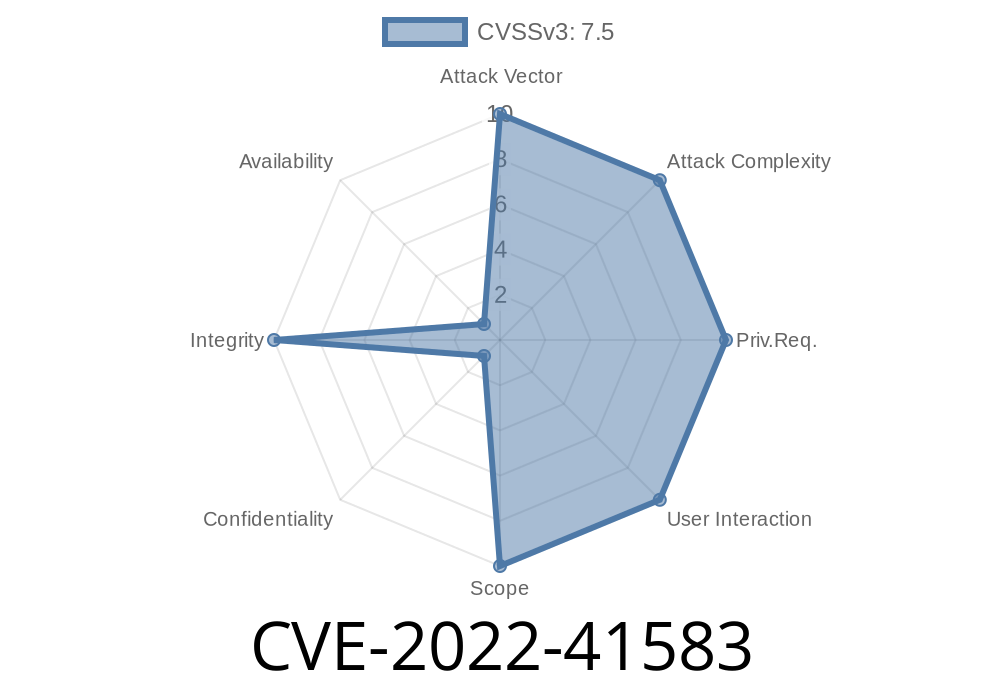
This issue can be exploited by an unauthenticated attacker, who can send specially crafted requests to the targeted Apache HTTP Server, system. This issue can be exploited by an unauthenticated attacker, who can send specially crafted requests to the targeted Apache HTTP Server, system. This can be done by an attacker seeking to monitor the functioning of the targeted Apache HTTP Server, system. Vulnerable versions: Apache HTTP Server: versions prior to 1.3.19, 1.4.19, 1.5.x, 1.6.x, and 1.7.x. Apache Storage Maintenance and Debugging: all versions. The storage maintenance and debugging module has a SQL injection vulnerability. Successful exploitation of this vulnerability will allow an attacker to inject arbitrary SQL statements into the targeted database, system. Vulnerable versions: Apache HTTP Server: versions prior to 1.3.19, 1.4.19, 1.5.x, 1.6.x, and 1.7.x. The storage maintenance and debugging module has a SQL injection vulnerability. Successful exploitation of this vulnerability will allow an attacker to inject arbitrary SQL statements into the targeted database, system. Vulnerable versions: Apache HTTP Server: versions prior to 1.3.19, 1.4.19, 1.5.x, 1.6.x, and 1.7.x. Apache Storage Maintenance and Debugging: all versions. The storage maintenance and debugging module has a SQL injection vulnerability
What is Apache Software and How to Detect if it’s Vulnerable?
Apache is an open-source Web server software which can run on a large number of Unix, Linux and Windows systems. It is the most popular Web server software in the world, used by more than 70% of all Web servers.
Apache Software is one of the most popular open-source Web server software. It's the most widely deployed and one of the most powerful web servers in use today. The Apache Software Foundation (ASF), a non-profit corporation based in Boston, Massachusetts, develops and maintains Apache Software. The ASF also provides support for Apache Software via its website, mailing lists, IRC channels and other services.
A vulnerability in Apache can be exploited by an unauthenticated attacker to gain access to system privileges by sending specially crafted requests to the targeted Apache HTTP Server, system. This issue can be exploited by an unauthenticated attacker, who can send specially crafted requests to the targeted Apache HTTP Server, system. This can be done by an attacker seeking to monitor the functioning of the targeted Apache HTTP Server, system. Vulnerable versions: Apache HTTP Server: versions prior to 1.3.19, 1.4.19, 1.5x and 1.6x; all versions of Storage Maintenance and Debugging module are vulnerable
Apache HTTP Server - Improper Restriction of File Operations
The Apache HTTP Server is affected by an improper restriction of file operations. This issue can be exploited by anyone sending specially crafted requests to the targeted Apache HTTP Server, system. This issue can be exploited by an unauthenticated attacker, who can send specially crafted requests to the targeted Apache HTTP Server, system. This issue can be exploited by an unauthenticated attacker, who can send specially crafted requests to the targeted Apache HTTP Server, system. This issue is due to improperly implemented restrictions of file operations. Vulnerable versions: Apache HTTP Server: versions prior to 1.3.19, 1.4.19, 1.5.x, 1.6.x, and 1.7.x
Research Notes
** The Apache HTTP Server is prone to a SQL injection vulnerability **
Successful exploitation of this vulnerability will allow an attacker to inject arbitrary SQL statements into the targeted database, system.
Timeline
Published on: 10/14/2022 16:15:00 UTC
Last modified on: 10/18/2022 17:27:00 UTC