Find and avoid these data leak risks at all costs. These are the major cause of data leakage that can lead to sensitive data exposure and data theft. While conducting a thorough code audit, you will come across many of these data leak risks. The most critical of them are as follows: 1. Improper validation – The most common data leak risk happens due to improper validation. When a field is not properly validated, it means that the data entered in that field is not validated against any rule or standard.
Improper User Input Validation
This data leak risk happens when your application receives user input that is not properly validated. If a person inputs an email address and the email they enter doesn’t exist, then you will have a user input with no validation.
2. Improperly escaped user input – This data leak is caused by unescaped data in the form of HTML or XML. If you allow users to type their own HTML or XML, this may lead to XSS vulnerabilities. The most common attack that occurs through this vulnerability is the injection of malware into your website.
3. Cloud Computing & Data Storage
While using cloud computing, you should be careful about where your data is stored and for how long it will stay there. You want to make sure that your data stays there for as short as possible so that it isn’t exposed to any malicious activity from hackers or other entities who are trying to access it even after you delete it from your system. 4. Default values – You should always monitor default values in order to avoid any potential attacks against your system and its security policies by attackers who exploit standard methods of exploiting default values within the system to obtain sensitive information such as: username & password, credit card numbers, social security numbers, etc..
5. Unprivileged Users – With each implementation of a new feature or service within an application, new users may be added without proper verification. When this happens, these users can view unauthorized files and folders on your system which can contain
Improper Validation – The most common data leak risk
2. Unencrypted Data – Data that is not encrypted is a common data leak risk and can also lead to data theft because it's easier to steal.
3. Vulnerable APIs – The vulnerability of an API is the result of a poorly written or misconfigured code and can cause sensitive data exposure.
4. Lack of Logging and Monitoring – Logging and monitoring are the last line of defense for your application, and they should be used in conjunction with other measures to mitigate risk and prevent data leak risks.
If any of these become evident during your code audit, make sure you perform extra research on how to remedy them so as not to expose any sensitive data without proper authorization.
Improperly formed Input Validation
One of the most common data leak risks is not properly formed input validation.
Most of the time, input validation is more than enough to protect sensitive information from being exposed to the internet. If a field requires a number, then any text entered in that field should be checked against a regular expression. This type of validation ensures that text entered into fields does not contain numbers, spaces, or other characters that are invalid for the field.
All fields that require input validation need to have this validation implemented with proper syntax so that there are no vulnerabilities when entering personal data such as credit card numbers or social security numbers.
Improper validation - The most common data leak risk
The second most common data leak risk is due to improper validation. When a field is not properly validated, it means that the data entered in that field is not validated against any rule or standard. For example, let's say you have a form requesting blog post title. The user types in something like 'a quick SEO tip for WordPress' in the website name field, but then the website automatically registers blog posts with this title as their own and creates a new one. The blog post will show up on your blog and in search engine results pages (SERPs), but your original article will be lost.
Another way improper validation can happen is if someone logs into your system using an email address belonging to someone else. Let's say you've invited friends to test out your service for free, but each person needs to log in by keying their email address into the account settings page. If their email address isn't specified exactly as they entered it – which is quite common – then they'll be able to sign up for your service using another person's account information.
Improper sanitation – The other common data leak risk is that of improper sanitation
. When a field is not properly sanitized, it means that the data entered in that field does not have any checks and/or filters applied to prevent input of viruses and malware.
2. Logical errors – The other common data leak risk is that of logical errors. When a logic error happens, it means that the software logic used to process data has been broken or mismanaged. These risks are often due to improper coding or improper handling of inputs on databases.
3. Security weaknesses – If a security weakness exists in an application, it means that the application fails to adopt best practices or standard security measures such as password strength requirements, enforced encryption, and secured connections.
4. SQL injection – SQL injection is a type of exploit in which malicious code is inserted into an SQL database query by circumventing the intended target servers' security measures via exploiting design flaws in their applications programming interfaces (APIs). It's one of the most common methods for hackers to penetrate web pages and extract information about users without their consent.
5. Outdated software – An application using outdated software can be vulnerable to hacking because the software is old enough that patches have been applied by vendors but it still runs on outdated hardware without support for newer hardware features like new CPUs or network cards for better performance.
6. Improperly configured permissions – In some cases, poorly configured permissions can lead to improper function calls with some privileges being denied and others being granted more than what they should be allowed to
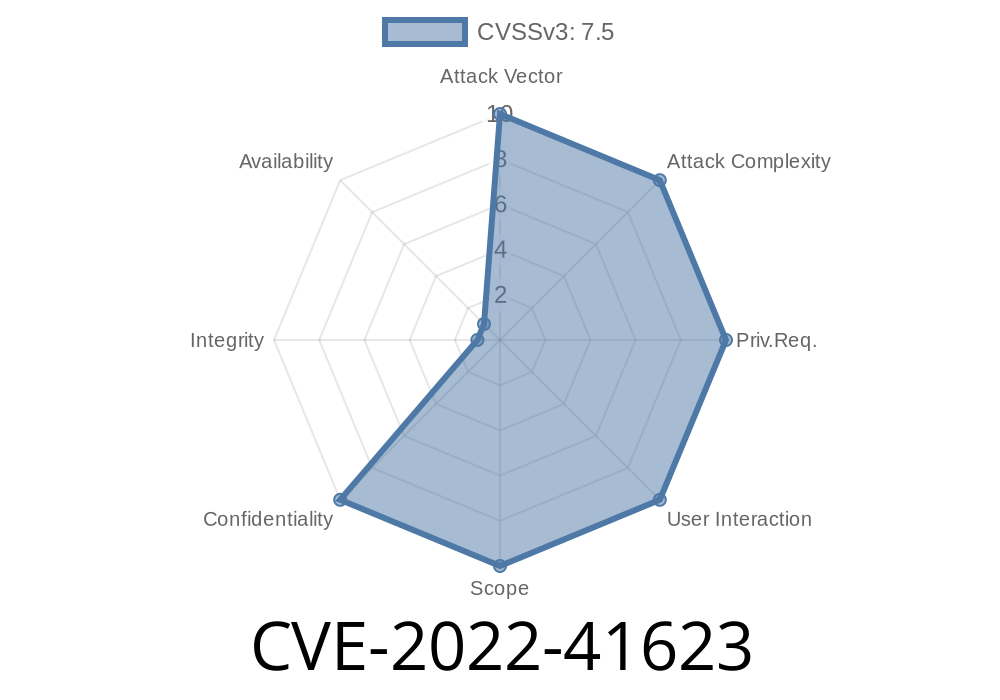
Timeline
Published on: 10/14/2022 20:15:00 UTC
Last modified on: 10/18/2022 18:42:00 UTC
References
- https://patchstack.com/database/vulnerability/woocommerce-alidropship/wordpress-ald-aliexpress-dropshipping-and-fulfillment-for-woocommerce-plugin-1-1-0-sensitive-data-exposure?_s_id=cve
- https://villatheme.com/extensions/aliexpress-dropshipping-and-fulfillment-for-woocommerce/#tab-changelog
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-41623