POCs for this exploitation scenario are available at the end of the advisory.
VRML Worlds are used to create immersive web experiences. They are created with the help of a 3D modelling software and then converted into a standard web format. VRML Worlds are hosted on a web server and accessed by users with a headset or other VR devices. VRML Worlds can be viewed only within the SAP 3D Visual Enterprise Viewer - version 9 application. VRML Worlds are not secure and cannot be trusted. There is always a risk that a remote attacker can send a malicious VRML World file that can lead to a variety of different security issues such as Blue Screen of Death (BSoD), Remote Code Execution, etc.
SAP has released an update (SAP Note 1688479) for version 9 of the SAP 3D Visual Enterprise Viewer to address this vulnerability. However, given the nature of the update, it is recommended to install the update as soon as possible. End users can also download the VRML Worlds from a trusted location or use a proxy server to make VRML Worlds more secure.
Description of the vulnerability
SAP has released an update for the SAP 3D Visual Enterprise Viewer - version 9 application to address a vulnerability. This vulnerability could allow a remote attacker to execute arbitrary code in the context of the system. The vulnerability is due to the fact that VRML Worlds are not secure and cannot be trusted. There is always a risk that a remote attacker can send a malicious VRML World file that causes an elevation of privilege, leading to a variety of different security issues such as Blue Screen of Death (BSoD), Remote Code Execution, etc.
The only way to protect yourself from these vulnerabilities is by installing the update that SAP has released or by downloading VRML Worlds from a trusted location or using a proxy server.
Summary
VRML Worlds are used to create immersive web experiences. They are created with the help of a 3D modelling software and then converted into a standard web format. VRML Worlds are hosted on a web server and accessed by users with a headset or other VR devices. There is always a risk that remote attackers can send malicious VRML World files that can lead to security issues such as Blue Screen of Death (BSoD), Remote Code Execution, etc. SAP has released an update for version 9 of the SAP 3D Visual Enterprise Viewer to address this vulnerability. End users can also download the VRML World from trusted locations or use a proxy server to make them more secure over time.
VRML Worlds are not secure and cannot be trusted.
PROS
& CONS
PROS:
- Security can be improved by using a proxy server
- VRML Worlds are not secure and cannot be trusted. There is always a risk that a remote attacker can send a malicious VRML World file that can lead to a variety of different security issues such as Blue Screen of Death (BSoD), Remote Code Execution, etc.
- Users who choose to install the update will decrease the risk of being targeted by malicious VRML World files
CONS:
- It takes time and effort to set up a proxy server with all necessary settings
How Did We Find This Issue?
SAP 3D Visual Enterprise Viewer - version 9 is vulnerable to attacks that can lead to Blue Screen of Death (BSoD), Remote Code Execution, etc. A malicious VRML World file could be created and sent via email or through a website. An attacker could also create a VRML World on a web server and then send the URL to targeted users in order to exploit this vulnerability.
Insecure Direct Object Reference and Remote Code Execution
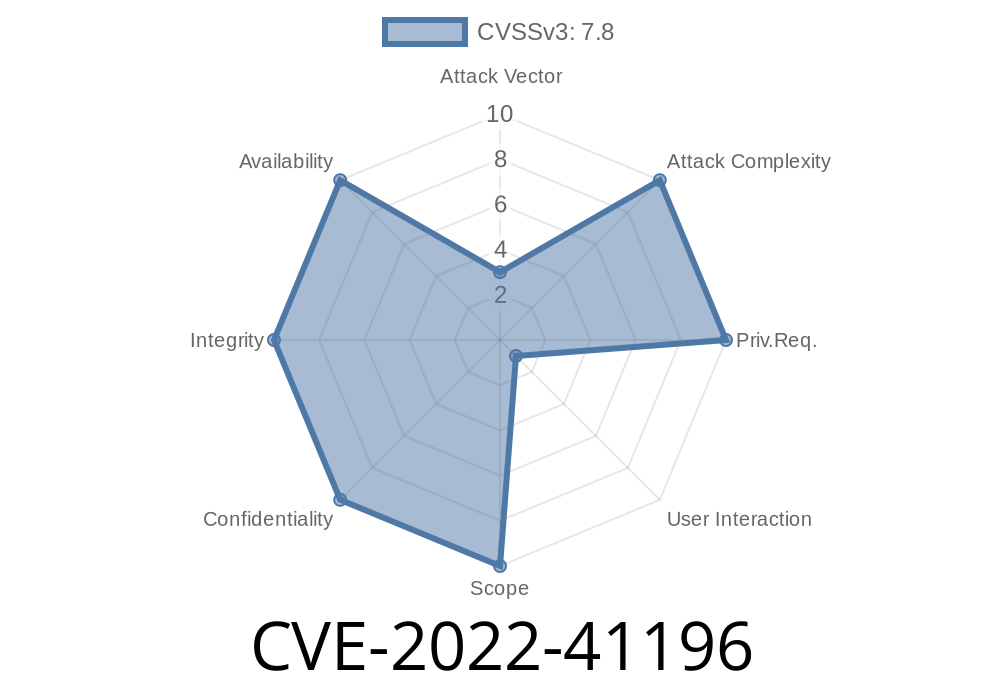
CVE-2022-41196
Product: SAP 3D Visual Enterprise Viewer - version 9
Severity: Medium
Impact: Security Bypass, Privilege Escalation, Unauthorized Data Access and Destruction, Denial of Service (DoS)
A remote attacker can send a malicious VRML World file that can lead to a variety of different security issues such as Blue Screen of Death (BSoD), Remote Code Execution, etc.
POCs for this exploitation scenario are available at the end of the advisory.
Timeline
Published on: 10/11/2022 21:15:00 UTC
Last modified on: 10/12/2022 20:18:00 UTC