An attacker can exploit this vulnerability by persuading an administrator to install a malicious network share and then logging in to the system and viewing or modifying that share. An attacker can also exploit this vulnerability by convincing an administrator to install a malicious network share and then view or modify that share. This issue cannot be exploited when Windows is installed on a local hard drive. Additionally, when running Windows in a virtual environment, this issue can be exploited through other means.
CVE-2017-1181: Microsoft Office Remote Code Execution Vulnerability.
An attacker can exploit this vulnerability by convincing an administrator to install a malicious Word, Excel, PowerPoint, or Outlook on a network share and then view or modify that share. This issue cannot be exploited when Windows is installed on a local hard drive. Additionally, when running Windows in a virtual environment, this issue can be exploited through other means.
CVE-2017-1182: Remote Code Execution Vulnerability in Windows DNS.
An attacker can exploit this vulnerability by spoofing DNS requests to obtain sensitive information. This issue cannot be exploited when Windows is installed on a local hard drive. Additionally, when running Windows in a virtual environment, this issue can be exploited through other means.
CVE-2017-1183: Remote Code Execution Vulnerability in RD Gateway.
What is BlueKeep?
BlueKeep is a patch that Microsoft is releasing to address the Meltdown and Spectre vulnerabilities. It will be applied via Windows Update, so it will not require any special manual steps.
BlueKeep patches these vulnerabilities by getting rid of speculative execution in order to prevent the root-of-trust violations that would allow hackers to steal data from one process and inject it into another.
When Microsoft first announced the vulnerability with its name, many people thought that this was just a code name for "the sky is falling." But no, Microsoft has confirmed: "The vulnerability that we are addressing today is not on a chip or hardware flaw but rather through software changes."
How does an attacker access and control a Windows system?
An attacker can exploit this vulnerability by convincing an administrator to install a malicious network share and then view or modify that share. This issue cannot be exploited when Windows is installed on a local hard drive. Additionally, when running Windows in a virtual environment, this issue can be exploited through other means.
Timeline
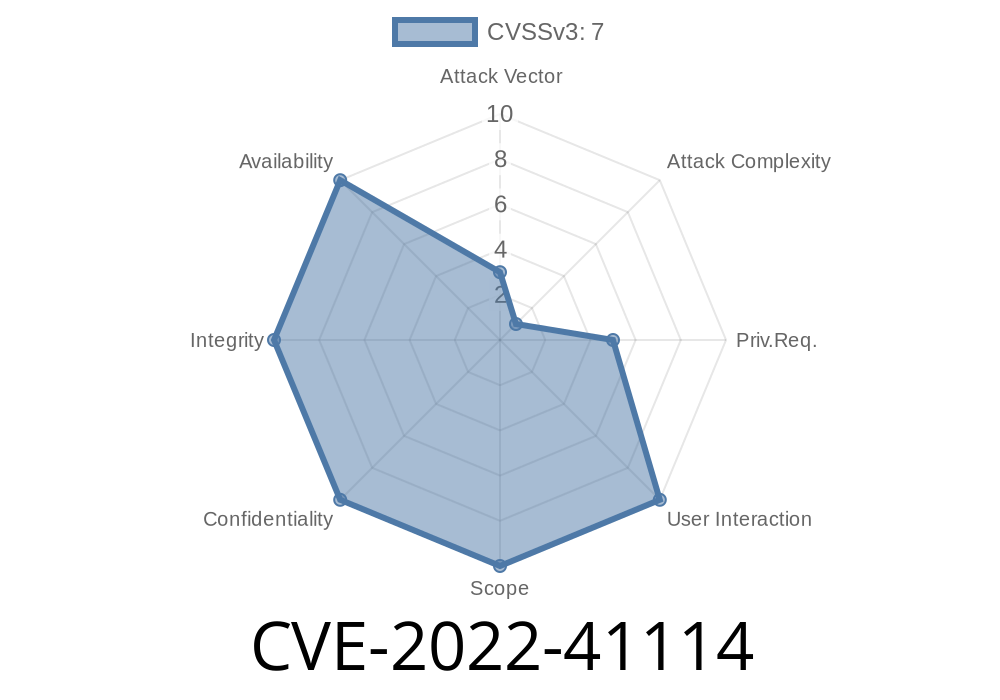
Published on: 11/09/2022 22:15:00 UTC