Exploitation of this vulnerability requires user space to send a specially crafted network packet to a vulnerable system. The user network interface (e.g. a remote access router) is configured to forward traffic to the target device with a specially crafted packet. This allows a remote attacker to exploit the vulnerability in the kernel.
The vulnerability was reported to Red Hat by an anonymous researcher earlier this month. Red Hat confirmed the existence of the issue and a fix is expected to be released in the upcoming Red Hat Enterprise Linux 6.5. Red Hat Enterprise Linux is the commercial version of Red Hat Linux and is usually updated every six months. Red Hat Enterprise Linux 5 is currently the longest supported version with support ending on May 31, 2021. Red Hat Enterprise Linux 6 was released in March and is expected to be supported through May 2021. The complete list of Red Hat Enterprise Linux supported releases can be found here.
Description
The vulnerability is remotely exploitable in the kernel. Red Hat Enterprise Linux 6.5 and later releases will have a fix for this issue.
What to do if you are running a version of Linux prior to 6.4
If you are running an affected version of Linux, update to the latest available version.
The vulnerability can be mitigated by disabling or removing the network interface used to send the packets to the target device in the configuration file.
Common Vulnerabilities and Exposures
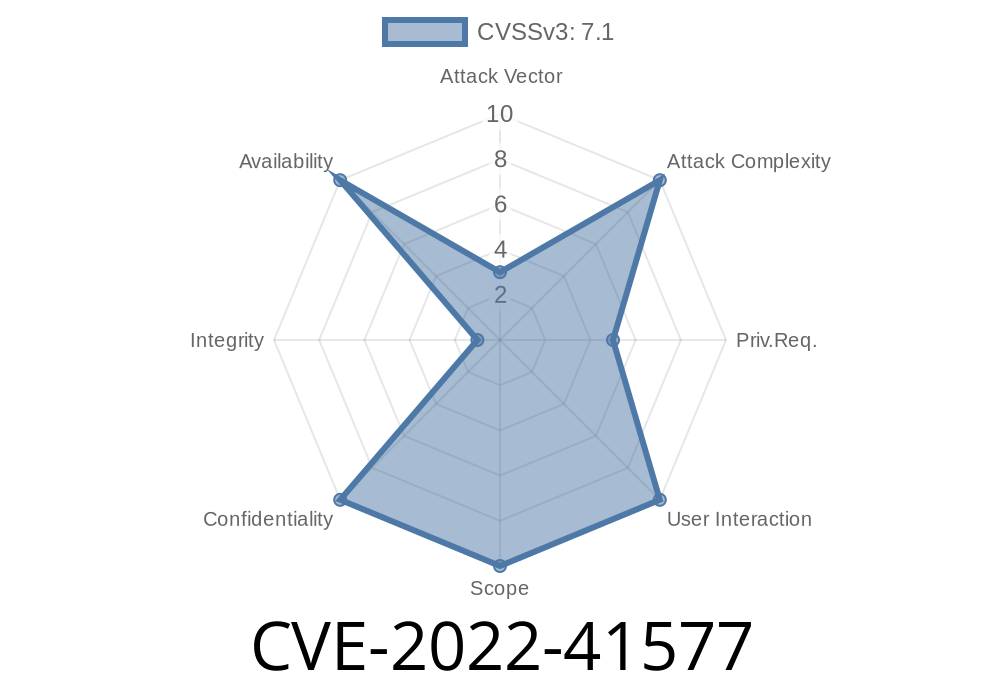
CVE-2022-41577 is a vulnerability in the kernel that has been confirmed by Red Hat. In this particular case, a remote attacker could exploit the vulnerability in the kernel of an affected system. The issue was reported to Red Hat by an anonymous researcher earlier this month but it was confirmed on May 18th.
Exploitation of this vulnerability requires user space to send a specially crafted network packet to a vulnerable system. The user network interface (e.g. a remote access router) is configured to forward traffic to the target device with a specially crafted packet. This allows a remote attacker to exploit the vulnerability in the kernel.
Check if you are affected by the vulnerability
If you are not running Red Hat Enterprise Linux 5.9 or later, then you are not affected by this vulnerability.
If you are running Red Hat Enterprise Linux 6, please check your release notes for more information on when the patch will be available. Please note that the fix does not apply to earlier versions of Red Hat Enterprise Linux such as 6.4 and 6.3 and must be installed through the updated channel.
How to check if you are vulnerable?
Systems running Red Hat Enterprise Linux 5 should check the following registry key to see if they are vulnerable:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\tcpip6
If the value named “AllowPathMatching” is set to 0, then your system is not vulnerable. If the value is set to 1, you are vulnerable.
Timeline
Published on: 10/14/2022 16:15:00 UTC
Last modified on: 10/15/2022 01:51:00 UTC