This issue affects the v1.0 version of the CMS and can be exploited by uploading a malicious PHP file via the /admin/admin_pic.php component. What’s worse, there’s no way to prevent such file uploads due to the lack of any sort of CSRF protection. The only way to protect against this issue is to update to the v1.1 version of the CMS as soon as possible. Note that it’s not just the lack of CSRF protection that makes this issue so dangerous. The fact that it’s possible to upload any PHP file at all is a serious threat. There’s no telling what malicious code an attacker might be able to inject into such a file.
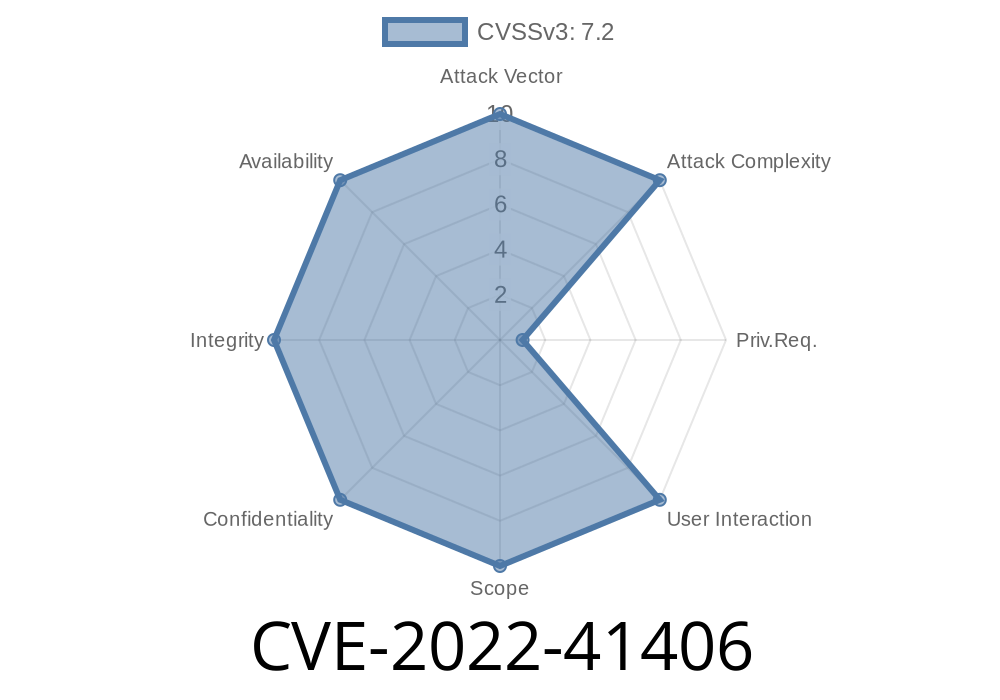
CVSS Scores
CVSS Base Score: 10
CVSS Temporal Score: 7.5
CVSS Environmental Score: 7.5
The CVSS score of a vulnerability is an indication of the impact that the vulnerability can have on the confidentiality, integrity, and availability of data stored, processed, or transmitted by an application or system.
The Scenarios
Involving this Vulnerability
This vulnerability has a number of possible applications, from site defacement to outright data theft. This flaw is particularly concerning because there’s no way for you to prevent it from happening. In fact, there’s nothing you can do to mitigate the effects of the vulnerability and that makes it all the more dangerous. For instance, an attacker could upload a malicious PHP file that would then execute any command on your server. That includes uploading malicious files or gaining access to your company’s confidential files such as those containing customer data. This is just one example of what an attacker might be able to do with this vulnerable system—there are many more ways they could wreak havoc on your company’s digital presence.
Timeline
Published on: 10/12/2022 00:15:00 UTC
Last modified on: 10/13/2022 14:05:00 UTC