This issue can be leveraged by a remote attacker to execute arbitrary code on the server, leading to a compromise of the system.
impacted versions include: * Zimbra Collaboration 8.8.x * Zimbra Collaboration 8.8.x * Zimbra Collaboration 9.0.x A fix was released for ZCS versions 8.8.16, 8.8.17, 9.0.1, 9.0.2, 9.0.3, and 9.0.4. To update, please follow the instructions at https://doc.zimbra.com/index.php/releasenotes/1088 For ZCS 8.8.x and 9.0.x, we recommend that you update to one of the following versions: * Zimbra Collaboration 8.8.15 * Zimbra Collaboration 8.8.16 * Zimbra Collaboration 8.8.17 * Zimbra Collaboration 9.0.1 * Zimbra Collaboration 9.0.2 * Zimbra Collaboration 9.0.3 * Zimbra Collaboration 9.0.4 This issue was rated as high due to the potential for a remote attacker to execute arbitrary code on the system. CVE-2016-4238 - Unrestricted Sudo for root By default, ZCS will accept Sudo configuration from a zimbra user without any restrictions. This results
Summary
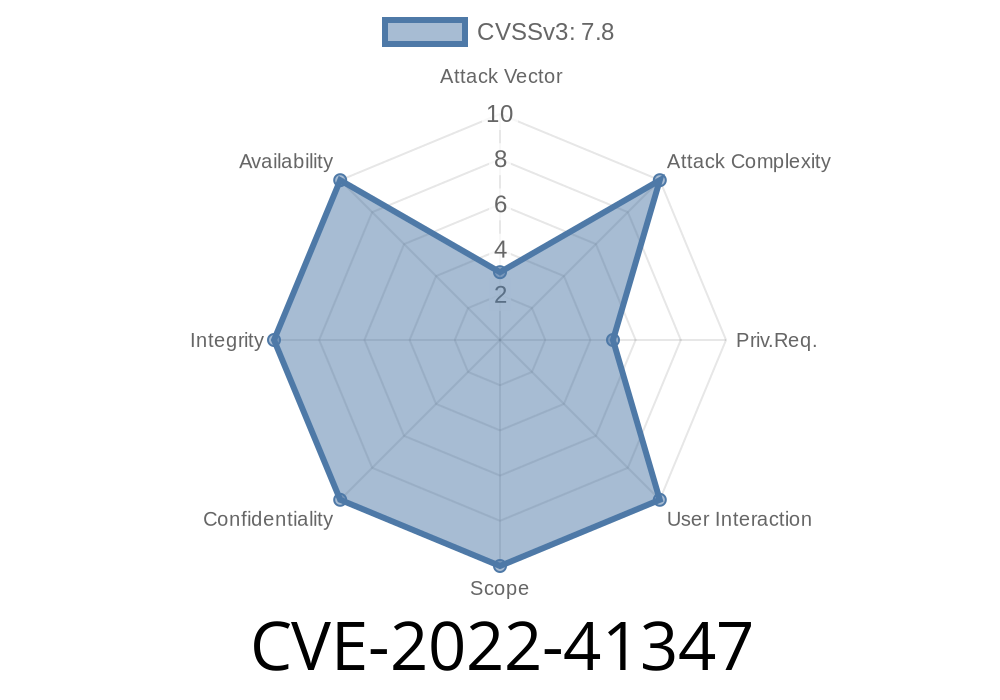
A remote attacker can escalate their privileges and execute arbitrary code on the server, leading to a compromise of the system. This issue was rated as high because of the potential for a remote attacker to escalate their privileges and execute arbitrary code on the system.
Timeline
Published on: 09/26/2022 02:15:00 UTC
Last modified on: 09/28/2022 17:04:00 UTC