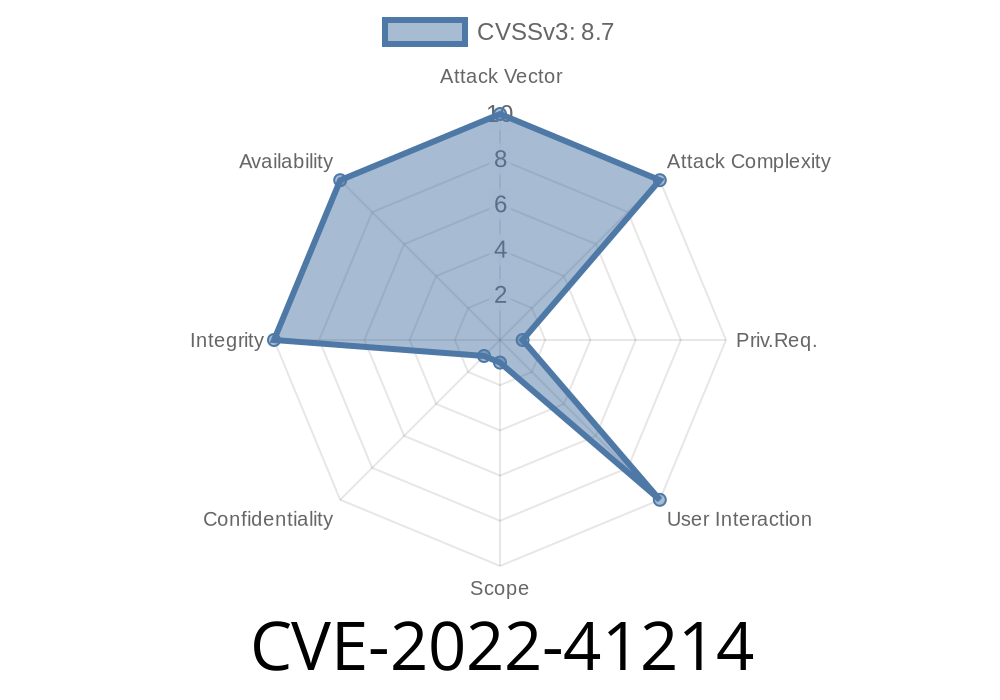
This issue exists due to insufficient input validation. Attackers can remotely enable functions (in APS and SAP S/4HANA) by specifying their URL, which allows them to perform actions which are otherwise not available. Due to the nature of ABAP programming language functions are not checked to see if they are enabled or not. This means that if an attacker can specify a function’s URL they can enable that function and use it as if it was a local function. An attacker can do this in two ways:
With the first method, the attacker must simply know the URL for a remote enabled function. This is less likely to be an issue than with locally enabled functions. With the second method, an attacker can simply input data into a form field or click a remote enabled link. This is a more serious issue.
Vulnerability Characteristics
Vulnerable functions are any function that is enabled remotely.
The issue does not exist because the backend server is not vulnerable. It exists because the ABAP programming language allows functions to be enabled remotely.
What You Need to Know about this Issue?
This issue is most likely to exist in APS and SAP S/4HANA. If you are using SAP HANA, then you can use the following workaround:
The below command should be placed in a ABAP script. It will disable all remote enabled functions for a specific URL.
set_disable_remote_enabled_functions( sap=>TRUE );
The below command should be placed in an ABAP script or other programming language (BI) to disable all remote enabled functions for all URLs.
set_disable_remote_enabled_functions( sap=>FALSE );
Dependency Bypass
The issue exists due to insufficient input validation. Attackers can remotely enable functions (in APS and SAP S/4HANA) by specifying their URL, which allows them to perform actions which are otherwise not available. Due to the nature of ABAP programming language functions are not checked to see if they are enabled or not. This means that if an attacker can specify a function’s URL they can enable that function and use it as if it was a local function. An attacker can do this in two ways:
With the first method, the attacker must simply know the URL for a remote enabled function. This is less likely to be an issue than with locally enabled functions. With the second method, an attacker can simply input data into a form field or click a remote enabled link. This is a more serious issue.
APS - Overview
APS is an application programming interface that is used by SAP S/4HANA to communicate with external applications, such as web services and databases. Due to the nature of ABAP programming language functions are not checked to see if they are enabled or not. This means that if an attacker can specify a function’s URL they can enable that function and use it as if it was a local function. An attacker can do this in two ways:
With the first method, the attacker must simply know the URL for a remote enabled function. This is less likely to be an issue than with locally enabled functions. With the second method, an attacker can simply input data into a form field or click a remote enabled link. This is a more serious issue.
Timeline
Published on: 11/08/2022 22:15:00 UTC
Last modified on: 12/09/2022 17:00:00 UTC