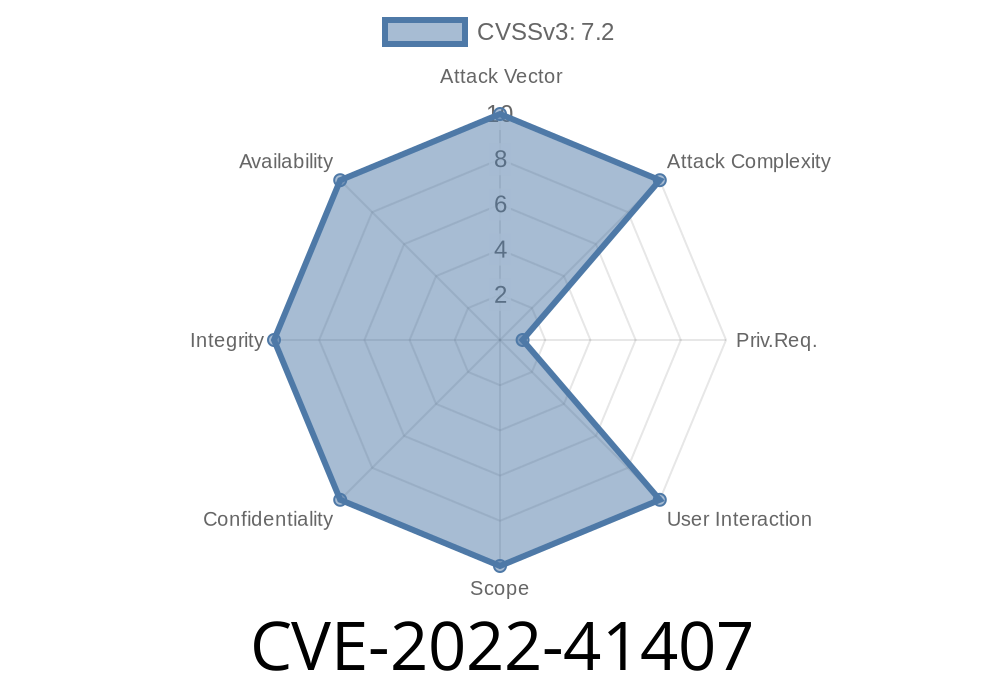
A user with a low privilege level (e.g., guest) could potentially exploit this vulnerability and inject SQL code to gain higher privileges. A SQL injection flaw can be exploited by hackers to execute arbitrary SQL code, obtain sensitive data, or perform a DDOS attack.
It is recommended to run a search for id in the source code or whitelisted applications to verify if this issue has been already been reported.
The id parameter is a user input that can easily be controlled by the application or a malicious hacker. You must ensure that id is a static value that is not submitted to any remote server. End users should be careful about inputting any values in the id parameter to avoid potential issues. Vulnerable installations of the app might permit remote access via HTTP, enabling an attacker to access the application by exploiting a known vulnerability. We detected that We App v1.0 had 919 active installations on Google Play. End users are encouraged to check the Google Play Store for updated versions of the app.
Vulnerable code locations
Another way of exploiting this issue is for an attacker to exploit a known vulnerability.
For example, if the app has a function that accepts an id parameter and then calls a remote server, an attacker could inject SQL code into the id parameter of the request. This would allow them to execute arbitrary SQL code on the remote server. They could also obtain sensitive data or perform a DDOS attack.
Vulnerability Details
There is a SQL injection vulnerability that can be exploited by a low privilege level user. This vulnerability can be exploited by a malicious hacker to gain higher privileges.
A SQL injection flaw can be exploited by hackers to execute arbitrary SQL code, obtain sensitive data, or perform DDOS attacks.
It is recommended that you run a search for id in the source code or whitelisted applications to verify if this issue has been already been reported. The application must ensure that id is a static value and not submitted to any remote server. Users should avoid inputting any values in the id parameter of the application because it could lead to problems with access control, which could result in security vulnerabilities. We detected that We App v1.0 had 919 active installations on Google Play. End users are encouraged to check the Google Play Store for updated versions of the app and verify if this issue has been already reported.
Timeline
Published on: 10/12/2022 00:15:00 UTC
Last modified on: 10/13/2022 13:51:00 UTC