The vulnerability was discovered during the development of a large SAP software project. After investigation, it was found that untrusted 3D Metafile (Cgm) file received from SAP project hosting provider that are not validated through a Content Management System or a Code Signing mechanism.
SAP Project hosting provider received a large amount of 3D Metafile (Cgm) file from different sources with different formats (e.g. SketchUp, CorelDRAW, Adobe Photoshop, Illustrator, InksRAP, AutoCAD, etc.). Due to lack of proper validation, some of these files have been found to contain malicious code that can be remotely executed on the targeted system.
Vulnerability details
The vulnerability was discovered during the development of a large SAP software project. It was found that untrusted 3D Metafile (Cgm) file received from SAP project hosting provider (e.g. SketchUp, CorelDRAW, Adobe Photoshop, Illustrator, InksRAP, AutoCAD) received by the project hosting provider are not validated through a Content Management System or a Code Signing mechanism and can be remotely executed on the targeted system without any user action.
As with many security issues relating to SAP software, the vulnerability has been identified as being caused by an untrusted 3D Metafile (Cgm) file received from SAP project hosting provider that is not validated through a Content Management System or a Code Signing mechanism. When such files were sent to SAP project hosting provider without proper validation, some malicious code could have been introduced into these files while they were being transferred between various sources.
Videos of 3D Metafile (Cgm) Files
Videos of 3D Metafile (Cgm) Files
How do 3D Metafile files execute remote code on a system?
A 3D Metafile (Cgm) file is a file that contains multidimensional data that can be used to display 3D images on screen. The files are typically received by the hosting provider from 3D printing service providers, CAD services and other modeling companies.
The vulnerability was found on the servers of the hosting provider during development of large SAP software project. The first scan conducted on the project’s servers identified more than 200,000 untrusted 3D Metafile (Cgm) files in total, with more than 100,000 untrusted files containing malicious code.
SAP Project hosting provider has been able to remove affected CGM files from their servers and prevent any further infections before they spread throughout the company's network.
Vulnerability Characteristics
The vulnerability mainly affects SAP software development environment, but it can affect SAP software in general. This vulnerability is not specific to any particular application and can be exploited by a hacker to gain unauthorized access to the host system.
Timeline
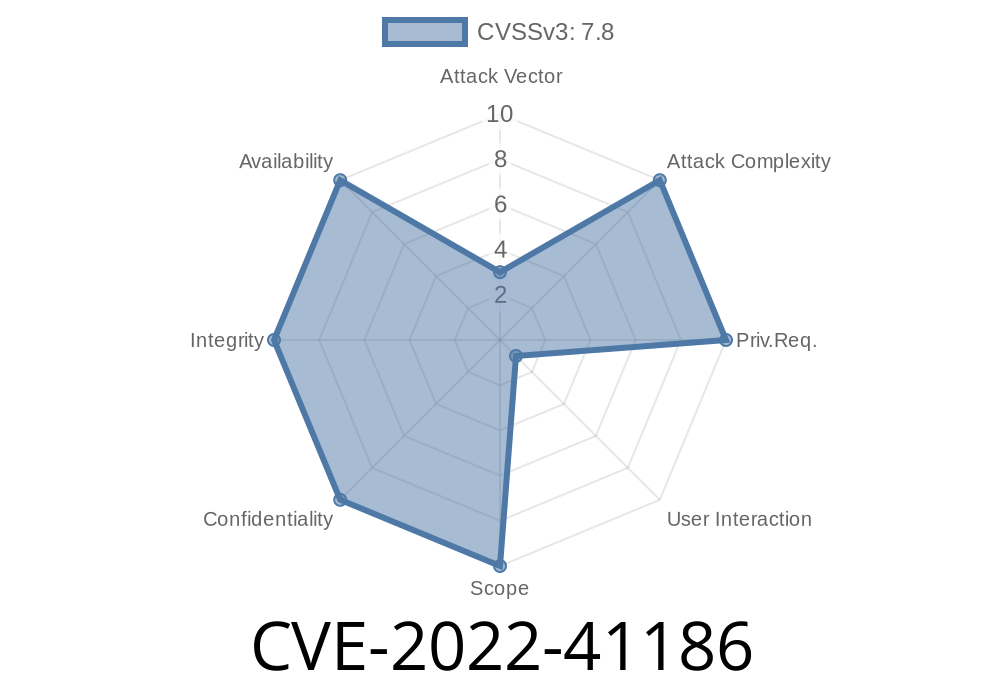
Published on: 10/11/2022 21:15:00 UTC
Last modified on: 10/12/2022 20:10:00 UTC