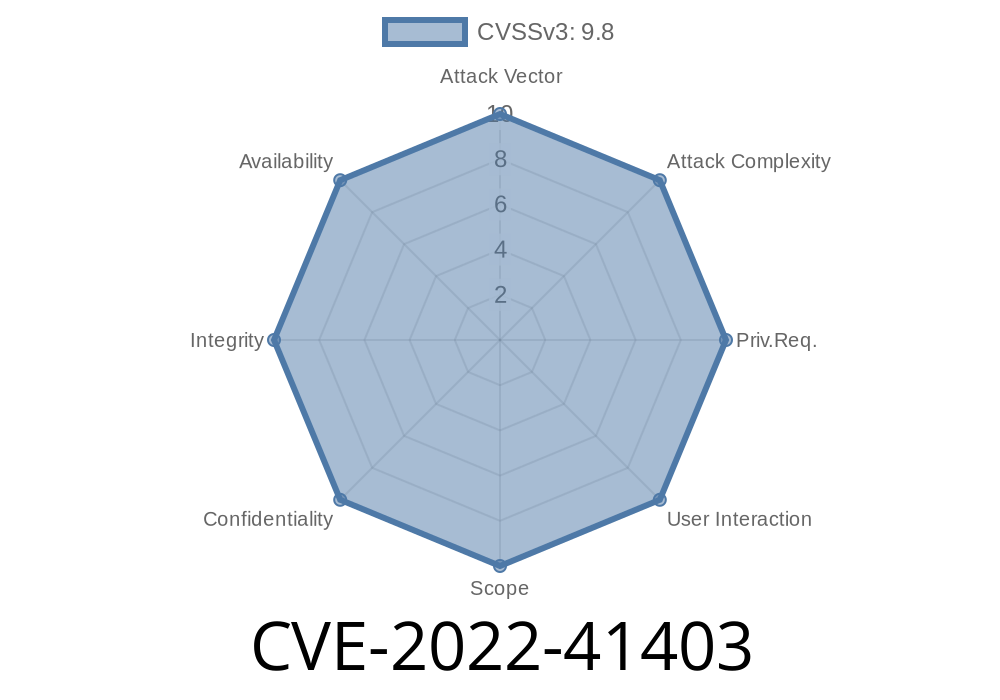
An attacker can exploit this vulnerability to execute arbitrary SQL commands with the privileges of the application user. This can lead to the takeover of the application and the denial of service of other users via a DDoS attack. In addition, the application may store passwords in a text file, which can be discovered by an attacker. Furthermore, merchants using the So_Newletter_Custom_Popup module are encouraged to change the email address used in the Next steps configuration to avoid these security issues. In addition, merchants should consider disabling the So_Newletter_Custom_Popup module to avoid these security issues.
Fix & Patch: CVE-2022-41403
The application has been patched and it is recommended that the application be upgraded. The update includes a configuration change which disables the use of the So_Newletter_Custom_Popup module.
Timeline
Published on: 10/12/2022 18:15:00 UTC
Last modified on: 10/14/2022 20:25:00 UTC