To exploit this issue, an attacker needs to upload a malicious PHP file to the server. After the file is uploaded, an attacker can request the file via a direct request. When the server receives the request, it will execute the code from the file, which can lead to a remote code execution.
To detect if your site is running an infected version of Wedding Planner v1.0, you can scan your site for XSS vectors or look for signs of a compromised server. If you find any, act immediately and patch your server!
END XSS VULNERABILITIES
END
Chunk Encoding HTML
Chunk encoding HTML is a method of encoding chunks of HTML within a single
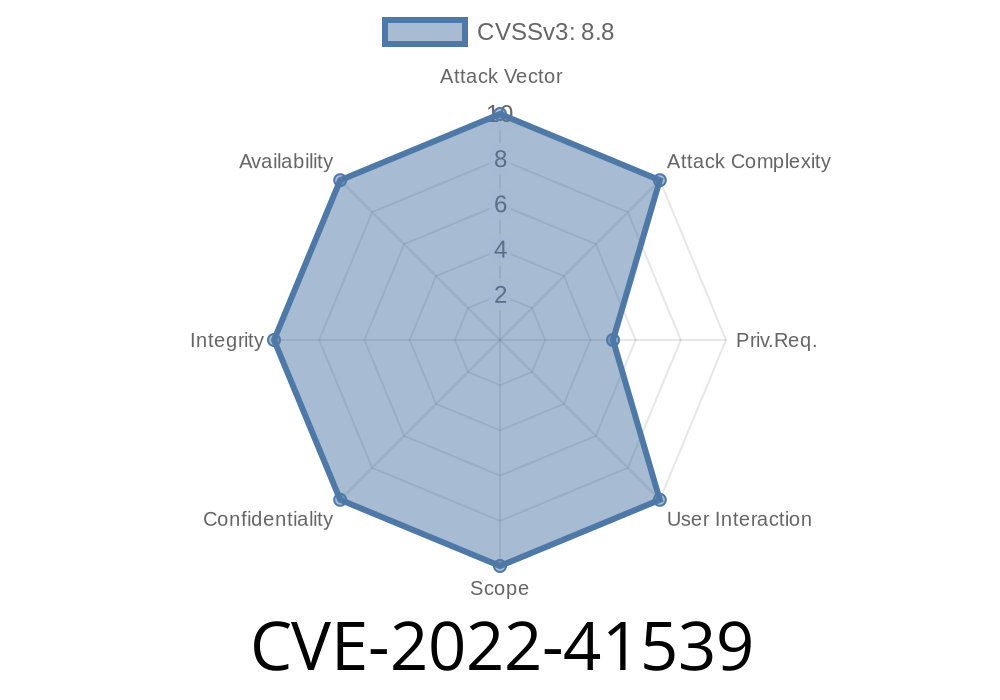
CVE-2016-5385
The vulnerability could have allowed an attacker to remotely execute code by uploading a malicious PHP file to the server. After the file was uploaded, an attacker could request it via a direct request. When the server received the request, it would execute the code from the file, which could lead to a remote code execution.
To detect if your site is running an infected version of Wedding Planner v1.0, you can scan your site for XSS vectors or look for signs of a compromised server. If you find any, act immediately and patch your server!
Insecure Direct Object References
An insecure direct object reference is a type of XSS vulnerability that occurs when an attacker is able to pass data via an HTTP request to the server. This data can then be used in an otherwise legitimate way, such as performing a SQL query or injecting HTML.
Insecure direct object references are found in two forms:
1. When the "name" attribute of the input element is set to something other than a string
2. When the "value" property on the input element is set to anything other than "false"
How Wedding Planner Site Is Being Attacked?
To exploit this issue, an attacker needs to upload a malicious PHP file to the server. After the file is uploaded, an attacker can request the file via a direct request. When the server receives the request, it will execute the code from the file, which can lead to a remote code execution.
Installation of Web Application Firewall (WAF)
You can install a web application firewall (WAF) to block direct requests from your website. By setting up a WAF, you'll be able to detect the malicious request for the PHP file and take action before the file is uploaded.
Timeline
Published on: 10/14/2022 05:15:00 UTC
Last modified on: 10/17/2022 16:32:00 UTC