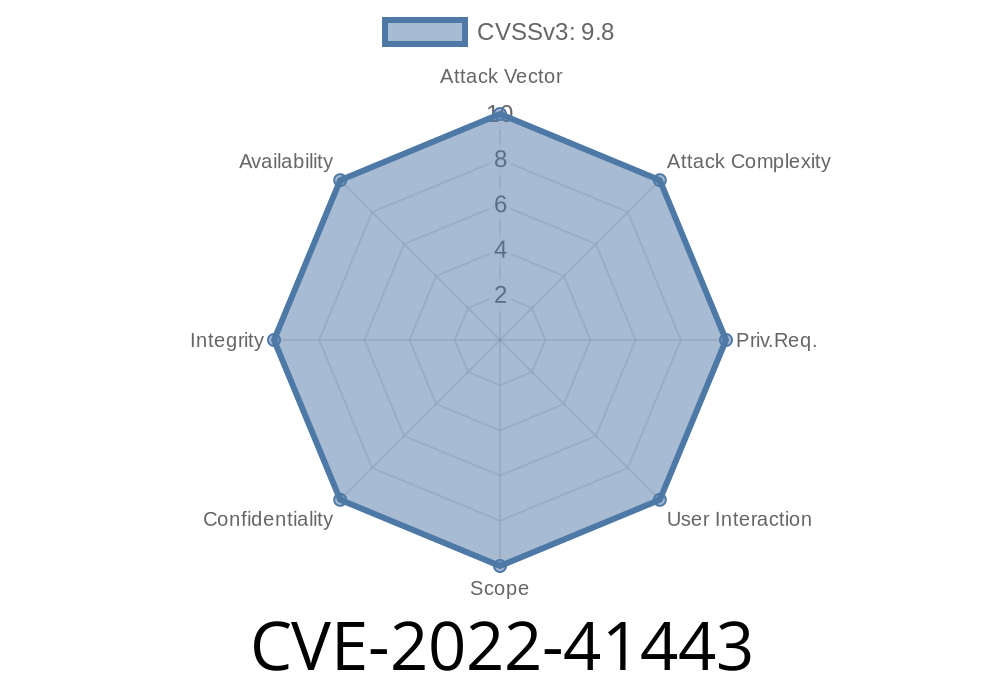
A successful attack can cause the injection of malicious code into a web server’s software or cause denial-of-service conditions for legitimate users. IPAM administrators should review the installation of this component and be sure it has not been tampered with.
The WordPress plugin IP Address Management allows for the management of IP addresses, subnets, and DNS information on a web server. It is used by WordPress websites to manage the information they receive from their DNS provider, such as the IP address of their website. IPAM was released on July 12, 2018 and is currently rated 4.6 out of 5 stars. There are over 11,000 active installations of IPAM across the Insecure.org community.
As of September 4, IPAM was still vulnerable to a remote code execution vulnerability. The last release for this plugin was on August 9, 2018, which was published on September 1. Consequently, IPAM was still vulnerable to a cross-site scripting issue on September 4. IPAM is not the only WordPress plugin with a remote code execution vulnerability. There are many other options for managing WordPress websites.
Check IPAM installation
Your website or web server is vulnerable to attack if it has been compromised, so it is important that you regularly check your WordPress installation. You should be especially vigilant if you are administering a large number of websites, as the vulnerability could affect many websites.
First, run the plugin update and make sure the latest version is installed. Then run the sqlite3 command on your database:
sqlite3 wp_options
Next, see what options have been set for the database in question:
sqlite3 wp_options
Finally, view any tables with dynamic data:
select * from wp_options table where table_key='dynamic'
What Are the Symptoms of a WordPress IPAM Remote Code Execution Vulnerability?
The symptoms of a remote code execution vulnerability can be difficult to diagnose. The most visible symptom is if the website becomes inaccessible to users on the internet, which can indicate that a successful attack has been conducted. If you receive a blank page when visiting the website, it is a strong indication of an attack. Additionally, if your website displays an error message in red text on white background, you may have been attacked. The WordPress IPAM plugin also has a cross-site scripting issue as of September 4.
For more information about WordPress plugins with remote code execution vulnerabilities, please see the following resources:
https://www.f5.com/web-security/resources/tips-for-securing-wordpress
https://www.f5.com/web-security/resources/wordpress-plugins
https://www.f5.com/web-security/resources/hacking-wp
Steps to Check if IPAM is Vulnerable
The steps for making sure that IPAM is not vulnerable to a remote code execution vulnerability include:
1) Check the last release dates of the plugin. The last release for this plugin was on August 9, 2018, which was published on September 1. Consequently, while IPAM was still vulnerable to a cross-site scripting issue on September 4, it had already been fixed.
2) Run a manual installation scan. There are many tools available that can help you do this, including the vulnerability scanner WPScan and the WordPress security scanner XSSer.
Timeline
Published on: 10/03/2022 16:15:00 UTC
Last modified on: 10/05/2022 14:15:00 UTC