicious code on targeted websites and injecting these malicious codes in the browser of the end users, which ultimately lead to the compromise of the targeted system. A Google Chrome OS user visiting a malicious website on the internet can be exploited by this vulnerability to compromise their computer
Internet Explorer Remote Code Execution Vulnerability
On Thursday, Microsoft issued a Security Advisory that included details of a critical remote code execution vulnerability in Internet Explorer. This issue is being actively exploited by hackers to carry out malicious attacks against the users. The flaw was discovered on Windows Server 2016 and Windows 10 systems running IE 11 in preview mode.
According to Microsoft, there are no reports of this vulnerability being exploited in the wild. It has also been reported that attackers are targeting a specific set of websites and injecting malicious code in the browser of the end users, which ultimately lead to their compromise.
What is Google Chrome OS?
Google Chrome OS is a Linux-based operating system that is mainly used to power Chromebooks. Google Chrome OS provides offline capabilities and relies on the cloud to generate its interface.
New Vulnerability in Windows: How Does It Work?
This vulnerability affects all versions of Windows operating system, including Windows 7 and 8. Microsoft has confirmed that the vulnerability is being actively exploited in the wild. This vulnerability is being exploited by hackers to inject malicious code on targeted websites and injecting these malicious codes in the browser of an end user, which ultimately lead to the compromise of the targeted system. An attacker can exploit this vulnerability on a victim's computer to gain remote access to sensitive information.
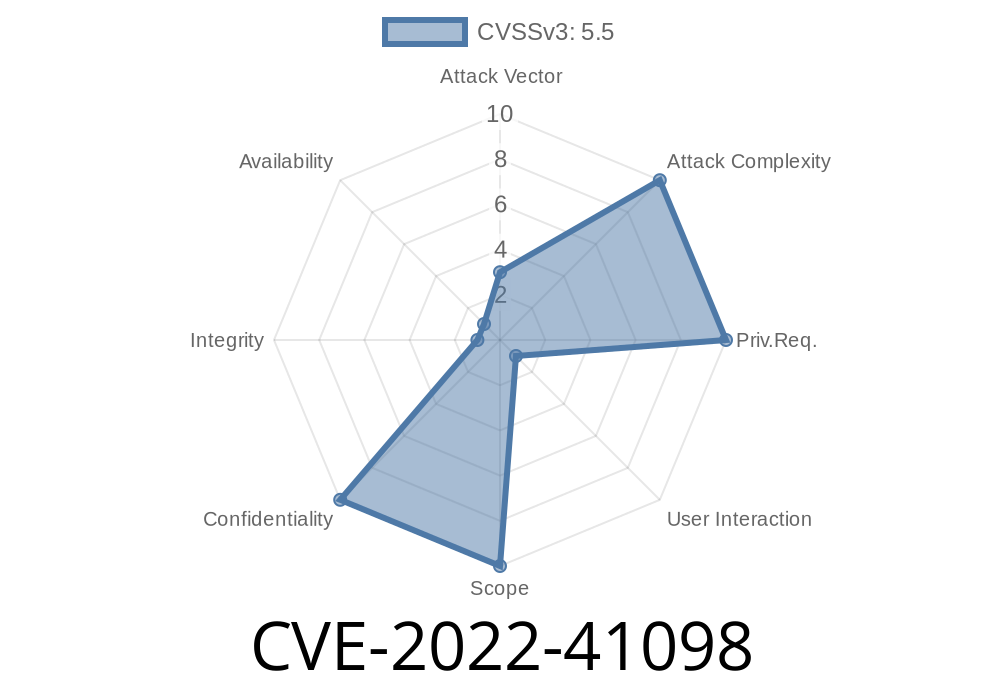
The details of the vulnerability are unknown, but it may be related to a previous issue that was discovered in GDI+. This issue was patched in Microsoft Security Advisory CVE-2022-41098 back in September 2017. The patch was applied automatically through Windows update as soon as it was released by Microsoft.
In order to mitigate this issue, all users should apply the appropriate updates from their respective vendors immediately. You can use Google Chrome or Mozilla Firefox web browsers to see if your computer has been compromised by this vulnerability or not. If your browser does not show any warning signs or you are using Internet Explorer for browsing, then it means that your computer has not been compromised so far. However, if you are using Netscape or AOL browsers for browsing, then you might have already been attacked by this threat
Vulnerability Details
A critical remote code execution vulnerability has been discovered in Windows operating system that is being actively exploited in the wild. It has been revealed that a critical remote code execution vulnerability has been discovered in Windows operating system. According to experts, this vulnerability is being actively exploited in the wild. The vulnerability can be exploited by a malicious website to inject malicious codes on targeted websites and injecting these malicious codes into the browser of the end user, which ultimately leads to their computer's compromise. This issue was discovered by Google Chrome OS Vulnerabilities Research Team and reported to Microsoft.
How Does Google Chrome OS Vulnerability Sparks Critical Vulnerability in Windows?
The vulnerability that has been discovered in Windows operating system, is being actively exploited in the wild. It has been revealed that a critical remote code execution vulnerability in Microsoft's Windows operating system allows hackers to execute malicious code on targeted websites and inject these malicious codes in the browser of the end users, which ultimately lead to the compromise of the targeted system. A Google Chrome OS user visiting a malicious website on the internet can be exploited by this vulnerability to compromise their computer systems and gain full control over them.
It is recommended for all Windows users to update their systems immediately as applicable patches have been released. Google Chrome OS Vulnerability Sparks Critical Vulnerability in Windows
Timeline
Published on: 11/09/2022 22:15:00 UTC
Last modified on: 11/10/2022 00:33:00 UTC