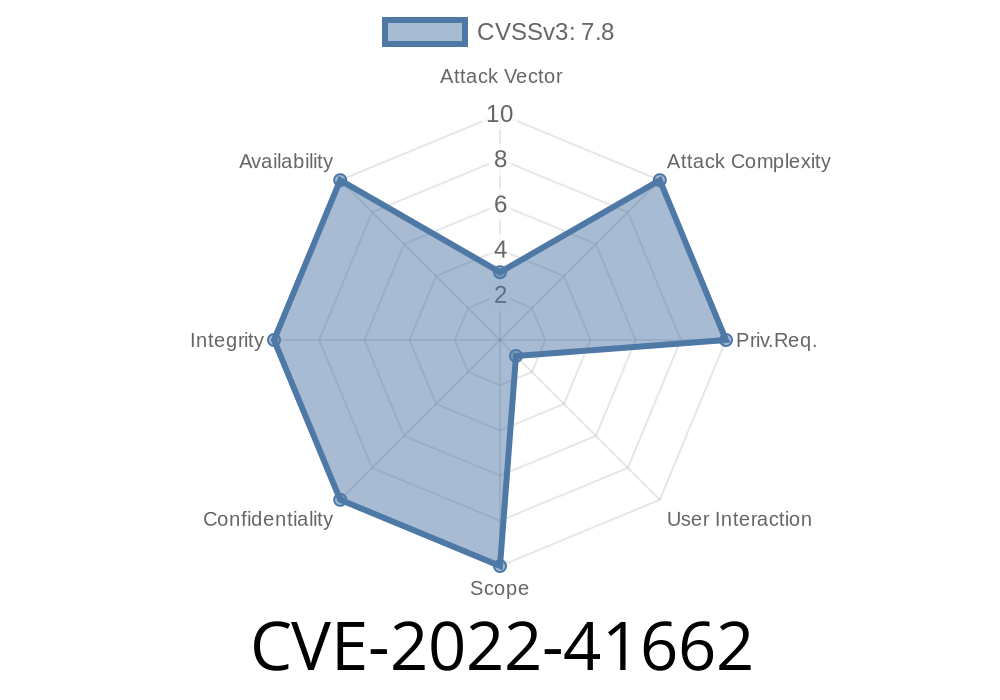
In October 2022, Siemens disclosed a critical vulnerability affecting several of its widely used industrial visualization tools – JT2Go and Teamcenter Visualization. Tracked as CVE-2022-41662, this bug lets attackers exploit how these programs process Computer Graphics Metafile (CGM) files.
For engineering, manufacturing, and PLM engineers worldwide, JT2Go and Teamcenter Visualization are essential for viewing complex 3D models. Unfortunately, before the appropriate update, all supported and unsupported versions below:
Teamcenter Visualization V14.1: all versions less than V14.1..4
were vulnerable to a carefully crafted attack file.
Understanding the Vulnerability
At the heart of CVE-2022-41662 is an *out-of-bounds read* when parsing certain CGM files. Attackers can supply a malicious CGM that tricks the application into reading memory it shouldn't. This can lead to information leakage – or, under the right conditions, even enable code execution in the context of the user running the application.
Why is this dangerous? Because in many corporate and industrial networks, these applications are run by users with high privileges, and because file-based attacks are hard to spot: all you have to do is *open the wrong file*.
Reference:
- Siemens advisory: SSA-211140: Vulnerabilities in JT2Go and Teamcenter Visualization
- National Vulnerability Database: CVE-2022-41662
Technical Details
The core issue results from how the software reads and processes certain data structures within CGM files. Let’s take a simplified look at how such a bug sometimes looks in C/C++:
void parse_cgm_record(uint8_t* data, size_t length) {
size_t offset = ;
while (offset < length) {
uint16_t record_length = *(uint16_t*)(data + offset);
offset += 2;
// Vulnerable: No bounds check on record_length vs data size!
memcpy(processing_buffer, data + offset, record_length);
offset += record_length;
}
}
If record_length is controlled by the file, and is larger than what remains in the buffer, the function can read past allocated memory -- that's a classic *out-of-bounds read*. With tweaks, an attacker can sometimes control what’s “spilled,” leaking memory or setting up a code-reuse exploit.
CGM File Structure Manipulation
In proof-of-concept tests, researchers showed that CGM files could have record headers with artificially large length fields. When the visualization app attempts to parse it, no check is made to ensure the length stays within the buffer. This can be abused to read unintended memory, sometimes containing sensitive process information or even to trigger more serious bugs (like out-of-bounds writes).
Attacker crafts a malicious CGM file with a manipulated record length or other header fields.
2. The file is delivered (via email, a download, or shared workspace) to a victim in a manufacturing, engineering, or PLM environment.
Example malicious file snippet (pseudo-binary)
[Header...] [Fake length: xFFFFFF] [Payload....]
When the application reads this, it may attempt to process far more data than what's actually present, triggering the vulnerability.
Proof of Concept (PoC)
While a complete working PoC isn’t public due to responsible disclosure, here's a demonstration in Python for crafting a malformed CGM record:
with open("evil.cgm", "wb") as f:
f.write(b'\x00\xFF') # Valid CGM file header bytes
# Craft record: Type, Length (huge), Data (short)
f.write(b'\x01') # Record type byte
f.write((b'\xFF\xFF').ljust(2, b'\x00')) # Faked xFFFF record length
f.write(b'A' * 10) # Not enough data for declared length!
Opening "evil.cgm" with a vulnerable Siemens viewer would cause it to read way past the ten A bytes, potentially leading to memory access issues.
Teamcenter Visualization V14.1: Update to V14.1..4 or newer
➡️ Download official patched versions here
In addition, avoid opening CGM files from untrusted sources, and use Windows file permissions to limit what the application can access.
Final Thoughts
CVE-2022-41662 is a serious bug illustrating the dangers in trusting complex file formats. Even tools meant for viewing or converting files can hide deep vulnerabilities, and attackers know corporate users are less suspicious of files from colleagues, partners, or even customers.
If you use Siemens JT2Go or Teamcenter Visualization, check your version and upgrade immediately. If you’re responsible for enterprise security, roll out the patches and notify your PLM teams. And, as always, be careful with files from unknown sources.
More Resources
- Siemens CERT Security Advisory SSA-211140
- NVD: CVE-2022-41662
- JT2Go Downloads
- Teamcenter Visualization Product Page
Stay safe, update your tools, and always treat files—even “just viewers”—with care!
Timeline
Published on: 11/08/2022 11:15:00 UTC
Last modified on: 11/08/2022 16:29:00 UTC