The code of this vulnerable management endpoint is as follows.
/sacco_shield/manage_borrower.php?id=1 The id parameter is used to assign an identity to a given user. As a result, attackers can manipulate the database by injecting SQL queries that are controlled by them. In order to exploit this vulnerability, an attacker would have to send a request with a maliciously crafted id parameter. For example, an attacker can send the following request to the management endpoint. The id parameter accepts a value between 1 and 100. The attacker can choose any value between 1 and 100. The above request will be accepted by the management endpoint if the user ID is 1. However if the management endpoint is configured to accept only values from 1 to 10 then the above request will be rejected. The management endpoint is vulnerable to SQL injection because the id parameter is not properly sanitized. An attacker can send a request like the following to exploit the vulnerability. The above request will inject a malicious SQL query into the database. The malicious query will execute with the privileges of the user with ID 1.
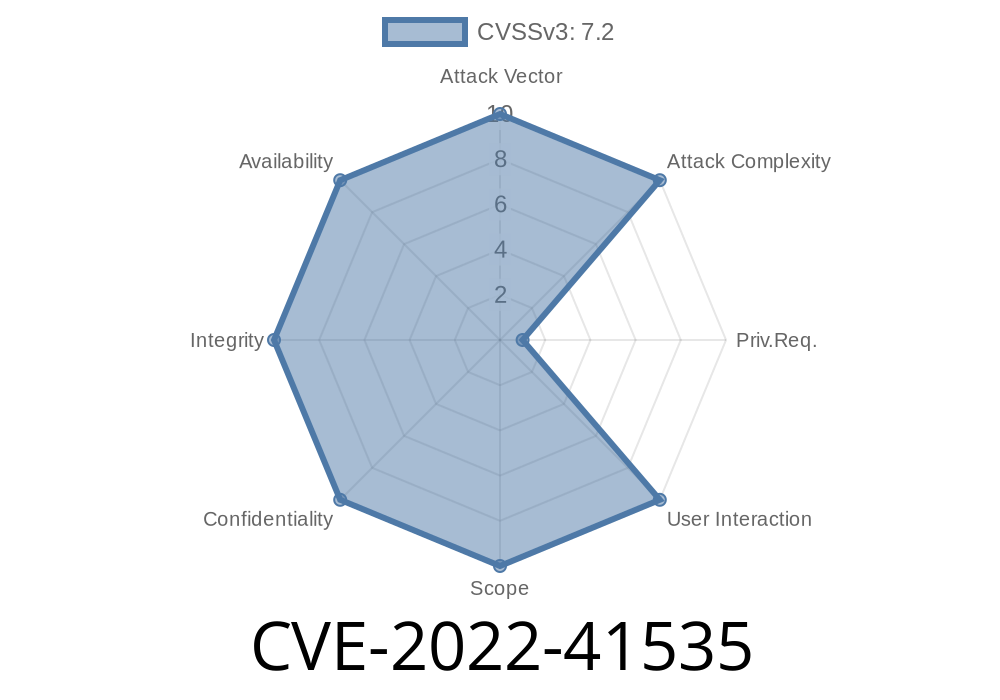
SQL Injection Vulnerability - CS
RF attack
The vulnerability exists in the management endpoint because the id parameter is not properly sanitized. The vulnerable management endpoint problem can be exploited using a cross-site request forgery (CSRF) attack. This type of attack leverages a link on your website that is used to generate an authentication token. The attacker can send you a link that, when clicked, will perform an action on your website. In this scenario, the attacker would send you a link like the following:
When you click on this link, it will generate a unique identifier for this request and submit it to the management endpoint with the value 1 inserted into the id parameter in order to exploit SQL injection vulnerabilities. If your website allows CSRF attacks then this vulnerability can be exploited by manipulating the id parameter value in order to execute malicious SQL queries with privileges of the user with ID 1.
SQL Injection Example: Borrower Management Endpoint
The management endpoint is vulnerable to SQL injection because the id parameter is not properly sanitized. An attacker can send a request like the following to exploit the vulnerability.
The above request will inject a malicious SQL query into the database. The malicious query will execute with the privileges of the user with ID 1.
SELECT * FROM borrowers where id='1';
SELECT * FROM borrowers where id='2';
The above request will execute and return information about every borrower in the system, regardless of their ID.
Timeline
Published on: 10/14/2022 06:15:00 UTC
Last modified on: 10/17/2022 16:18:00 UTC