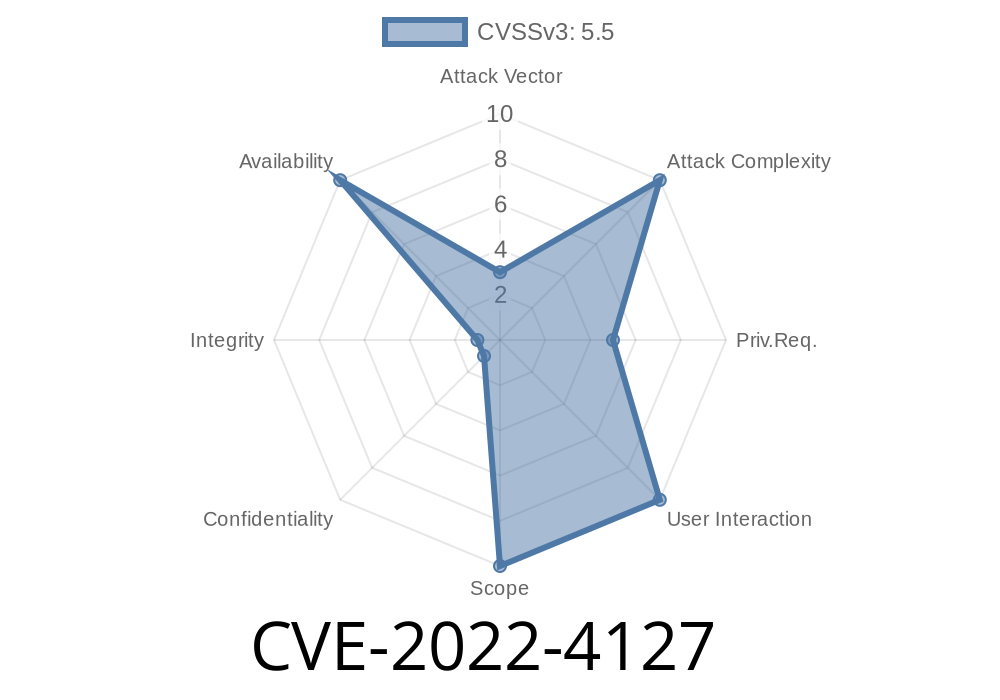
The Linux kernel is built for stability and security, but sometimes small mistakes can have big effects. In late 2022, a NULL pointer dereference bug was discovered in the function io_files_update_with_index_alloc. The issue, tracked as CVE-2022-4127, can allow a regular user to crash the system—a classic Denial of Service (DoS) attack. In this post, you’ll learn what caused this bug, how it can be exploited, and how you can protect your systems.
What Is CVE-2022-4127?
CVE-2022-4127 is a security flaw inside the Linux kernel’s I/O subsystem, specifically within the code that handles file lists for io_uring operations. If a user triggers this vulnerability, the kernel will try to access memory through a NULL pointer—causing a system crash (kernel panic).
In simple words: a normal user can crash Linux just by running the right program.
In some cases, the function didn’t check if a certain pointer was NULL before using it.
- If things line up just right, the function will dereference a NULL pointer (i.e., try to use memory at address zero).
Here’s a simplified snippet (in C language) inspired by the real buggy code
struct file *file = files[index];
if (!file) {
// Oops, "file" might be NULL here!
file->f_pos = ; // This line causes the crash.
}
The correct logic should have checked for NULL before accessing file
struct file *file = files[index];
if (file) {
file->f_pos = ;
}
Exploiting the Vulnerability (Denial of Service)
Any regular user with shell access can potentially crash the entire system. Here’s what an attack might look like:
Here’s a very rough proof-of-concept (PoC) in C (for illustration)
#include <stdio.h>
#include <sys/ioctl.h>
#include <fcntl.h>
#include <unistd.h>
#include <liburing.h>
int main() {
struct io_uring ring;
io_uring_queue_init(1, &ring, );
// Do some crafted calls that will trigger the NULL pointer bug
// (Details are omitted as they depend on the kernel version and setup)
// For illustration, let’s assume "ring" has a file index setup that is NULL
// Submitting an operation now may hit the bug.
printf("If your kernel is vulnerable, this might cause a panic!\n");
// Real exploit details are omitted for safety.
io_uring_queue_exit(&ring);
return ;
}
Warning: Don’t try untested PoCs on production systems! A real exploit could cause major downtime.
Fixes and Mitigations
The Linux kernel maintainers quickly patched the issue. The fix adds proper NULL pointer checks before using file objects in the affected function.
What To Do
- Upgrade your kernel: Make sure you’re running a version newer than the patched release.
- Apply distribution fixes: Red Hat, Ubuntu, and others have published advisories (see links below).
References and Further Reading
- CVE-2022-4127 at NVD
- Red Hat Security Advisory
- Ubuntu Security Notice
- Linux Kernel git commit (the patch)
Summary
CVE-2022-4127 proves that even a small code mistake can have big, system-wide impacts. With this bug, a regular user can knock a Linux machine offline just by running code that triggers a NULL pointer dereference in the kernel’s file handling logic. Luckily, the Linux community fixed this quickly. If you run Linux, patch up now!
Timeline
Published on: 11/28/2022 22:15:00 UTC
Last modified on: 12/01/2022 19:14:00 UTC