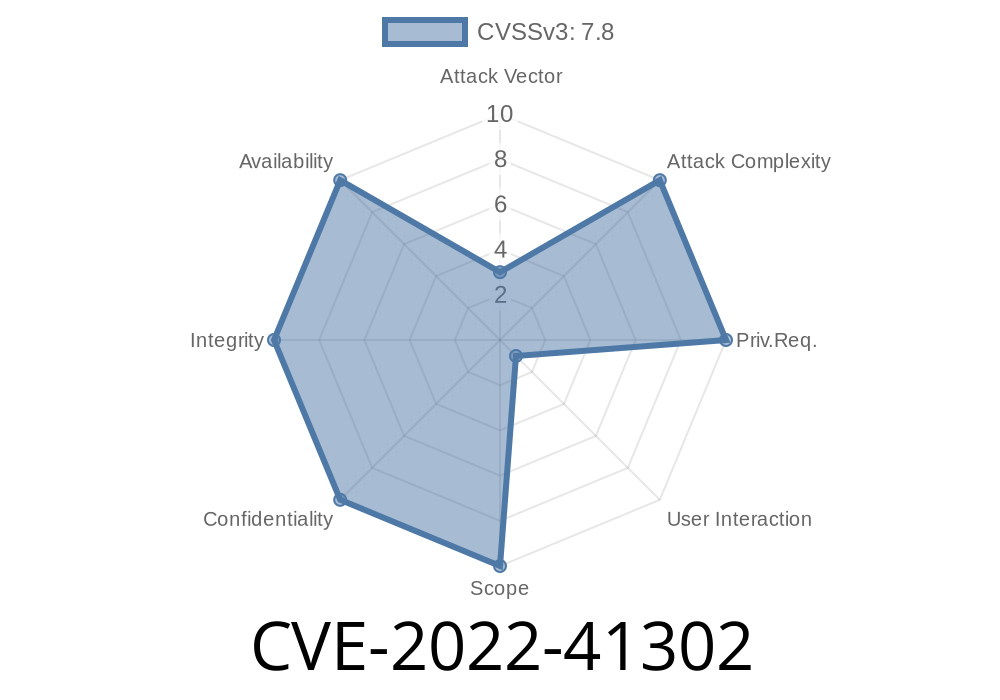
The vulnerability exists due to improper validation of input data to be used in an Autodesk FBX SDK function. An attacker could exploit this vulnerability by submitting a maliciously crafted FBX file through a website or a file transfer. An attacker would need to trick users into visiting a malicious website or by sending a maliciously crafted file to an end user. An attacker could also exploit this vulnerability by sending a maliciously crafted file to an intended recipient, who may be a developer of an Autodesk FBX SDK product. An attacker could send a maliciously crafted file to a developer of an Autodesk FBX SDK product. An attacker would need to trick a developer of an Autodesk FBX SDK product into opening a malicious file or by tricking a developer of an Autodesk FBX SDK product into believing that a code review of a maliciously crafted file has been completed. An attacker could send a maliciously crafted file to an intended product user, who may be a developer of an Autodesk FBX SDK product. An attacker would need to trick a developer of an Autodesk FBX SDK product into opening a malicious file or by tricking a developer of an Autodesk FBX SDK product into believing that a code review of a maliciously crafted file has been completed. An attacker could send a maliciously crafted file to an intended product user, who may be a developer of an Autodesk FBX SDK product. An attacker would need to trick a
Vulnerability Description
The vulnerability exists due to improper validation of input data to be used in an Autodesk FBX SDK function. An attacker could exploit this vulnerability by submitting a maliciously crafted FBX file through a website or a file transfer. An attacker would need to trick users into visiting a malicious website or by sending a maliciously crafted file to an end user. An attacker could also exploit this vulnerability by sending a maliciously crafted file to an intended recipient, who may be a developer of an Autodesk FBX SDK product. An attacker could send a maliciously crafted file to a developer of an Autodesk FBX SDK product. An attacker would need to trick a developer of an Autodesk FBX SDK product into opening a malicious file or by tricking a developer of an Autodesk FBX SDK product into believing that a code review of a maliciously crafted file has been completed. An attacker could send a maliciously crafted file to an intended product user, who may be a developer of an Autodesk FBX SDK product. An attacker would need to trick the developer of an Autodesk FBX SDK product into opening a malicious file or by tricking the developer of the Autodesk FBX SDK product into believing that code review has been completed for
Timeline
Published on: 10/14/2022 17:15:00 UTC
Last modified on: 10/19/2022 05:49:00 UTC