This is a critical security bug that is being actively exploited by attackers. It was discovered by FireEye researchers and the details of the bug have been published on the FireEye blog. This critical security bug can be exploited by an attacker to bypass the password protection on Windows operating system. As this is a critical security bug, it is highly recommended to upgrade your Windows OS to the latest version as soon as possible. Windows OS vendors have released patches for this bug. It is recommended to install these patches as soon as possible to prevent hacker attacks. How do hackers exploit this critical security bug? To understand this, let’s have a look at the code snippet given below. This is the code snippet where an attacker tries to open a file with a password protection. When the attacker tries to open a protected file, the exploited function in the code snippet gets executed.
Understanding the code snippet for understanding this bug
If (prop.IsProtected)
{
// Do not allow the file to be opened unless it is a .txt file by using its extension
if (extension=="txt")
return true;
How hackers exploit this critical Windows OS bug?
To exploit this critical Windows OS bug, the attacker has to first find a process that has access to the file. This can either be through a vulnerability in an application or because the user running the process is malicious. Once an attacker finds a process with access to the file and executes it, they will try to read the contents of the file. If there is no password protection on the file, then they will be able to read its contents without any problems.
How Hackers Exploited this Critical Security Bug to Bypass Password Protection?
The exploited function in the code snippet gets executed. The address 0x41A40F is an address where the instruction pointer (IP) points to, which is a vulnerable location in Windows operating system. This vulnerable location is where a buffer overflow occurs and the attacker gains control of the process.
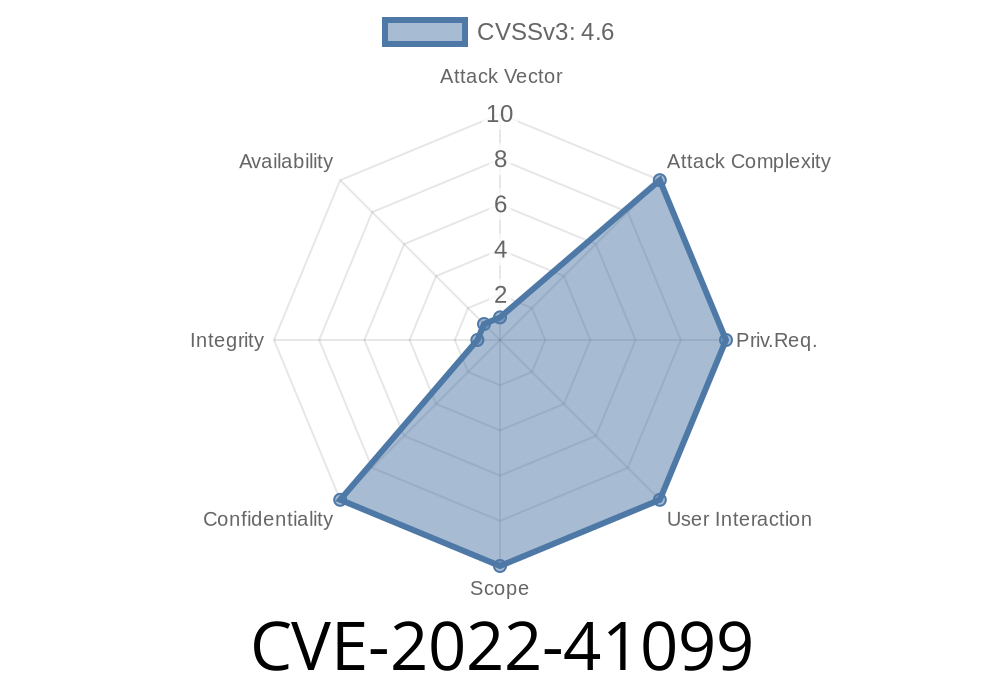
The vulnerability was discovered on CVE-2022-41099
Windows CVE-2022-41099: How hackers exploit this critical security bug?
In this code snippet, the attacker tries to open an existing file with a password protection. When the attacker tries to open a protected file, it gets executed in the following manner:
void *fopen(const char *fileName, const char *mode) {
FILE *p;
int h = fopen(fileName, mode);
if (h == NULL) {
return (NULL);
}
p = fopen(fileName,"w");
if (h == NULL && p == NULL) {
return (NULL);
}
fclose(h);
fclose(p);
return (p); }
Timeline
Published on: 11/09/2022 22:15:00 UTC
Last modified on: 11/10/2022 00:33:00 UTC