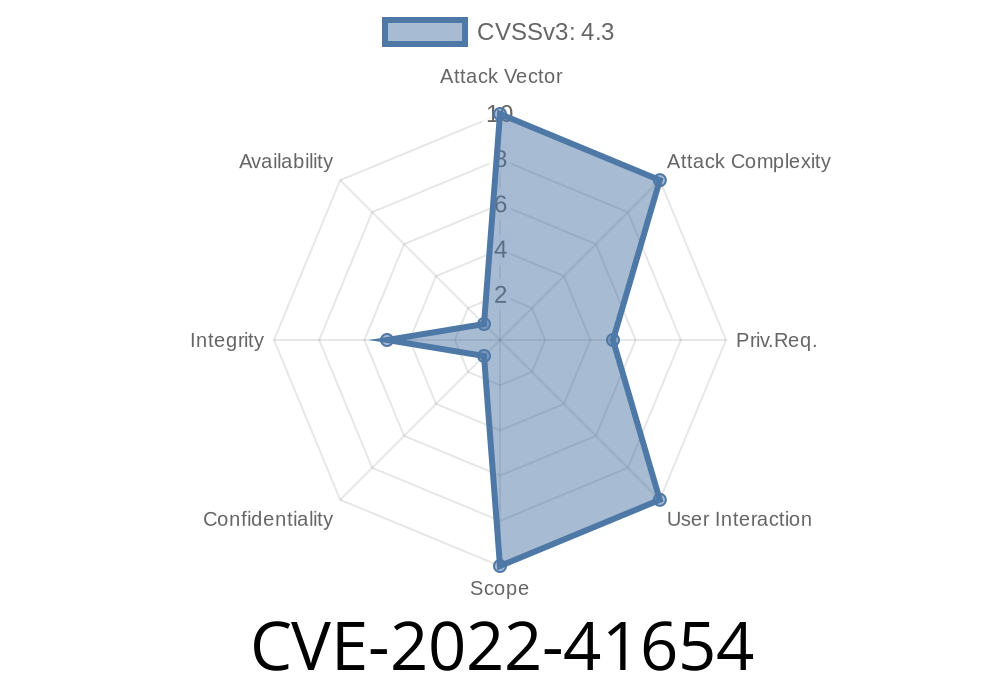
Ghost Foundation Ghost 5.9.4 is vulnerable to cross-site request forgery (CSRF) due to insecure usage of HTTP requests. A hacker can easily perform a CSRF attack against Ghost Foundation Ghost 5.9.4.
An authorization bypass vulnerability exists in the function that allows a user to create a new newsletter on Ghost Foundation Ghost 5.9.4. An attacker can exploit this vulnerability and take over any account on Ghost Foundation Ghost 5.9.4.
An information disclosure vulnerability exists in the function that allows a user to view his/her newsletter on Ghost Foundation Ghost 5.9.4. A hacker can exploit this vulnerability and get access to any account on Ghost Foundation Ghost 5.9.4. End users are advised to update to the latest version 5.9.4 of Ghost Foundation Ghost 5.9.4. Stay alert for the latest news about new software vulnerabilities.
CSRF Attack on Ghost Foundation Ghost 5.9.4
Cross-site request forgery (CSRF) is a type of computer security vulnerability that occurs when an attacker tricks a user into performing an unwanted action on a web application hosted on another domain without their knowledge. CSRF attacks are dangerous because they allow the attacker to perform any unauthorized action on the user's behalf, such as transferring funds, changing account settings, or deleting content. A hacker can easily perform a CSRF attack against Ghost Foundation Ghost 5.9.4 by sending the victim a malicious link via email or social media that prompts him/her to authenticate using his/her credentials on another web application like Twitter or Facebook.
CSRF Protection for Mailboxes
CSRF attacks are one of the most common vulnerabilities in software. Ghost Foundation Ghost 5.9.4 has built-in CSRF protection that safeguards against this attack.
When you fill out a form on your account and submit it, the system will send a cookie back to the server with a token that identifies your account as having submitted that form, making it difficult for an attacker to impersonate you and submit malicious forms.
You can disable cookies for mobile devices or use an alternative browser (such as Incognito) to avoid this attack altogether.
Timeline
Published on: 12/22/2022 10:15:00 UTC
Last modified on: 12/29/2022 20:33:00 UTC