Subsequently, an attacker may access and/or modify Jenkins data, create or alter jobs, or propagate the attack to other Jenkins installations. This may lead to a breach of the Jenkins user’s security. Cross-Site Request Forgery (CSRF) is a type of attack in which an attacker tricks a user into performing a task that the user did not intend to do. In Jenkins, CSRF occurs when an attacker tricks a user into making a request to another site. To make Jenkins a target of a cross-site request forgery attack, the attacker must know the credentials of the Jenkins user. This may be done through a number of ways. The most common way is to trick the user into clicking a link in an email that appears to be from a Jenkins administrator. An email may also appear to be from a Jenkins administrator and include a link that takes the user to the Jenkins administration page.
Summary
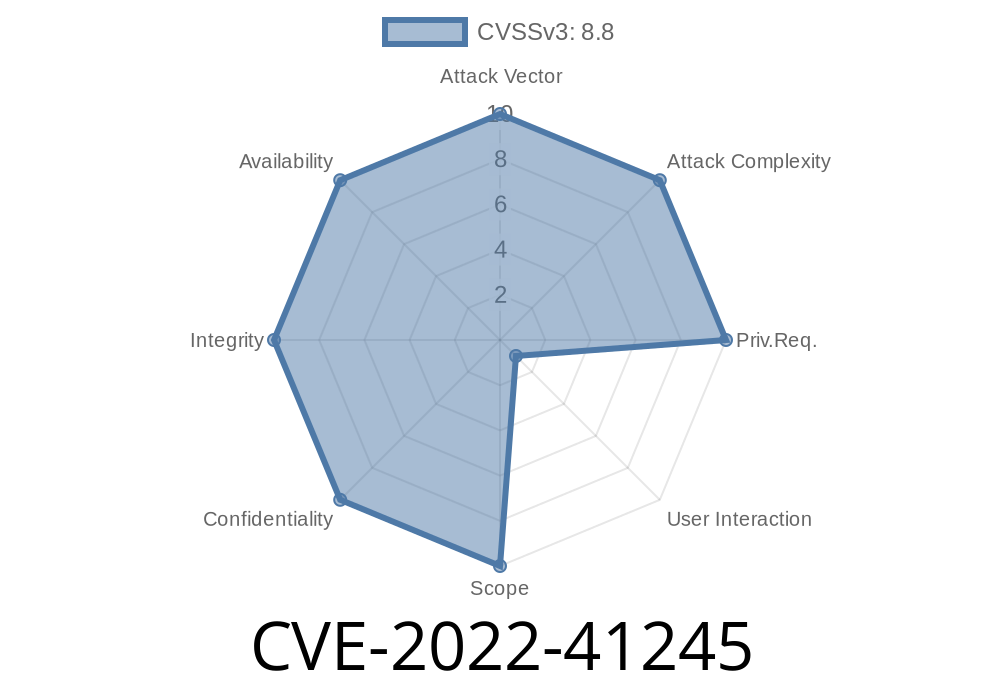
CVE-2022-41245 is a vulnerability in Jenkins which allows an attacker to:
1. Gain unauthorized access to Jenkins data or create jobs, or 2. Perform a cross-site request forgery (CSRF) attack on the Jenkins user. This may lead to a breach of the Jenkins user's security.
Mitigation Strategies
Many of the prevention strategies for CSRF exist in Jenkins. For example, "Show a pop-up confirmation when a user first confirms their email address." This will help prevent any credentials from being exposed to an attacker who may trick the user into clicking a malicious link in an email or on their website.
Cross Site Request Forgery: How to prevent and mitigate this type of attack
CSRF prevention tips
For Jenkins users, there are several best practices for prevention of CSRF:
1. Use the Token feature to allow only pre-authorized actions
2. Use the HTTPOnly cookie flag to limit the ability to read or write cookie data from JavaScript code
3. Configure Jenkins to run with a low privilege level
4. Enable the X-Frame-Options header to prevent browser rendering of content in an iframe on other sites
5. Protect Jenkins via authentication and authorization with a password-based plugin like Auth0
Vulnerability overview
A vulnerability was discovered in Jenkins on May 22, 2018. The vulnerability may be exploited by an attacker to execute CSRF attacks against users of Jenkins.
Timeline
Published on: 09/21/2022 16:15:00 UTC
Last modified on: 09/22/2022 15:51:00 UTC