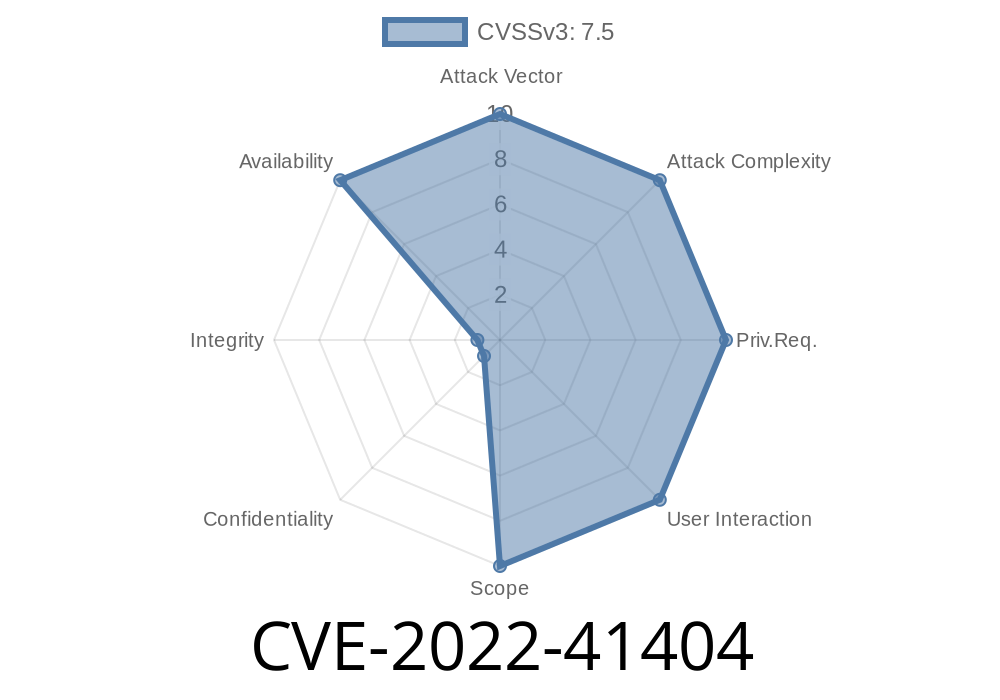
Issues have been reported in the org.ini4j.basic.fetching.Profile class in org.ini4j before v0.5.4 due to incorrect validation of user-supplied data. This can lead to unexpected behaviour when the user passes unexpected data to the constructor of the org.ini4j.basic.fetching.Profile class. A remote attacker may be able to take advantage of this vulnerability to cause a Denial of Service (DoS) via a specially crafted request to the target application. Additionally, issues have been reported in the org.ini4j.basic.fetching.Profile class of org.ini4j before v0.5.4 due to insecure handling of user-supplied data. An attacker may be able to take advantage of this vulnerability to force the user to submit unexpected data, resulting in a possible Denial of Service (DoS). Fixing these issues will improve the security of org.ini4j installations.
Mixed Content Vulnerability
A mixed content vulnerability occurs when a website loads both secure and insecure resources on the same webpage. The insecure resource could be anything from an image to a script tag. When this happens, the secure resource is made vulnerable to attack because malicious code loaded by the insecure resource can influence the execution of the request. There are two types of mixed content vulnerabilities: type 1 and type 2.
Type 1 Mixed Content Vulnerability
A type 1 mixed content vulnerability occurs when a website loads a malicious script from an untrusted source and that script contains JavaScript that performs some action in the browser that changes the content or state of any HTML element on the page. For example, if an attacker injects a malicious JavaScript file into a website, they will be able to access local files on your computer which would otherwise not be possible without first authenticating. This can result in information disclosure or even privilege escalation (e.g., if you have elevated privileges, e.g., admin, you would gain new ones).
Type 2 Mixed Content Vulnerability
A type 2 mixed content vulnerability occurs when a website loads both HTTP and HTTPS resources on the same webpage but fails to perform proper validation of each request so as to ensure that each request is sent over HTTPS only and not sent over HTTP/HTTPS combo connections. If these requests are intercepted while they are still in transit, it's very likely that attackers could hijack them and perform actions such as injecting scripts into pages or stealing confidential information from sites by
Overview
CVE-2022-41404 has been assigned to the org.ini4j.basic.fetching.Profile class in org.ini4j before v0.5.4 due to insecure handling of user-supplied data and a possible Denial of Service (DoS).
An attacker may be able to take advantage of this vulnerability to force the user to submit unexpected data, resulting in a possible Denial of Service (DoS) via a specially crafted request to the target application.
Fixing these issues will improve the security of org.ini4j installations.
Vulnerability Scenario
In order to exploit this vulnerability, a remote attacker would need to send crafted requests to the target application. A crafted request may be sent in the form of an HTTP request or a RMI TCP connection request that allows for arbitrary code execution.
Vulnerability: Incorrect Validation of User Supplied Data
A vulnerability was discovered in the org.ini4j.basic.fetching.Profile class of org.ini4j before v0.5.4 due to incorrect validation of user-supplied data when the user passes unexpected data to the constructor of the class. This can lead to unexpected behaviour when the user passes unexpected data to the constructor, possibly leading to a Denial of Service via a specially crafted request to the target application.
Issues have also been reported in this class due to insecure handling of user-supplied data where an attacker may be able to take advantage and force the user to submit unexpected data, resulting in a possible Denial of Service (DoS). Fixing these issues will improve security for org.ini4j installations.
Timeline
Published on: 10/11/2022 23:15:00 UTC
Last modified on: 11/28/2022 13:15:00 UTC