An attacker can inject SQL commands that will run against the database to leak sensitive information. Remote attackers can exploit this vulnerability to execute code with elevated privileges.
An attacker can exploit this vulnerability to view unauthorized data.
An attacker can exploit this vulnerability to conduct phishing activities and gather critical information.
An attacker can exploit this vulnerability to collect network credentials.
An attacker can exploit this vulnerability to obtain access to critical data. End users should be cautious when clicking unknown links or downloading unknown files. An attacker can exploit this vulnerability to view unauthorized data.
An attacker can exploit this vulnerability to conduct phishing activities and gather critical information.
An attacker can exploit this vulnerability to collect network credentials.
An attacker can exploit this vulnerability to obtain access to critical data. End users should be cautious when clicking unknown links or downloading unknown files.
Vulnerability Details
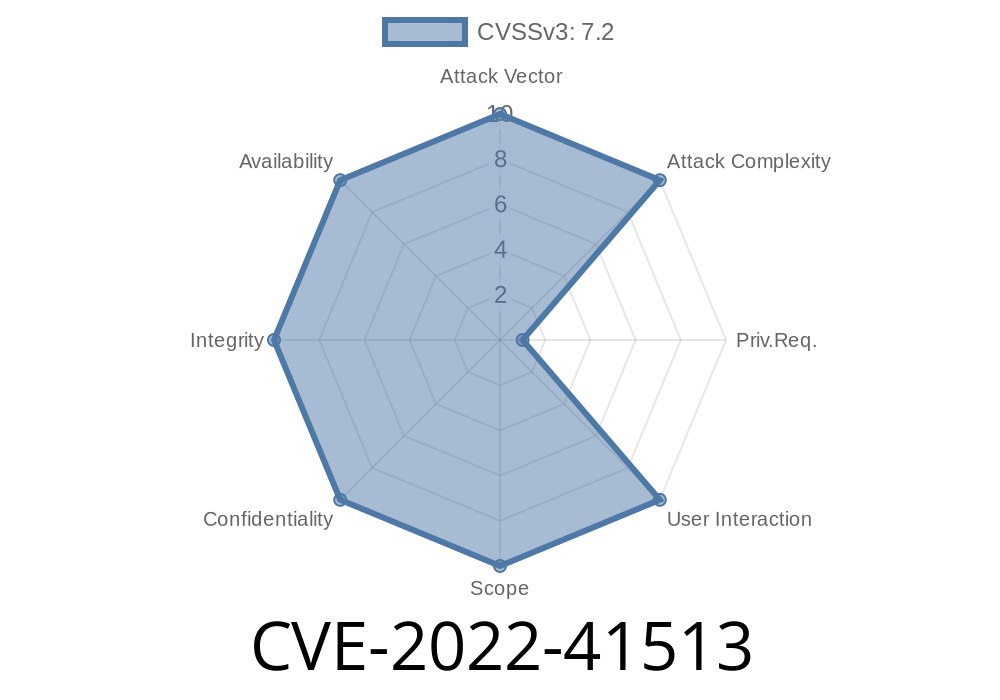
Vulnerability: CVE-2022-41513
Type: Remote Code Execution
Affected Software: SQL Server 2000, SQL Server 2005, SQL Server 2008, SQL Server 2012, Microsoft Access 2000, Microsoft Access 2003, Microsoft Access 2007, Microsoft Access 2010
Affected Systems: Client and Server
CVSSv3 Score: 9.3 (AV:N/AC:M/Au:N/C:C/I:C/A:C)
Vulnerable versions of Oracle Database
Oracle Database versions 10.2.0.5, 11.1.0.7, 12c Database 12c R2, 12c R1, and 12c R3 are vulnerable to this vulnerability.
The severity of these vulnerabilities is high as any unauthorized user could access sensitive data from the database servers remotely without needing a valid login or password for the affected systems and without requiring any user interaction to exploit these vulnerabilities.
Vulnerability Details
CVE-2022-41513 is a remote code execution vulnerability that can be exploited by an attacker who has access to the targeted system. An attacker can exploit this vulnerability to inject SQL commands that will run against the database and leak sensitive information such as user credentials, encryption keys, server configurations, and more.
Timeline
Published on: 10/07/2022 18:15:00 UTC
Last modified on: 10/09/2022 02:48:00 UTC