This issue is present in all SAP products, but it is particularly dangerous in SAP 3D Visual Enterprise Author, as it is a production-setup application, which means that one of the first clicks on a compromised document may lead to a situation when the system gets compromised and attackers gain full access to the system.
Unfortunately, it is very hard to find a proper solution for this type of vulnerability. However, in order to protect your system, you need to know about it, and most importantly, you need to be careful.
What is the SAP 3D Visual Enterprise Author?
SAP 3D Visual Enterprise Author is a complex and powerful software application that allows users to create, edit, and manage 3D models in a system of documents. This software is mostly used by architects in their practice and the company’s internal services.
The issues with this product are present in all versions of SAP products, but it is particularly dangerous in SAP 3D Visual Enterprise Author, as it is a production-setup application, which means that one of the first clicks on a compromised document may lead to a situation when the system gets compromised and attackers gain full access to the system.
What is the issue?
If you want to prevent the system from getting compromised and attackers gaining full access to your system, you need to know about this issue.
The issue is that, when a document is loaded in an SAP 3D Visual Enterprise Author production-setup application, it will automatically execute whatever user inputbeds it has. A user inputbed may be something like a phone number or an email address. This means that if the document is compromised in any way, attackers can load their own malicious inputbed into the system and click on it in order to hijack the whole system.
Description of the issue
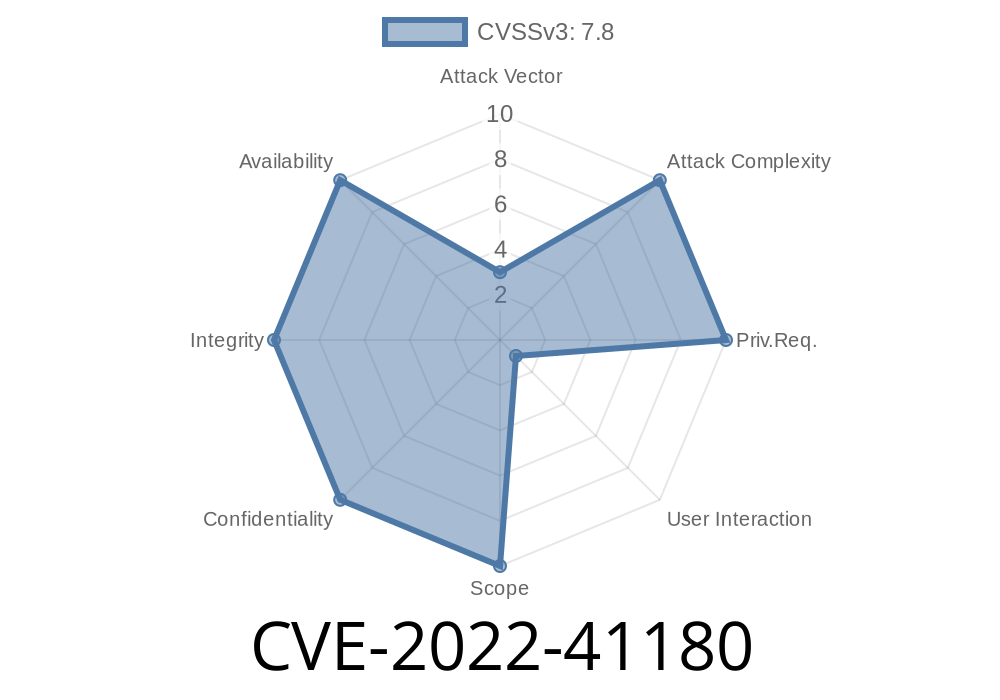
CVE-2022-41180 is a vulnerability that can be exploited by attackers to gain full access to SAP 3D Visual Enterprise Author. The issue comes from the production-setup configuration of this application, which means that one of the first clicks on a compromised document may lead to a situation when the system gets compromised and attackers gain full access to the system.
This issue is present in all SAP products, but it is particularly dangerous in SAP 3D Visual Enterprise Author, as it is a production-setup application.
Unfortunately, it is very hard to find a proper solution for this type of vulnerability. However, in order to protect your system, you need to know about it and be careful.
Timeline
Published on: 10/11/2022 21:15:00 UTC
Last modified on: 10/12/2022 20:06:00 UTC