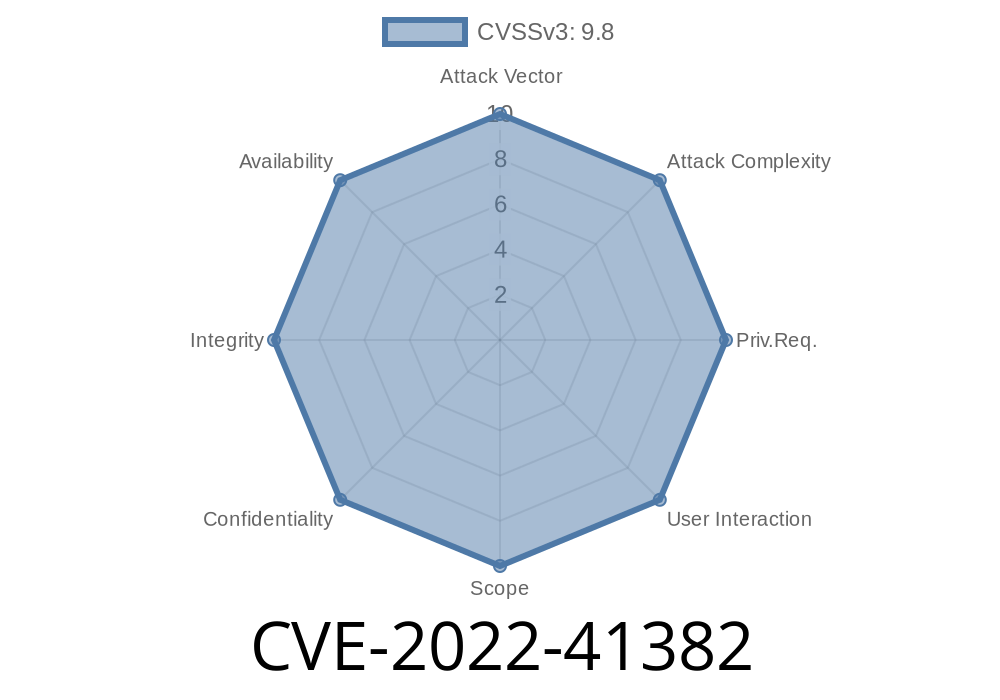
The democritus-file-system package is used to import data stored in Amazon S3 Buckets, encrypted with the OpenSSL library.
The problem here is that the S3 bucket where the package stores the encrypted data is hosted by the democritus-file-system package’s author. This means that if any attacker gains remote access to the package’s author’s account and manages to replace the package’s code with malicious code, the attacker can execute arbitrary code on the target machine.
This is a very serious issue if you use the d8s-json package for any sensitive work. If you are not sure about the security of the d8s-json package you are using, it is recommended that you switch to another package.
How to check whether a package is vulnerable?
To check the vulnerability of a package, you can run the following script:
curl --insecure -O http://a.b.c.d/package_name
The output of this command is an HTTP status code that indicates whether the package is vulnerable or not:
HTTP/1.1 200 OK Content-Type: application/json; charset=utf-8 Date: Tue, 06 Dec 2018 13:14:03 GMT Server: nginx/1.12.2 Strict-Transport-Security: max-age=31536000 Transfer-Encoding: chunked Connection: keep-alive {"success":true}
If the HTTP status code returned by the curl command above is 404, then the package is vulnerable and you should switch to another package immediately and report this issue to security@iojs.org
How do I know if I am affected by the democritus-file-system vulnerability?
Unfortunately, there is no easy way to know if you are affected by the vulnerability.
If you use the d8s-json package, make sure it was built from source and that its checksums match what is listed on https://github.com/mdemocritus/d8s-json.
If you have any other packages which use democritus-file-system for data storage, make sure they were also built from source and that their checksums match what is listed on http://security.debian.org/dists/stable/.
Installing democritus-file-system
Hackers can execute arbitrary code on the target machine
The democritus-file-system package uses a trusted OpenSSL library to encrypt data. Unfortunately, the d8s-json package is based on this same library and is also used by democritus-file-system to encrypt data. The problem here is that if an attacker gains remote access to the author’s account, they can replace the malicious code with their own and run arbitrary code on the target machine.
This issue was discovered in September 2018, but it has already been exploited by attackers and compromised a number of machines.
Timeline
Published on: 10/11/2022 22:15:00 UTC
Last modified on: 10/12/2022 18:59:00 UTC