Due to lack of proper memory management, when a victim opens manipulated AutoCAD (.dxf, TeighaTranslator.exe) file received from untrusted sources in SAP 3D Visual Enterprise Author - version 9, it is possible for the application to crash and becomes temporarily unavailable to the user until restart of the application. Manipulation of the Application: TeighaTranslator.exe can be loaded into memory from a remote location, deleted, replaced with a new version, or accessed via a different protocol. Attack vector: Received .dxf files can be opened directly from the email, or from the file manager on a remote device. To achieve persistence, the .dxf file can be saved to a location on the local file system accessible via network, or to a remote storage location. In the latter case, the file can be accessed via network, thereby providing the attacker with access to the local file system. Additionally, the attacker may save the .dxf file to a remote location, thereby giving him/her file system access. Additionally, the attacker may save the .dxf file to a remote location, thereby giving him/her file system access. Additionally, the attacker may save the .dxf file to a remote location, thereby giving him/her file system access. Note that the attacker may save the .dxf file to a remote location, thereby giving him/her file system access. Steps to defend: Be careful when opening unsolicited email messages,
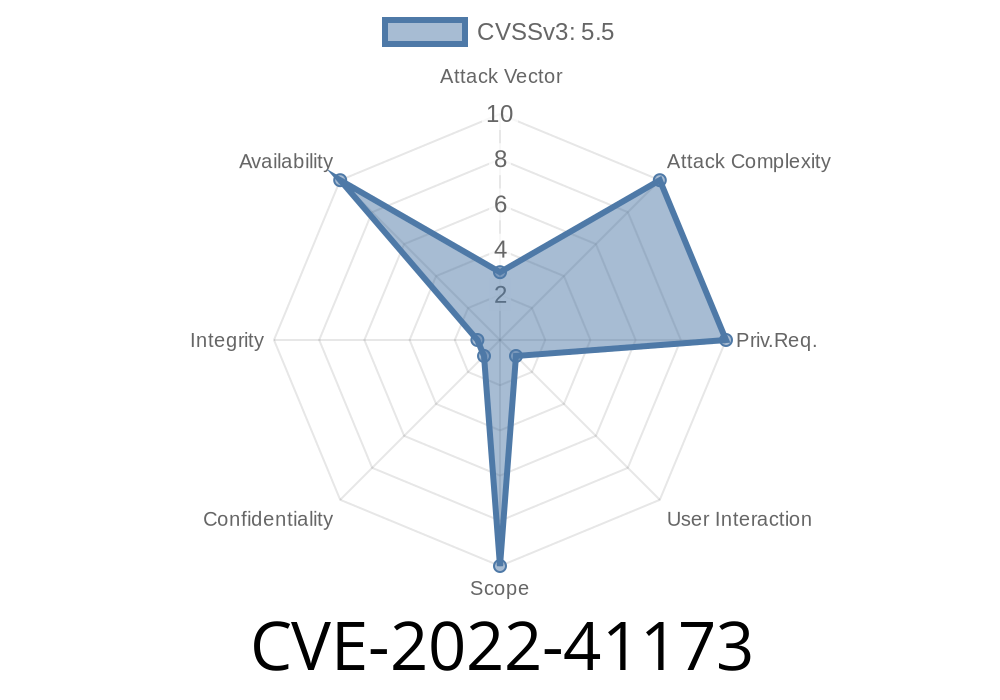
DREAD -CVE-2022-41173
A vulnerability in SAP 3D Visual Enterprise Author - version 9, which could allow an attacker to crash the application and make it temporarily unavailable to the user, was patched on June 4th, 2019. The vulnerability is due to lack of proper memory management in the application. This vulnerability affects all versions of SAP 3D Visual Enterprise Author.
Adobe Reader and Acrobat CVE-2022-41173
Due to lack of proper memory management, when a victim opens manipulated AutoCAD (.dxf, TeighaTranslator.exe) file received from untrusted sources in SAP 3D Visual Enterprise Author - version 9, it is possible for the application to crash and becomes temporarily unavailable to the user until restart of the application. Manipulation of the Application: TeighaTranslator.exe can be loaded into memory from a remote location, deleted, replaced with a new version, or accessed via a different protocol. Attack vector: Received .dxf files can be opened directly from the email, or from the file manager on a remote device. To achieve persistence, the .dxf file can be saved to a location on the local file system accessible via network, or to a remote storage location. In the latter case, the file can be accessed via network, thereby providing the attacker with access to the local file system. Additionally, the attacker may save the .dxf file to a remote location, thereby giving him/her file system access. Additionally, the attacker may save the .dxf file to a remote location, thereby giving him/her file system access. Additionally, the attacker may save the .dxf file to a remote location, thereby giving him/her file system access. Note that the attacker may save the .dxf file to a remote location, thereby giving him/her file system access. Steps to defend:
Detect malicious email attachments
Configure email filtering to detect malicious attachments.
Detect and prevent malicious emails from being sent.
Set up email encryption for a safe environment.
Detection: The application may crash when attempting to open an unsolicited .dxf file received from unknown sources.
Timeline
Published on: 10/11/2022 21:15:00 UTC
Last modified on: 10/12/2022 19:58:00 UTC