---
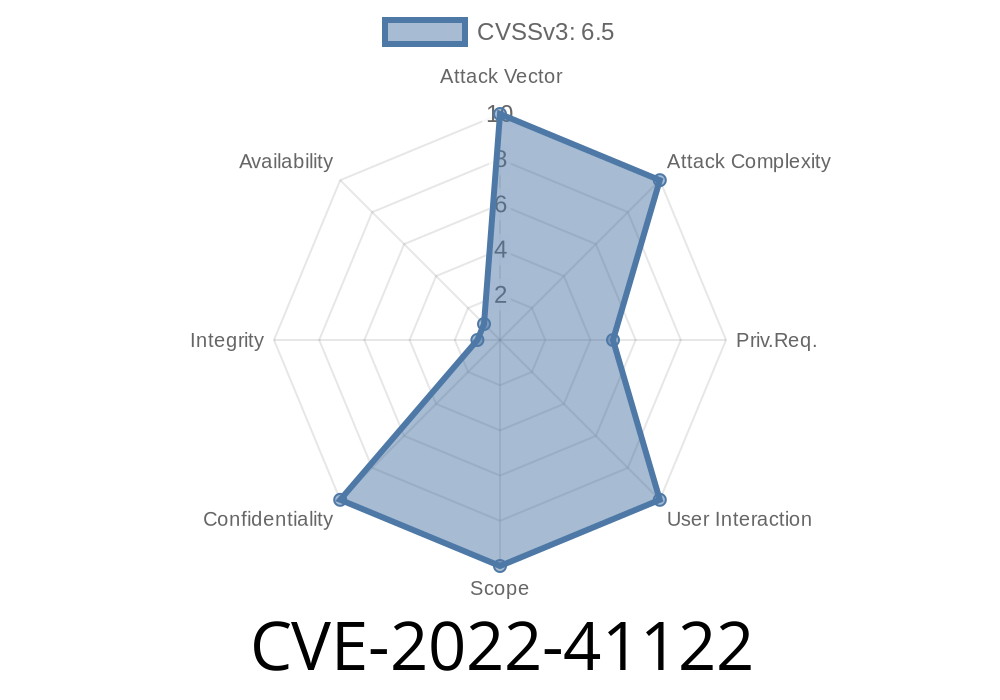
If you manage Microsoft SharePoint servers, you can’t afford to ignore CVE-2022-41122. This vulnerability, disclosed and patched by Microsoft in November 2022, exposes your system to spoofing attacks—meaning attackers can trick users or applications into thinking malicious content is legitimate. In this guide, you’ll learn what this CVE is all about, how attackers might exploit it, and what you need to do to protect your SharePoint environment.
What is CVE-2022-41122?
CVE-2022-41122 describes a spoofing vulnerability in Microsoft SharePoint Server. Essentially, it lets an attacker present fake or manipulated data as if it came from a trusted source, fooling users or backend processes.
How Does the Exploit Work?
At its core, this vulnerability lets attackers inject or manipulate HTTP headers or other input processed by SharePoint so that the server accepts and relays information as if it were trusted. For example, imagine a phishing link or embedded content that appears 100% legitimate to your users, but really leads them to an attacker-controlled page.
A common attack vector is when SharePoint fails to properly validate URLs or resources referenced in web parts, emails, or redirections.
User clicks a link or views a manipulated web part.
3. Content is rendered, appearing to be from your trusted internal server, but it secretly loads scripts or content from a malicious site.
Exploit Details & Proof-of-Concept
Let's see what this might look like with a simplified code snippet.
Suppose SharePoint fails to sanitize the RedirectUri parameter in a GET request
GET /_layouts/15/Authenticate.aspx?Source=https://malicious.attacker.com/payload
If SharePoint simply takes the Source parameter at face value (without validation), it could redirect users to an external website, thinking it’s a legitimate action.
Imagine SharePoint server code like this (simplified)
// BAD: No validation! Vulnerable scenario
string redirectUrl = Request.QueryString["Source"];
Response.Redirect(redirectUrl);
In a secured application, you’d want something like
// GOOD: Validate the redirect URL
string redirectUrl = Request.QueryString["Source"];
if (IsLocalUrl(redirectUrl)) {
Response.Redirect(redirectUrl);
} else {
// Log and block
}
IsLocalUrl() verifies the redirect is only to a local or allowed address.
Detection Steps
1. Review server logs for requests to endpoints like /Authenticate.aspx or similar, with external URLs in parameters.
2. Look for user reports of unexpected redirects or login/logout pages.
3. Use penetration testing tools (like Burp Suite) to test whether external redirects or resource loads are accepted by the server.
Microsoft’s Patch
Microsoft fixed this with security updates on *November 8, 2022*. The patch improves sanitization and validation of URLs or HTTP inputs that can be used for spoofing.
- Microsoft Security Update Guide: CVE-2022-41122
Patch ASAP. Without the update, your SharePoint is at risk.
Manually review and sanitize input in custom SharePoint web parts and workflows.
- Educate users not to click strange links, even if they look “internal”—this is classic phishing territory.
References
- Microsoft CVE-2022-41122 Official Advisory
- NVD - CVE-2022-41122 Detail
- SharePoint Patch Guidance
Summary
CVE-2022-41122 is a serious SharePoint flaw—one that lets attackers fool your users and your system. It is easy to exploit and can lead to major consequences like credential theft, information leakage, and more. The best defense is to apply the security update immediately, audit your system, and remind your users to always be on guard.
Feel free to reach out if you have more questions or need a step-by-step patching guide! Stay safe.
Timeline
Published on: 11/09/2022 22:15:00 UTC
Last modified on: 11/10/2022 00:33:00 UTC