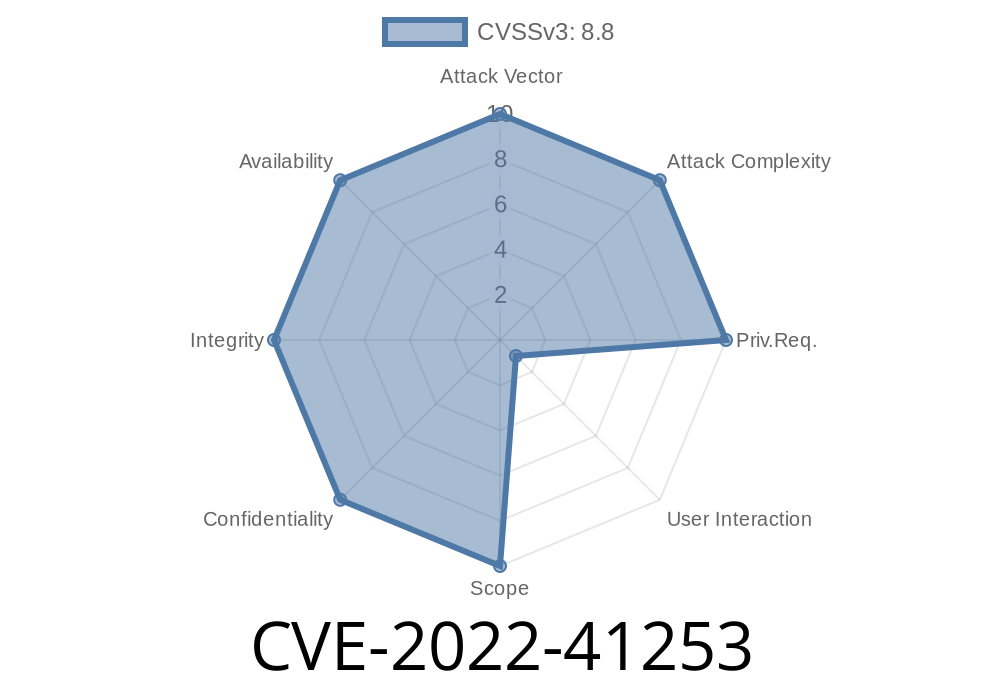
This CSRF vulnerability can be exploited by an attacker who controls a target Jenkins installation and configures the plugin to pass login credentials to another server. In order for this to happen, the attacker must first configure a target Jenkins instance to pass login credentials to another server.
Then the attacker must configure the plugin to send those credentials to another server. This can be done by setting the CSRF_TOKEN and CSRF_COOKIE_SESSION_ID environment variables to the values of the corresponding variables in the other server. Finally, the attacker must configure the plugin to pass those credentials to another server. This can be done by setting the CSRF_TOKEN and CSRF_COOKIE_SESSION_ID environment variables to the values of the corresponding variables in the other server. If the plugin was installed via the Jenkins console, the attacker must also make sure that the plugin is enabled on the target Jenkins instance. If the plugin was installed manually, the attacker must make sure that the plugin is enabled in the plugin manager of the target Jenkins instance.
How do I know if my site is vulnerable?
The easiest way to check if your site is vulnerable is to take a look at the configuration of the Jenkins plugin. If you see an entry for "CSRF_TOKEN" or "CSRF_COOKIE_SESSION_ID," this means that your site is vulnerable. If you are not sure, you can try setting some cookies in the Jenkins console and then trying to log in from another server via the Jenkins plugin.
Affected Software
Jenkins
Java
Timeline
Published on: 09/21/2022 16:15:00 UTC
Last modified on: 09/22/2022 18:43:00 UTC