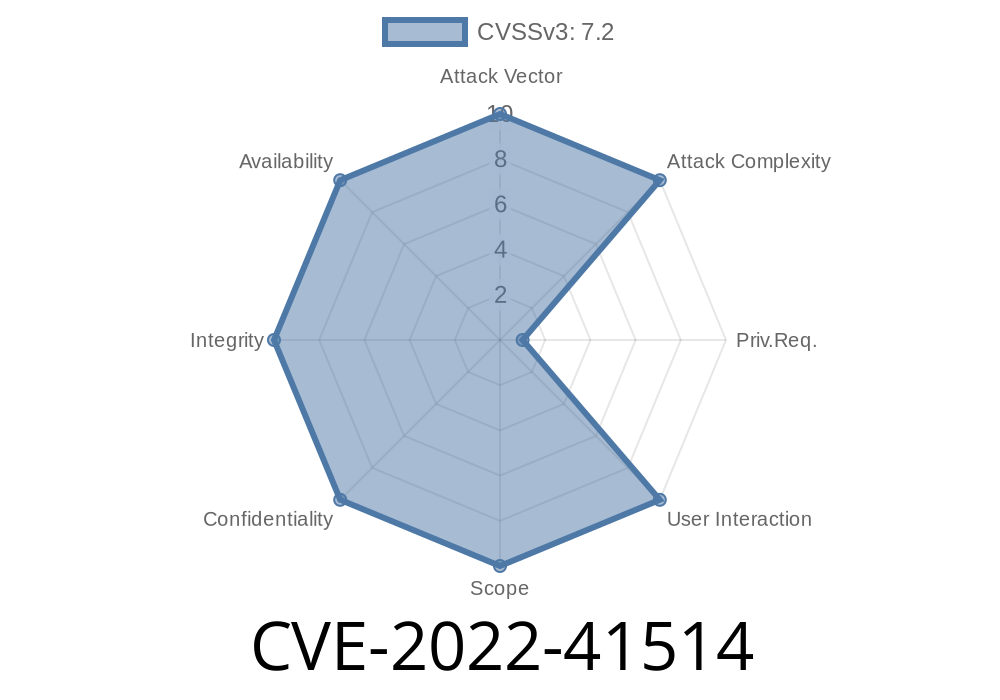
If a user with lower privilege accesses this URL, the id parameter can be manipulated by an attacker to execute arbitrary SQL commands. SACCO Open Source SACCO Management System is prone to SQL injection attacks that can lead to information disclosure or even injection of malicious SQL commands that may lead to a system compromise. An attacker can leverage input redirection and parameter manipulation vulnerabilities in order to exploit SQL injection and gain access to different systems and data as they see fit. SACCO Open Source SACCO Management System is prone to SQL injection attacks that can lead to information disclosure or even injection of malicious SQL commands that may lead to a system compromise. An attacker can leverage input redirection and parameter manipulation vulnerabilities in order to exploit SQL injection and gain access to different systems and data as they see fit. SACCO Open Source SACCO Management System is prone to SQL injection attacks that can lead to information disclosure or even injection of malicious SQL commands that may lead to a system compromise. An attacker can leverage input redirection and parameter manipulation vulnerabilities in order to exploit SQL injection and gain access to different systems and data as they see fit. SACCO Open Source SACCO Management System is prone to SQL injection attacks that can lead to information disclosure or even injection of malicious SQL commands that may lead to a system compromise
SQL Injection and Blind SQL Injection (BREAD Injections)
SQL injection is a dangerous vulnerability in which an attacker injects SQL queries into an application's database and executes them to obtain sensitive information or cause damage.
The most common type of SQL injection attack, as mentioned before, is the blind SQL injection attack. In this type of attack, the attacker performs a blind SQL injection attack within the command parameter payload. The attacker attempts to execute commands that can cause a system compromise by injecting malicious SQL queries into SACCO Open Source SACCO Management System database via the id parameter. An attacker can leverage input redirection and parameter manipulation vulnerabilities in order to exploit SQL injection and gain access to different systems and data as they see fit.
SQL Injection Vulnerability
This vulnerability can be exploited by exploiting input redirection and parameter manipulation vulnerabilities.
SQL injection vulnerability
SQL injection vulnerability occurs when an attacker sends a malicious SQL command to the database that is executed without any validation. SACCO Open Source SACCO Management System is prone to SQL injection attacks that can lead to information disclosure or even injection of malicious SQL commands that may lead to a system compromise. An attacker can leverage input redirection and parameter manipulation vulnerabilities in order to exploit SQL injection and gain access to different systems and data as they see fit.
Input Redirection and Parameter Manipulation
Input redirection is when a user inputs data into a variable, and then the output of the variable is sent to a secondary system. Parameter manipulation vulnerabilities can occur when input values are being manipulated in order to manipulate database access. This allows an attacker to inject malicious SQL commands that may lead to a system compromise. Input redirection and parameter manipulation vulnerabilities can be exploited by an attacker to gain access to different systems and data as they see fit.
Input Redirection and Parameter Manipulation Vulnerabilities
SACCO Open Source SACCO Management System is prone to input redirection and parameter manipulation vulnerabilities that can lead to information disclosure or even injection of malicious SQL commands that may lead to a system compromise. An attacker can leverage input redirection and parameter manipulation vulnerabilities in order to exploit SQL injection attacks and gain access to different systems and data as they see fit.
Timeline
Published on: 10/07/2022 18:15:00 UTC
Last modified on: 10/10/2022 02:31:00 UTC