In some instances, an attacker may be able to perform these actions even if they are not logged into the Apex One web console. Trend Micro recommends that users take the following precautions to ensure that attackers cannot exploit this vulnerability. Restrict access to the affected installation to only authorized users.
Disable the web-based management interface by setting the following registry value to prevent unprivileged users from accessing the management interface: HKEY_LOCAL_MACHINE\SOFTWARE\Trend Micro\Antivirus - Value: Enabled - Type: DWORD - Data: 0x00000001 Incorporate two-factor authentication, if possible, in order to increase the difficulty of an attacker’s task.
Restrict access to the affected installation to only trusted networks.
Disable the web-based management interface by setting the following registry value to prevent unprivileged users from accessing the management interface: HKEY_LOCAL_MACHINE\SOFTWARE\Trend Micro\Antivirus - Value: Enabled - Type: DWORD - Data: 0x00000001 These steps will help ensure that attackers cannot exploit this vulnerability.
Vulnerability Details
A vulnerability has been identified which may allow for an attacker to take control of the web console by using a specially crafted URL. This vulnerability poses a risk as attackers are able to perform certain actions even if they are not logged into the Apex One web console.
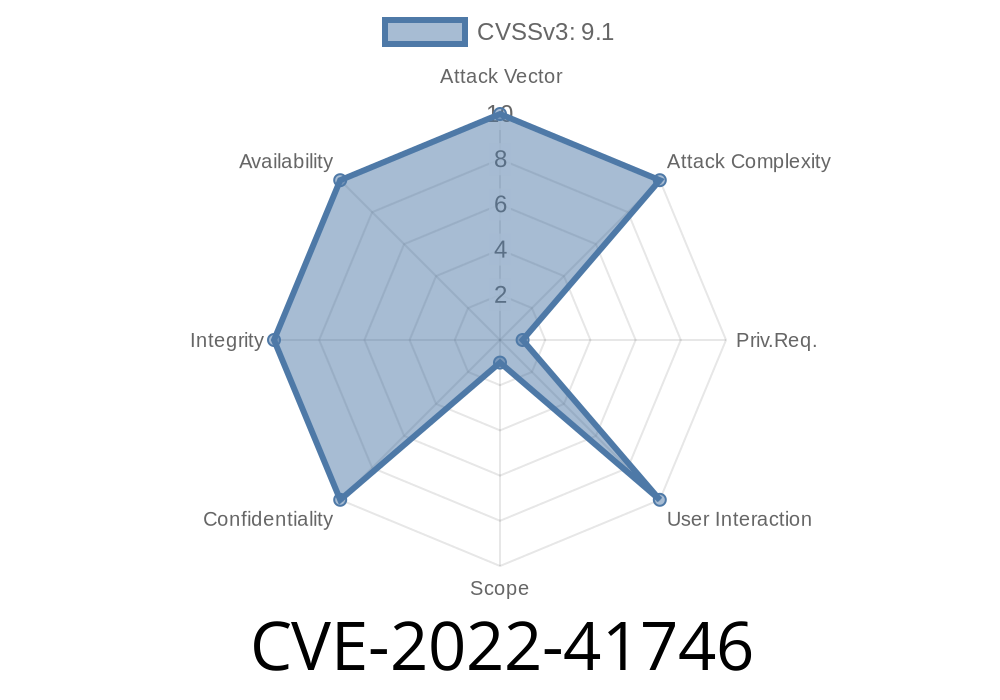
Vulnerability: CVE-2022-41746
Description: In some instances, an attacker may be able to perform these actions even if they are not logged into the Apex One web console. Trend Micro recommends that users take the following precautions to ensure that attackers cannot exploit this vulnerability. Restrict access to the affected installation to only authorized users.
Impact Level: High
Mitigation Technique: Restrict access to the affected installation to only authorized users. Disable the web-based management interface by setting the following registry value to prevent unprivileged users from accessing the management interface: HKEY_LOCAL_MACHINE\SOFTWARE\Trend Micro\Antivirus - Value: Enabled - Type: DWORD - Data: 0x00000001 Incorporate two-factor authentication, if possible, in order to increase the difficulty of an attacker’s task. Restrict access to the affected installation to only trusted networks. Disable the web-based management interface by setting the following registry value to prevent unprivileged users from accessing the management interface: HKEY_LOCAL_MACHINE\SOFTWARE\Trend Micro\Antivirus - Value: Enabled - Type: DWORD -
Dependencies for this vulnerability
The following are the dependencies for this vulnerability:
- This vulnerability requires that the web interface is enabled and accessible from any location on the network.
Timeline
Published on: 10/10/2022 21:15:00 UTC
Last modified on: 10/11/2022 19:55:00 UTC