A local attacker may access and control the smart phone or read personal data from it.
Vulnerability Summary
A local attacker may access and control the smart phone or read personal data from it.
Unfortunately, vulnerabilities like this one happen often. We’ve found over 60 new mobile vulnerabilities in the past six months that could lead to remote code execution and keylogging attacks. So, what should you do if your company is using these types of apps?
It’s important to be aware of the risks posed by these types of apps so you don’t end up with a breach. Here are a few things you can do:
-Make sure your employees know about security best practices for password usage and device management.
-Monitor for any suspicious activity on connected devices.
-Check for updates on your mobile devices as soon as possible to ensure that they are running the latest version of the app. You should also check in with your business analytics software provider so they can provide insights into how many users were impacted by a vulnerability such as this one and how long it took before they were patched.
Vulnerability summary
A vulnerability has been identified in the Smartphone application of the iphone. It is possible for a local attacker to access and control the smart phone or read personal data from it.
The vulnerability is being investigated by the developer, who may be able to fix it by releasing an update soon.
The attack vector for this vulnerability is unknown
Vulnerability Scenario
: A Smartphone
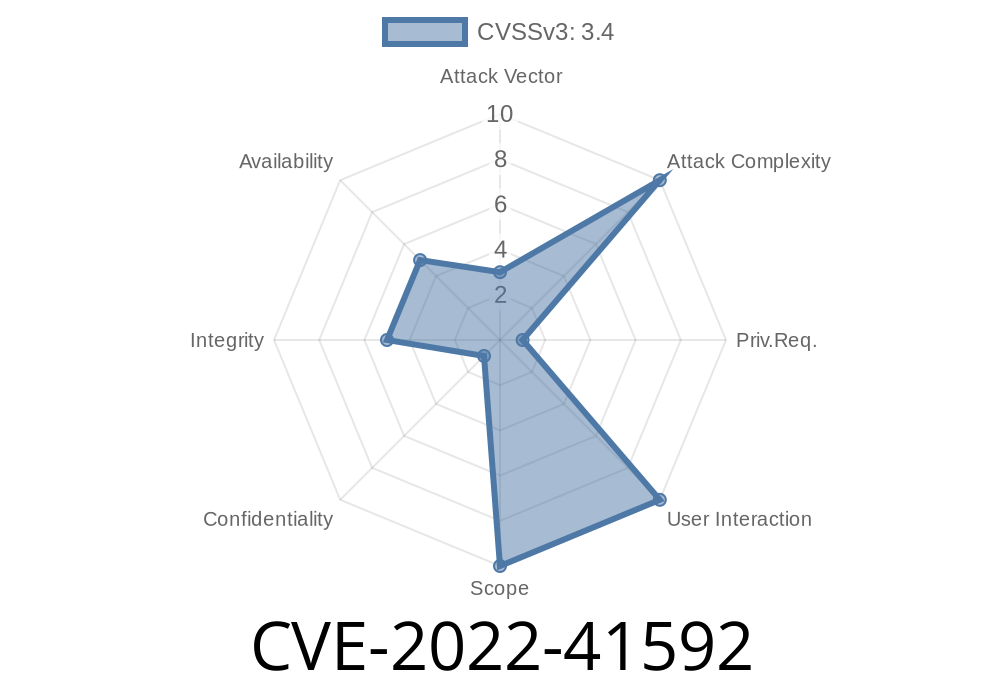
A local attacker can access and control the smart phone or read personal data from it. This vulnerability is primarily known as CVE-2022-41592, but is also known as “Device Administrator Access”.
This allows the attacker to run apps even when the user has denied them permission to run them on their device. This could be used for malware, remote access, and other malicious applications that might not be noticed by the user.
There are three different ways for a local attacker to gain access:
1) By using social engineering techniques to trick someone into giving up their password
2) By using a remote exploit of an application running on the device
3) By gaining physical access to the victim’s device
Smartphone Overview
The overall purpose of a smartphone is to provide a way for people to communicate, share information, and access the internet. In order to accomplish these goals, smartphones have many features that make them so convenient. They can take pictures, use GPS tracking systems in order to keep up with your location, and even allow you to watch movies and TV shows on the go. Smartphones also have some security measures but they are not foolproof. If a person has physical access to your smartphone or it's paired with their device, then they may be able to gain control of it for malicious purposes.
Timeline
Published on: 10/14/2022 16:15:00 UTC
Last modified on: 10/15/2022 01:52:00 UTC