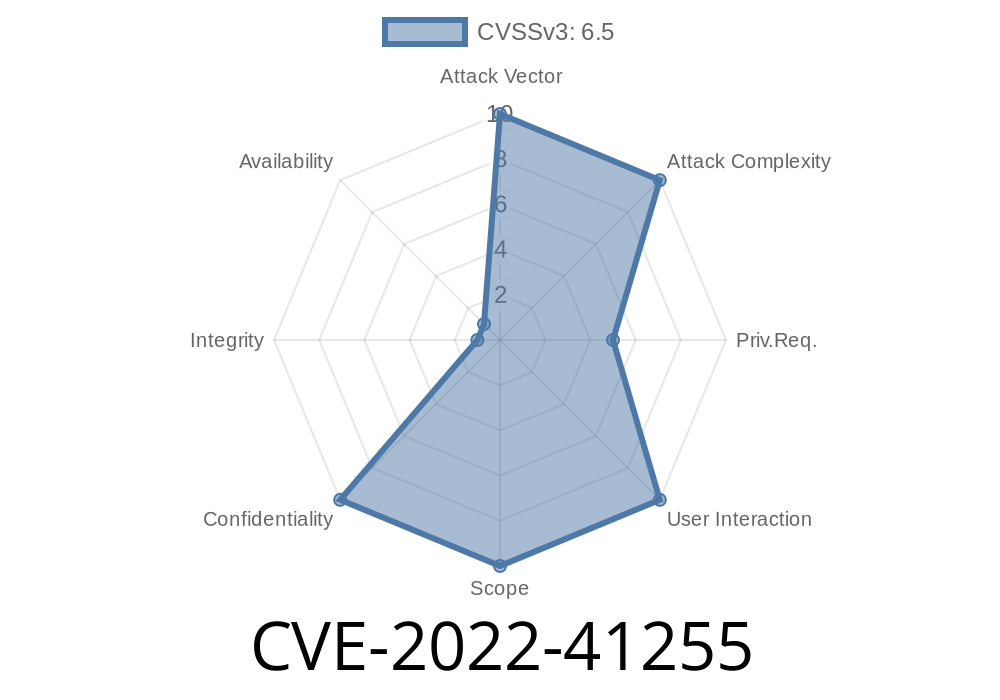
This may result in malicious actors gaining access to the API token used to authenticate with the Cons3rt service, potentially giving them the ability to upload and execute arbitrary code on the Jenkins server. The Jenkins plugin version 1.0.0 and earlier has been upgraded to resolve this issue. If you are using the Jenkins plugin, you must upgrade as soon as possible.
Monitoring, User Education and Observability Tips
The Cons3rt vulnerability is a remote code execution vulnerability that affects Jenkins, a software development tool. Remote code execution vulnerabilities are common in software and allow attackers to take control of the program's runtime environment by inserting malicious code into the application's memory.
With remote code execution vulnerabilities, an attacker can execute arbitrary code on the target machine, whether it be a web server or a VM. This can be achieved by any number of methods including: exploiting flaws in input validation, encoding malicious payloads in images/web pages, injecting malicious scripts into document or PDF files, etc.
Recommendations
Fix the following issues:
- Add a policy to prevent Jenkins from accessing the Cons3rt service.
- Disable API token authentication for the Cons3rt service.
- Update to version 1.0.1 of the Jenkins plugin, which has been released as a patch for CVE-2022-41255.
Upgrade to Consul 3.0.0 or later
The Consul service must be upgraded to version 3.0.0 or later to fix this issue. You can upgrade your Jenkins plugin to the latest version at https://plugins.jenkins-ci.org/versions/.
Timeline
Published on: 09/21/2022 16:15:00 UTC
Last modified on: 09/22/2022 18:47:00 UTC