This issue can be exploited by uploading a file with a malicious extension. An attacker can upload a PHP file with a file path like “photo.jpg” and the server will execute it. We discovered that this component had a hardcoded image path of “/Wedding-Management-PHP/admin/images/flower/flower.jpg”. This hardcoded path makes it trivial for an attacker to upload a malicious file by uploading an image with the extension “.jpg”. A hacker just needs to upload an image file with the same name as the PHP file. An attacker can easily exploit this vulnerability by uploading a PHP file with the name “photo.jpg” and the server will execute the file. We discovered that this component had a hardcoded image path of “/Wedding-Management-PHP/admin/images/flower/flower.jpg”. This hardcoded path makes it trivial for an attacker to upload a malicious file by uploading an image with the extension “.jpg”. A hacker just needs to upload an image file with the same name as the PHP file.
PHP File with a malicious extension
An attacker can exploit this vulnerability by uploading a PHP file with the name “photo.jpg” and the server will execute the file. We discovered that this component had a hardcoded image path of “/Wedding-Management-PHP/admin/images/flower/flower.jpg”. This hardcoded path makes it trivial for an attacker to upload a malicious file by uploading an image with the extension “.jpg”. A hacker just needs to upload an image file with the same name as the PHP file.
Timeline
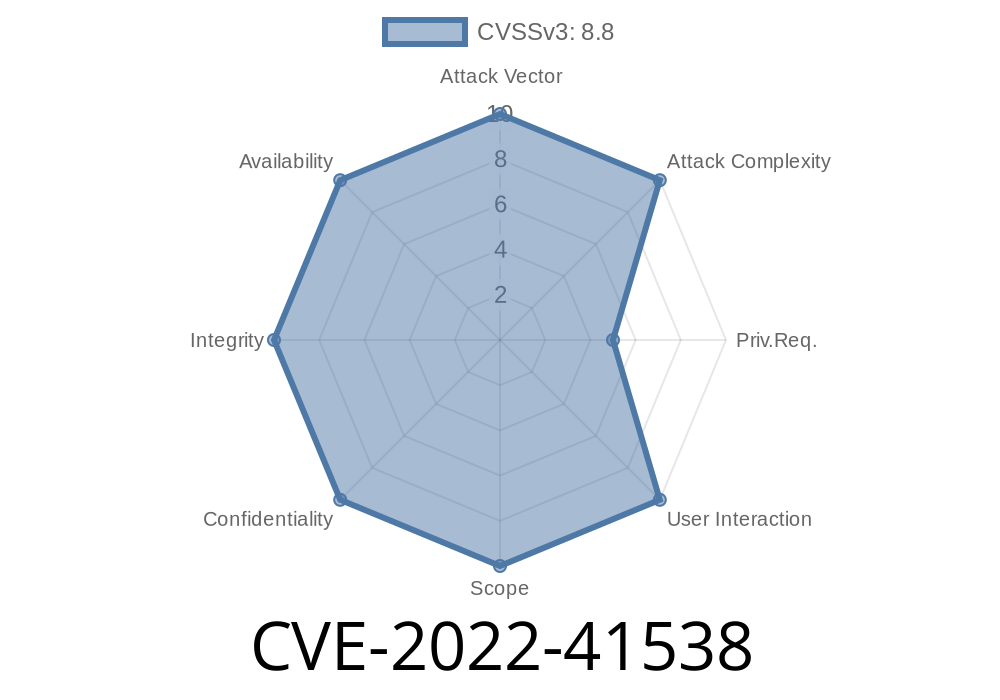
Published on: 10/14/2022 05:15:00 UTC
Last modified on: 10/17/2022 16:29:00 UTC