It is possible that a Remote Code Execution can be triggered when a user downloads and opens a file with malicious Java applet embedded in that file. When the victim opens a malicious or compromised .jt file received from an untrusted source, it is possible that a Remote Code Execution can be triggered when a victim redirects a system’s network traffic through a RCE vulnerability in the SAP 3D Visual Enterprise Viewer - version 9. To exploit this vulnerability, an attacker must send a specially crafted URL to a victim. When a victim opens a malicious or compromised .jt file received from an untrusted source, it is possible that a Remote Code Execution can be triggered when a victim redirects a system’s network traffic through a RCE vulnerability in the SAP 3D Visual Enterprise Viewer - version 9. To exploit this vulnerability, an attacker must send a specially crafted URL to a victim.
Vulnerability Information
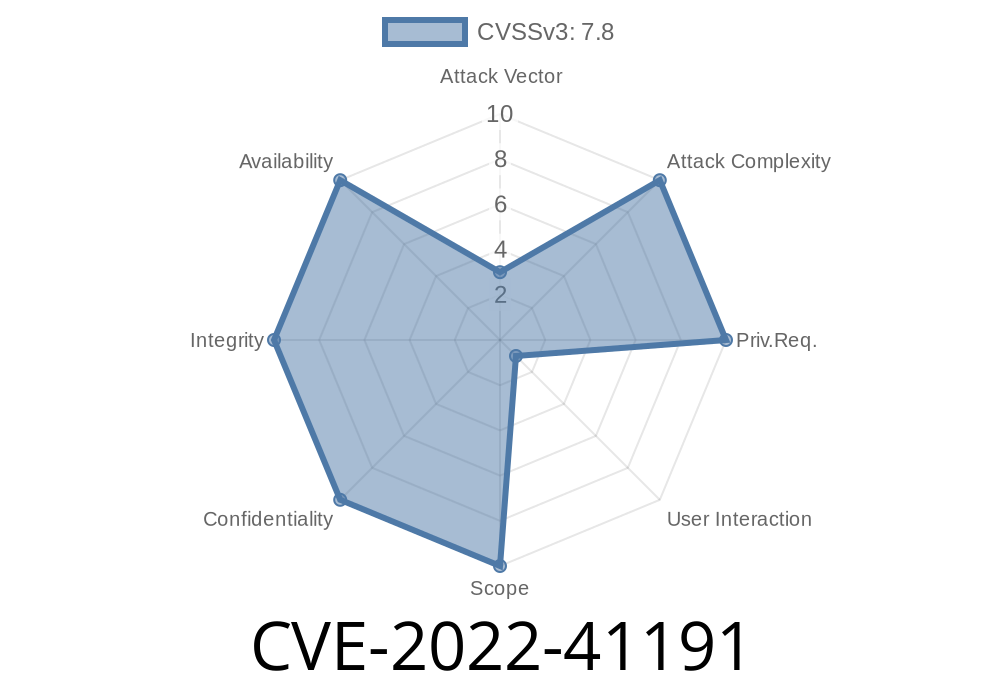
SAP might be vulnerable to a Remote Code Execution attack when a user downloads and opens a file with malicious Java applet embedded in that file. The vulnerability is tracked as CVE-2022-41191.
The vulnerability allows an attacker to execute arbitrary code on the system of a vulnerable victim. The vulnerability can be triggered by the download and opening of an infected .jt file sent from an untrusted source, which will cause the RCE because SAP 3D Visual Enterprise Viewer - version 9 is installed on the system. SAP 3D Visual Enterprise Viewer - version 9 is found on SAP GUI, Web Graphics Server, and Monitoring Server software.
RCE - SAP 3D Visual Enterprise Viewer - version 9
When a victim opens a malicious or compromised .jt file received from an untrusted source, it is possible that a Remote Code Execution can be triggered when a victim redirects a system’s network traffic through a RCE vulnerability in the SAP 3D Visual Enterprise Viewer - version 9. To exploit this vulnerability, an attacker must send a specially crafted URL to a victim.
Steps to Be Taken to Exploitation Remote Code Execution
The following list of steps outlines the process to exploiting a Remote Code Execution vulnerability in SAP 3D Visual Enterprise Viewer - version 9.
1. Generate a malicious .jt file containing Java Applet which is either signed or unsigned
2. Compromise a legitimate .jt file by compromising the system that hosts it
3. Send a specially crafted URL to victim with their system's network traffic redirected through RCE vulnerability in SAP 3D Visual Enterprise Viewer - version 9
4. When victim opens the malicious or compromised .jt file, they will be prompted with instructions on how to download and open the file
5. Victim will then trigger an RCE vulnerability in SAP 3D Visual Enterprise Viewer - version 9
How to trigger CVE-2022-41191 vulnerability?
To trigger this vulnerability, the attacker sends a specially crafted URL to the victim.
Vulnerability overview
This vulnerability allows an attacker to execute code on a vulnerable system. This can allow an attacker to take control of the target system. The update Microsoft has released includes a fix for this issue and all systems are updated to prevent further exploitation of this issue.
Timeline
Published on: 10/11/2022 21:15:00 UTC
Last modified on: 10/12/2022 20:20:00 UTC