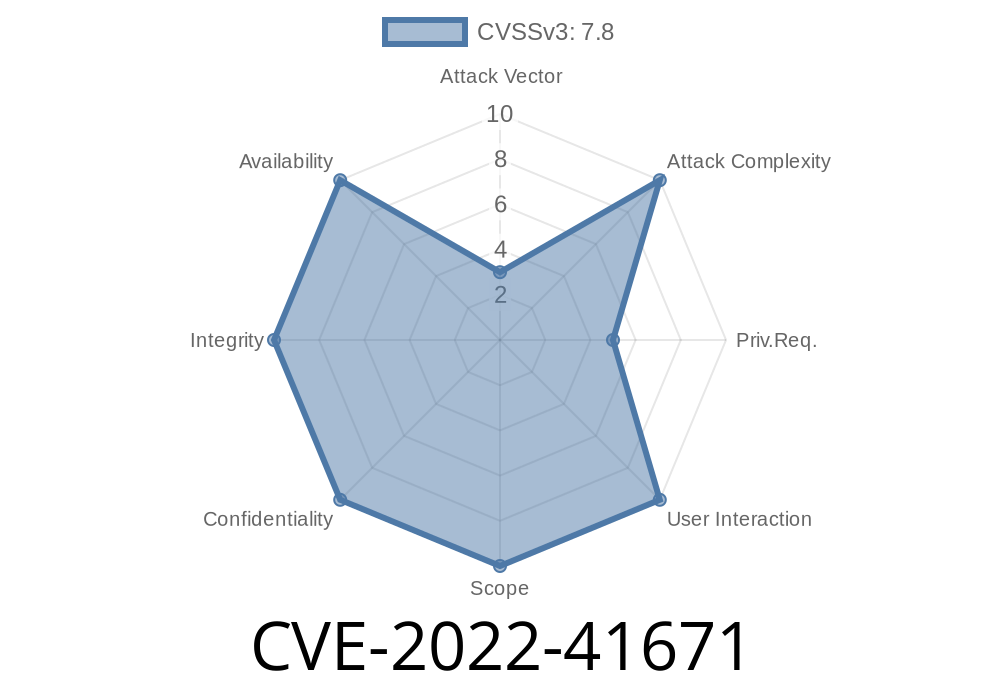
Risk: Remote Code Execution. Exploitation of this vulnerability is possible if user inputs an SQL command that has special characters of the ‘injection’ type into the database. No user interaction is required to exploit this vulnerability. When this SQL injection issue is present in the database then any user can inject malicious SQL code into database and get executed on the database server. This SQL injection issue is common in most of the database software. What are some of the famous database software that suffer from this issue? - MSSQL, MySQL, Oracle and other. What are the typical ways to exploit this SQL injection issue? - User-friendly web interface hacker can simply access the database server via any vulnerable web interface and inject the SQL code to get malicious code executed on the database server. - Another common way to exploite this SQL injection issue is via command-line interface (CLI) of the database server. A perfect example of how to exploit this issue via CLI is by running the following query “select * from users”. This query will return all the data of the users table from the database. What are the typical ways to exploit this SQL injection issue? - User-friendly web interface hacker can simply access the database server via any vulnerable web interface and inject the SQL code to get malicious code executed on the database server
MSSQL
, MySQL, Oracle and other suffer from this vulnerability
The vulnerability is common in most of the database software. What are some of the database software that suffer from this issue? - MSSQL, MySQL, Oracle and other. What are the typical ways to exploit this SQL injection issue? - User-friendly web interface hacker can simply access the database server via any vulnerable web interface and inject the SQL code to get malicious code executed on the database server. - Another common way to exploit this SQL injection issue is via command-line interface (CLI) of the database server. A perfect example of how to exploit this issue via CLI is by running the following query “select * from users”. This query will return all the data of the users table from the database. What are some of the ways to protect yourself against these vulnerabilities? - Use a firewall that blocks requests for any ports not listed in your Web site security configuration; or you may use a proxy server such as Squid which inspects outgoing data for signs of abuse before sending it on its way over your network.
Timeline
Published on: 11/04/2022 15:15:00 UTC
Last modified on: 11/08/2022 16:21:00 UTC