A local attacker may access and control the smart phone or read personal data from it.
Smart Phone Components Affected by the Vulnerability
The vulnerability affects the Common Messaging Service on the Smart Phone which is a contact list, email, and SMS client. This service is not used to communicate with the server and can be accessed without authentication in case of a local attack.
The vulnerability also affects the Smart Phone’s location services and Wi-Fi connection settings.
Overview
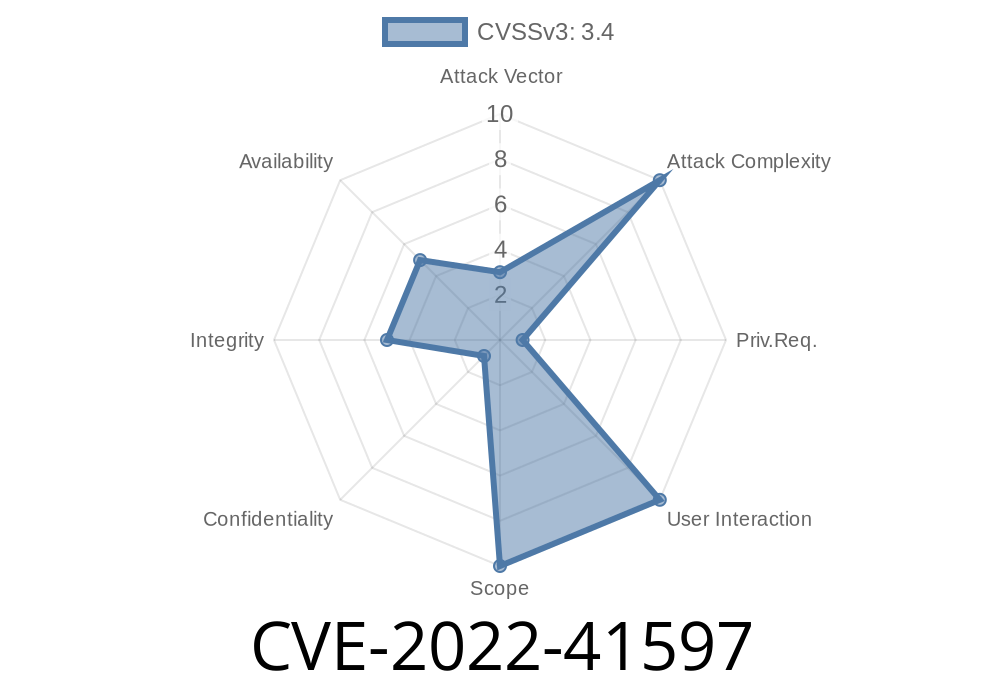
The CVE-2022-41597 vulnerability allows a local attacker to access and control the smart phone or read personal data from it. The vulnerability is in the Bluetooth stack of Android's firmware.
Even older versions of Android are vulnerable to this vulnerability. To exploit this vulnerability an attacker must be within Bluetooth range of the target device.
Vulnerability Scenario
A local attacker has the ability to gain access and control over the smart phone of an individual or read personal data from it. This vulnerability is possible because the information stored on a smart phone includes personal data.
The following subheading is for a blog post about how to outsource SEO correctly and avoid the 5 most common mistakes:
Why Outsourcing SEO Can Be a Good Idea
- Designing an effective SEO strategy isn’t a simple task. Companies have to consider how search engines are evaluating the content, what aspects of SEO offer the most impact, and where they could change their current content to better align with search engine expectations. This is especially critical as search engines like Google continually refine their ranking process. For example, page loading speed is now a factor in search result rankings. In practice, this expands the role of SEO; it’s not enough to simply weave in popular keywords and deliver high-quality content. Brands also need to consider the entire user experience. As a result, it’s often worth outsourcing SEO services to ensure that your digital presence is generating maximum impact and capturing the highest volume of prospective customers.
Vulnerabilities of Smart Phone
Data security is an important issue for any business and every smart phone user. Because of the decentralized nature of smart phone technology, a local attacker can access and control the device, which means they may also access personal data on it or read information from it.
In many countries, people are using their phones to make purchases. In fact, in 2018 that number was projected to increase by 8 percent. With this in mind, businesses should take the appropriate steps to secure their data and avoid data breaches like these. If a business wants to ensure their customers’ privacy and data security, they should consider implementing tight security measures with encryption software like PGP.
Timeline
Published on: 10/14/2022 16:15:00 UTC
Last modified on: 10/15/2022 01:55:00 UTC